Newly Launched - AI Presentation Maker

AI PPT Maker
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
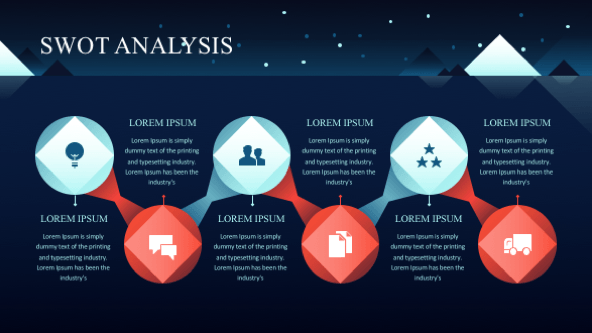
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories


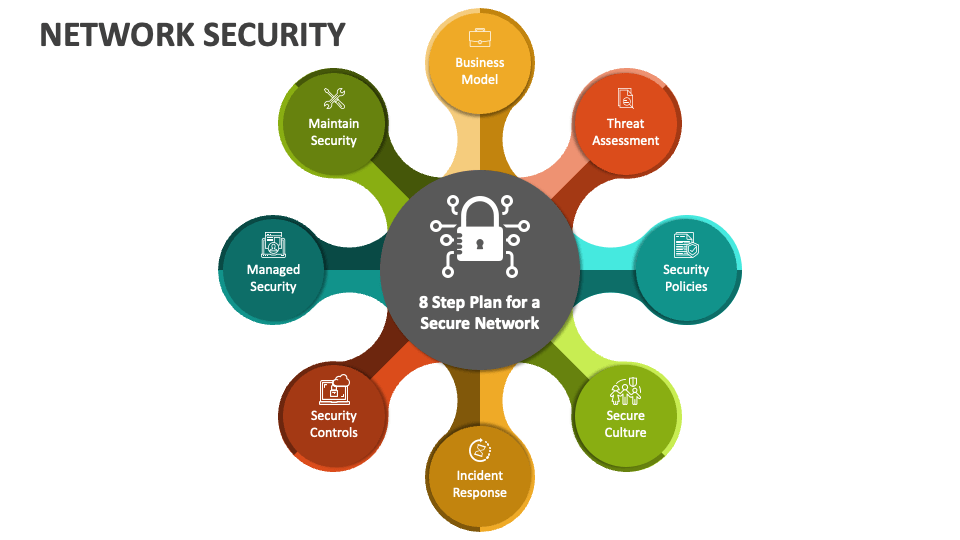
Network security powerpoint presentation slides
Network Security protects electronic devices such as computers, servers, mobile gadgets, data, electronic systems, and networks from network attacks. This PowerPoint presentation illustrates important details about network security. This network security PowerPoint presentation will be helpful to throw light on the current scenario of the organization, the requirement of network security in different sectors, and its work. In addition, computer security PPT contains the critical elements of network security, network risk identification, and assessment, steps to mitigate those risks, benefits of network security, and automations role in network security. Further, this data security presentation comes with a checklist to implement network security in the organization, a 30-60-90-day plan to manage network security, and the budget to implement the same. The Information Security deck also showcases a roadmap to monitor network security and a timeline to implement network security in the organization. Lastly, this electronic information security PPT shows the effects of network security implementation on the organization and dashboard for threat tracking in network security. Get access now.

- Add a user to your subscription for free
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Network Security Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of eighty one slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

People who downloaded this PowerPoint presentation also viewed the following :
- Complete Decks , All Decks , IT
- Information Security ,
- Data security ,
- Computer Security ,
- Network Security ,
- Electronic Information Security ,
- Information Technology Security
Content of this Powerpoint Presentation
Slide 1 : This slide introduces Network Security. State Your Company Name and begin. Slide 2 : This is an Agenda slide. State your agendas here. Slide 3 : This slide shows Table of Contents for Network Security. Slide 4 : This is another slide continuing Table of Contents for Network Security. Slide 5 : This slide highlights title for topics that are to be covered next in the template. Slide 6 : This slide defines the meaning of Network security and how it helps to prevent data through different methods and techniques. Slide 7 : This slide shows Requirement of Network Security in Different Sectors. Slide 8 : This slide highlights title for topics that are to be covered next in the template. Slide 9 : This slide shows the organization's current situation through the total losses experienced because of different cyberattacks. Slide 10 : This slide displays Highest Number of Malware Attacks in Departments. Slide 11 : This slide shows Cyber Attacks Experienced by Company in Previous Financial Year. Slide 12 : This slide highlights title for topics that are to be covered next in the template. Slide 13 : This slide represents the different elements of Network security such as application security, network security, information security, etc. Slide 14 : This slide defines application security and categories of application threats and tools to perform application security. Slide 15 : This slide displays Elements of Network Security – Information Security. Slide 16 : This slide represents the main principles of information security such as confidentiality, integrity, and availability. Slide 17 : This slide represents the network security element of Network security and different network security methods. Slide 18 : This slide presents Elements of Network Security – Disaster Recovery Planning. Slide 19 : This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. Slide 20 : This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, etc. Slide 21 : This slide defines the operational security element of Network security. Slide 22 : This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, etc. Slide 23 : This slide presents the end-user education within the Network security model. Slide 24 : This slide shows Elements of Network Security – Cloud Security. Slide 25 : This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, etc. Slide 26 : This slide shows Security Framework in Cloud Computing. Slide 27 : This slide highlights title for topics that are to be covered next in the template. Slide 28 : This slide presents the main types of threats in Network security, such as cybercrime, cyber terrorism, etc. Slide 29 : This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, etc. Slide 30 : This slide displays Common Methods Used to Threaten Network-Security. Slide 31 : This slide highlights title for topics that are to be covered next in the template. Slide 32 : This slide depicts the cyberattacks surface based on different property types. Slide 33 : This slide presents Cyber Threat Landscape in Data Security. Slide 34 : This slide highlights title for topics that are to be covered next in the template. Slide 35 : This slide depicts the importance of cyber risk management strategy and procedures. Slide 36 : This slide shows Cyber Safety Tips - Protection Against Cyberattacks. Slide 37 : This slide highlights title for topics that are to be covered next in the template. Slide 38 : This slide presents the different benefits of deploying a Network security model in an organization. Slide 39 : This slide depicts the cyber protection of an organization through artificial intelligence. Slide 40 : This slide displays Complete Network Security Implementation Checklist. Slide 41 : This slide highlights title for topics that are to be covered next in the template. Slide 42 : This slide represents the Network security awareness training program for staff, including the name of the participants. Slide 43 : This slide presents Hardware and Software Update in Company. Slide 44 : This slide depicts the benefits of using antivirus software in the organization. Slide 45 : This slide displays the importance of having strong passwords for different online accounts. Slide 46 : This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Slide 47 : This slide displays Prepare Data Backup for Sensitive Information. Slide 48 : This slide depicts what factors will be considered while preparing a recovery planning of an organization. Slide 49 : This slide represents the value of having strong IT policies within an organization. Slide 50 : This slide depicts secure communication within an organization and the technology to encrypt emails. Slide 51 : This slide displays the importance of disposal of the data and equipment that is not in use anymore. Slide 52 : This slide depicts that the security of employees’ hardware or devices is also essential while applying the cyber security model. Slide 53 : This slide presents Define Access Control Measures for Employees. Slide 54 : This slide highlights title for topics that are to be covered next in the template. Slide 55 : This slide depicts how the Network security model will work in the first 30 days and the tasks the organization should focus on. Slide 56 : This slide represents the plan for 60 days after implementing the Network security model in the organization. Slide 57 : This slide depicts the 90 days plan of the Network security model in an organization and training compliance. Slide 58 : This slide highlights title for topics that are to be covered next in the template. Slide 59 : This slide represents the budget for IT infrastructure after implementing data security. Slide 60 : This slide displays the organization's staff training budget through a graph covering trainer name, date, and capability levels. Slide 61 : This slide highlights title for topics that are to be covered next in the template. Slide 62 : This slide displays Timeline for the Implementation of Network Security. Slide 63 : This slide depicts the Network security training roadmap. Slide 64 : This slide highlights title for topics that are to be covered next in the template. Slide 65 : This slide displays Impact on Organization After Implementing Network Security Strategy and Training. Slide 66 : This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Slide 67 : This slide highlights title for topics that are to be covered next in the template. Slide 68 : This slide presents Dashboard for Threat Tracking in Network Security. Slide 69 : This slide depicts the Network security compliance report on how data and hardware are monitored in different categories. Slide 70 : This slide showcases Icons for Network Security. Slide 71 : This slide is titled as Additional Slides for moving forward. Slide 72 : This slide provides 30 60 90 Days Plan with text boxes. Slide 73 : This is Our Mission slide with related imagery and text. Slide 74 : This slide presents Roadmap with additional textboxes. Slide 75 : This is a Timeline slide. Show data related to time intervals here. Slide 76 : This slide shows Post It Notes. Post your important notes here. Slide 77 : This is a Comparison slide to state comparison between commodities, entities etc. Slide 78 : This slide presents Bar chart with two products comparison. Slide 79 : This is a Financial slide. Show your finance related stuff here. Slide 80 : This slide contains Puzzle with related icons and text. Slide 81 : This is a Thank You slide with address, contact numbers and email address.
Network security powerpoint presentation slides with all 86 slides:
Use our Network Security Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.

Network security refers to the set of methods, techniques, and technologies that an organization uses to secure its computer network infrastructure from unauthorized access, misuse, modification, or destruction. It is crucial because it protects sensitive and confidential data, prevents network downtime, and ensures business continuity by mitigating cyber threats, attacks, and vulnerabilities.
The four main elements of network security are application security, information security, network security, and operational security. Application security ensures the protection of applications and software from threats. Information security deals with securing confidential and sensitive data. Network security aims to protect the network infrastructure and devices from unauthorized access. Operational security ensures that the security protocols and procedures are followed correctly to mitigate cyber threats.
Recent threats to network security include malware, phishing, ransomware, and social engineering attacks. These threats are continuously evolving and becoming more sophisticated. Attackers are using advanced techniques to bypass security measures and exploit vulnerabilities.
Organizations can prevent network security threats by implementing security best practices, such as using strong passwords, regularly updating software and hardware, deploying anti-malware and anti-virus software, and providing regular security awareness training to employees. Additionally, using multi-factor authentication, implementing access control measures, and conducting regular vulnerability assessments can also help prevent network security threats.
The benefits of deploying a network security model in an organization include protecting sensitive data and intellectual property, mitigating cyber risks and threats, ensuring business continuity, and enhancing customer trust and confidence. A robust network security model can also help the organization comply with regulatory requirements and reduce financial losses due to cyber attacks.
Ratings and Reviews
by Darrell Crawford
April 10, 2022
by Del Holmes
April 9, 2022

Free Network Security Google Slides Themes And Powerpoint Templates

Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches

17 templates

american history
85 templates

49 templates

43 templates

el salvador
34 templates

art portfolio
100 templates
Network Security Introduction Workshop
It seems that you like this template, network security introduction workshop presentation, free google slides theme, powerpoint template, and canva presentation template.
Are you planning on teaching an introduction to network security workshop? If so, this template is just what you need. Elegant, sophisticated, full of materials you can customize… Its design in blue and white is perfect to present your information in a way that’s attractive but also serious and professional. Add your own facts and figures, and you’ll be ready to show the wonders of network security to your students.
Features of this template
- 100% editable and easy to modify
- 30 different slides to impress your audience
- Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups
- Includes 500+ icons and Flaticon’s extension for customizing your slides
- Designed to be used in Google Slides, Canva, and Microsoft PowerPoint
- 16:9 widescreen format suitable for all types of screens
- Includes information about fonts, colors, and credits of the resources used
How can I use the template?
Am I free to use the templates?
How to attribute?
Attribution required If you are a free user, you must attribute Slidesgo by keeping the slide where the credits appear. How to attribute?

Register for free and start downloading now
Related posts on our blog.

How to Add, Duplicate, Move, Delete or Hide Slides in Google Slides
How to Change Layouts in PowerPoint
How to Change the Slide Size in Google Slides
Related presentations.

Premium template
Unlock this template and gain unlimited access

- All Resource
PPT Templates
Single slides.
- Pitch Deck 215 templates
- Animation 341 templates
- Vertical Report 316 templates
- Business 813 templates
- Finance 56 templates
- Construction 46 templates
- IT/Commerce 173 templates
- Medical 64 templates
- Education 45 templates
- Lifestyle 402 templates
- Pitch Decks 138 templates
- Business 547 templates
- Finance 20 templates
- Construction 75 templates
- IT/Commerce 73 templates
- Medical 27 templates
- Lifestyle 578 templates
- Pitch Decks 140 templates
- Business 469 templates
- Finance 19 templates
- Construction 64 templates
- IT/Commerce 72 templates
- Medical 29 templates
- Education 39 templates
- Lifestyle 490 templates
- Cover 266 templates
- Agenda 97 templates
- Overview 216 templates
- CEO 28 templates
- Our Team 142 templates
- Organization 48 templates
- History 38 templates
- Vision, Mission 109 templates
- Problem, Solution 193 templates
- Opportunity 154 templates
- Business Model 158 templates
- Product, Services 299 templates
- Technology 65 templates
- Market 155 templates
- Prices 56 templates
- Customers 55 templates
- Competitor 113 templates
- Business Process 151 templates
- Analysis 222 templates
- Strategy 120 templates
- Marketing, Sales 61 templates
- Profit, Loss 69 templates
- Financials 247 templates
- Timeline 122 templates
- Proposal 40 templates
- Contact Us 272 templates
- Break Slides 16 templates
- List 361 templates
- Process 351 templates
- Cycle 177 templates
- Hierarchy 98 templates
- Relationship 152 templates
- Matrix 86 templates
- Pyramid 67 templates
- Tables 145 templates
- Map 96 templates
- Puzzles 163 templates
- Graph 217 templates
- Infographics 436 templates
- SWOT 111 templates
- Icon 418 templates
- Theme Slides 138 templates
- Mockup 42 templates
- Column 315 templates
- Line 199 templates
- Pie 139 templates
- Bar 179 templates
- Area 130 templates
- X Y,Scatter 16 templates
- Stock 59 templates
- Surface 3 templates
- Doughnut 256 templates
- Bubble 65 templates
- Radar 83 templates
- Free PPT Templates 2,101 templates
- Free Keynote 2,017 templates
- Free Google Slides 2,098 templates
- Free Theme Slides 35 templates
- Free Diagram 126 templates
- Free Chart 49 templates
- New Updates
Result for ' network security '
343 Templates are available.
- Sort by Accuracy
- Sort by Newest

Business Social network Pitch Deck Powerpoint Presentation
Easy customization All images included Modern and clean design Easy color change Modern layouts based on master slides

security Company Pitch Deck PowerPoint Presentation Design
Modern, simple, and clean design Easy customization 100% fully editable PowerPoint slides Easy editable data driven charts (pie, bar, line) Master layout with text placeholders

Social network Communication Modern PPT Templates
Quick and easy to customize Highly editable presentation template. 16:9 aspect ratio Professional business presentation 100% fully editable via Excel Shapes: fully editable vector graphics All elements are editable

security Slide Presentation
Easy to change colors 100% vector (fully editable maps, infographic, icons) Professional business presentation Easy to edit in PowerPoint

Social network Simple PowerPoint Templates
Modern, simple, and clean design 100% fully editable PowerPoint slides Scalable vectorial PowerPoint shapes and PowerPoint icons Easy to customize without graphic design skills Perfect themes for business or educational. Data charts editable via Excel

Biometrics security PowerPoint Templates for Presentation
Highly editable presentation template. 100% vector (fully editable maps, infographic, icons) Easy to edit in PowerPoint Easy color change All elements are editable

security Interactive PPT
Easy customization For professionals and educators Creatively crafted slides Easy color change

E-Commerce and Cyber security Puzzle Infographic Diagram
Easy to edit and customize 100% fully editable PowerPoint slides Quick and easy to customize Shapes: fully editable vector graphics

New Social network ing, Threads business ppt
Built-in custom color palette Creative slides Professional and unique slides Free font used Suitable for creative projects

Cyber security pitch deck Keynote Templates
Creative slides Easily editable content Data charts Dark version

security Check List Diagram (Cyber security)
Easy to edit and customize Quick and easy to customize Easy color change Dark and light versions of each Aspect ratio - 4:3 (normal), 16:9 (widescreen)

4 Rings Step Diagram (Cyber security )
Easy to edit and customize 100% fully editable PowerPoint slides Quick and easy to customize Easy color change Dark and light versions of each 2 aspect ratios (4:3 & 16:9)

4 Steps Hexagonal Pyramid Diagram (Cyber security )
Standard (4x3) version of this template also available. Easy customization Quick and easy to customize Easy to change colors Dark & light backgrounds

Key with Jigsaw Puzzle Diagram (Cyber security )
Standard (4x3) version of this template also available. Easy to edit in PowerPoint 100% fully editable PowerPoint slides Quick and easy to customize Easy color change

Iris Recognition Puzzle Diagram (Cyber security )
Standard (4x3) version of this template also available. Quick and easy to customize Easy to change colors Dark & light backgrounds

Padlock with Puzzle Diagram (Cyber security )
Easy customization 100% fully editable PowerPoint slides Quick and easy to customize Easy color change Dark & light backgrounds

Shields with puzzle pieces Diagram (Cyber security )
100% fully editable PowerPoint slides Shapes: fully editable vector graphics Dark and light versions of each 16:9, 4:3 aspect ratios

Devices Pairing Diagram (Cyber security )
Easy to edit and customize 100% fully editable PowerPoint slides Quick and easy to customize Easy to change colors Dark & light backgrounds

Lock Screen Diagram (Cyber security )
Easy to edit and customize 100% fully editable PowerPoint slides Quick and easy to customize Easy color change Dark & light backgrounds 2 aspect ratios (4:3 & 16:9)

Laptop security Infographic Diagram (Cyber security)
Easy to edit in PowerPoint 100% fully editable PowerPoint slides Quick and easy to customize Dark and light versions of each 2 aspect ratios (4:3 & 16:9)
1 / 18 page
Free Slides
Slide Members
All Rights Reserved 2024 © Copyright Slide Members
Information
- Privacy Policy
- Terms & Conditions
Recent Slides
- 21+ Latest weekly update Powerpoint Templates & Google slides
- 15+ New Animation Powerpoint Templates Update
- 17+ Recently Powerpoint Templates & Google slides Update
JavaScript seems to be disabled in your browser. For the best experience on our site, be sure to turn on Javascript in your browser.
- My Wish List
- Compare Products
- Presentations
Network Security
You must be logged in to download this file*
item details (6 Editable Slides)
(6 Editable Slides)
Related Products
Don't miss this deck if you want to captivate your viewers with a simple yet impactful slideshow. Leverage our brilliant Network Security PowerPoint template to describe the measures used to protect the company's network from security breaches, online threats, intrusions, etc.
Cyber security experts, security consultants, and network security engineers can use these fantastic PowerPoint slides to shed light on the types of network security attacks, including brute force attacks, malware, phishing, etc. You can also use this set to explain the importance and advantages of network security.
Sizing Charts
| Size | XS | S | S | M | M | L |
|---|---|---|---|---|---|---|
| EU | 32 | 34 | 36 | 38 | 40 | 42 |
| UK | 4 | 6 | 8 | 10 | 12 | 14 |
| US | 0 | 2 | 4 | 6 | 8 | 10 |
| Bust | 79.5cm / 31" | 82cm / 32" | 84.5cm / 33" | 89.5cm / 35" | 94.5cm / 37" | 99.5cm / 39" |
| Waist | 61.5cm / 24" | 64cm / 25" | 66.5cm / 26" | 71.5cm / 28" | 76.5cm / 30" | 81.5cm / 32" |
| Hip | 86.5cm / 34" | 89cm / 35" | 91.5cm / 36" | 96.5cm / 38" | 101.5cm / 40" | 106.5cm / 42" |
| Size | XS | S | M | L | XL | XXL |
|---|---|---|---|---|---|---|
| UK/US | 34 | 36 | 38 | 40 | 42 | 44 |
| Neck | 37cm / 14.5" | 38cm /15" | 39.5cm / 15.5" | 41cm / 16" | 42cm / 16.5" | 43cm / 17" |
| Chest | 86.5cm / 34" | 91.5cm / 36" | 96.5cm / 38" | 101.5cm / 40" | 106.5cm / 42" | 111.5cm / 44" |
| Waist | 71.5cm / 28" | 76.5cm / 30" | 81.5cm / 32" | 86.5cm / 34" | 91.5cm / 36" | 96.5cm / 38" |
| Seat | 90cm / 35.4" | 95cm / 37.4" | 100cm / 39.4" | 105cm / 41.3" | 110cm / 43.3" | 115cm / 45.3" |
Newly Launched - AI Presentation Maker
AI PPT Maker
Design Services
Business PPTs
Business Plan
Introduction PPT
Self Introduction
Startup Business Plan
Cyber Security
Digital Marketing
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
All Categories
Network security PowerPoint Presentation Templates and Google Slides
DISPLAYING: 60 of 416 Items
- You're currently reading page 1

Organizational Network Security Awareness Staff Learning Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in-house and outside by utilizing this complete deck. This organizational network security awareness staff learning ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well-researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Secure Network Construction Proposal Example Document Report Doc Pdf Ppt
Heres a predesigned Secure Network Construction Proposal Example Document Report Doc Pdf Ppt for you. Built on extensive research and analysis, this one-complete deck has all the center pieces of your specific requirements. This temple exudes brilliance and professionalism. Being completely editable, you can make changes to suit your purpose. Get this Secure Network Construction Proposal Example Document Report Doc Pdf Ppt A4 One-pager now.

Cloud Computing Security Networking Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cloud computing security networking ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Wireless Network Security System Smart Lock Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this wireless network security system smart lock ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.

Cloud Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cloud Network Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
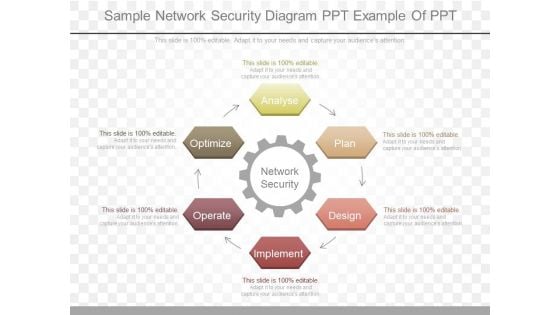
Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.
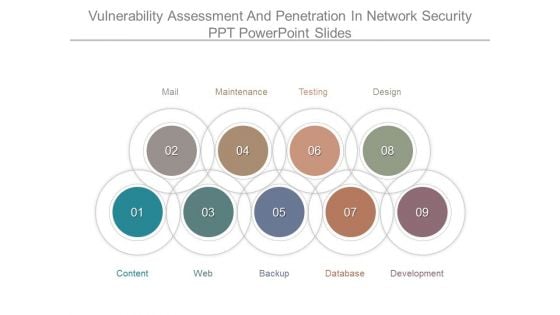
Vulnerability Assessment And Penetration In Network Security Ppt Powerpoint Slides
This is a vulnerability assessment and penetration in network security ppt powerpoint slides. This is a nine stage process. The stages in this process are mail, maintenance, testing, design, development, database, backup, web, content.

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
Network Security Enterprise Ppt Powerpoint Presentation Infographics Templates Cpb
This is a network security enterprise ppt powerpoint presentation infographics templates cpb. This is a five stage process. The stages in this process are network security enterprise.
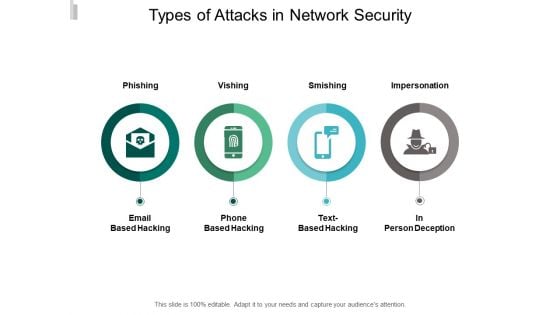
Types Of Attacks In Network Security Ppt PowerPoint Presentation Portfolio Layouts
Presenting this set of slides with name types of attacks in network security ppt powerpoint presentation portfolio layouts. This is a four stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Home Security Network Icon Ppt PowerPoint Presentation Portfolio Ideas
Presenting this set of slides with name home security network icon ppt powerpoint presentation portfolio ideas. The topics discussed in these slides are communication, teamwork, build network. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Network Security Small Business Ppt PowerPoint Presentation Gallery Ideas Cpb
Presenting this set of slides with name network security small business ppt powerpoint presentation gallery ideas cpb. This is an editable Powerpoint ten stages graphic that deals with topics like network security small business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Security Ppt PowerPoint Presentation Infographics Graphics Example Cpb
Presenting this set of slides with name network security ppt powerpoint presentation infographics graphics example cpb. This is an editable Powerpoint four stages graphic that deals with topics like network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Small Business Network Security Ppt PowerPoint Presentation Ideas Summary Cpb
Presenting this set of slides with name small business network security ppt powerpoint presentation ideas summary cpb. This is an editable Powerpoint six stages graphic that deals with topics like small business network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Importance Network Security Ppt PowerPoint Presentation Portfolio Graphic Images Cpb
Presenting this set of slides with name importance network security ppt powerpoint presentation portfolio graphic images cpb. This is an editable Powerpoint six stages graphic that deals with topics like importance network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Datacenter Services Network Security Ppt Sample
This is a datacenter services network security ppt sample. This is a five stage process. The stages in this process are arrow, business, marketing.

Protected Globe Network Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with protected global network the internet

Cyber Network Code Security PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with cyber security network data monitor as abstract

Firewall Network Security Communication PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Firewall Network Security Communication PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime. Use our Technology PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination. Download our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Download and present our Business PowerPoint Templates because It will Strengthen your hand with your thoughts. They have all the aces you need to win the day. Present our Signs PowerPoint Templates because It will mark the footprints of your journey. Illustrate how they will lead you to your desired destination.Use these PowerPoint slides for presentations relating to firewall, security, business, signs, communication, technology. The prominent colors used in the PowerPoint template are Green, Red, White.

Secure Internet Browser Networking PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Secure Internet Browser Networking PowerPoint Templates PPT Backgrounds For Slides 0213.Download our Internet PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our Technology PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Use our Security PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Communication PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate.Use these PowerPoint slides for presentations relating to Secure internet browser, internet, technology, security, communication, business. The prominent colors used in the PowerPoint template are Yellow, Orange, Gray.
Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black.

Firewall Secured Network Business Communication PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our Firewall Secured Network Business Communication PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download and present our Technology PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time. Present our Signs PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to Security plan for a firewall system, business, communication, technology, success, signs. The prominent colors used in the PowerPoint template are Green, Red, Gray.
Network Security Devices Computer Network Ppt PowerPoint Presentation Visual Aids Background Images Cpb Pdf
Presenting this set of slides with name network security devices computer network ppt powerpoint presentation visual aids background images cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like network security devices computer network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Our Team For Secure Network Construction Proposal One Pager Sample Example Document
Presenting you an exemplary Our Team For Secure Network Construction Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Team For Secure Network Construction Proposal One Pager Sample Example Document brilliant piece now.
Telecommunications Network Security Ppt PowerPoint Presentation Summary Microsoft Cpb
Presenting this set of slides with name telecommunications network security ppt powerpoint presentation summary microsoft cpb. This is a three stage process. The stages in this process are telecommunications network security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Network Security Architecture Practices Ppt PowerPoint Presentation Gallery Infographics Cpb
Presenting this set of slides with name network security architecture practices ppt powerpoint presentation gallery infographics cpb. This is an editable Powerpoint five stages graphic that deals with topics like network security architecture practices to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
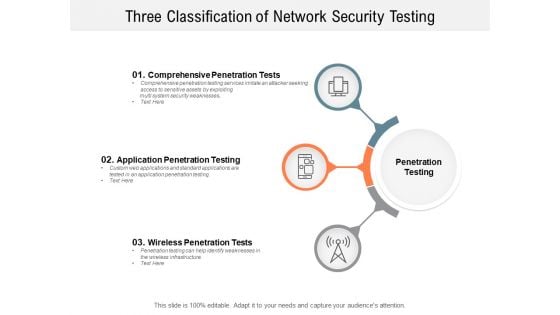
Three Classification Of Network Security Testing Ppt PowerPoint Presentation Slides Demonstration
Presenting this set of slides with name three classification of network security testing ppt powerpoint presentation slides demonstration. This is a three stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Network Monitoring Management Security Ppt PowerPoint Presentation Summary Clipart Images Cpb
Presenting this set of slides with name network monitoring management security ppt powerpoint presentation summary clipart images cpb. This is an editable Powerpoint five stages graphic that deals with topics like network monitoring management security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Scads Network Security Assessment Ppt PowerPoint Presentation Icon Deck Cpb
Presenting this set of slides with name scads network security assessment ppt powerpoint presentation icon deck cpb. This is an editable Powerpoint five stages graphic that deals with topics like scads network security assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Security Tools Ppt PowerPoint Presentation Summary Layout Ideas Cpb
Presenting this set of slides with name network security tools ppt powerpoint presentation summary layout ideas cpb. This is an editable Powerpoint three stages graphic that deals with topics like network security tools to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Network Security Vs Firewall Ppt PowerPoint Presentation Infographic Template Gridlines Cpb
Presenting this set of slides with name network security vs firewall ppt powerpoint presentation infographic template gridlines cpb. This is an editable Powerpoint five stages graphic that deals with topics like network security vs firewall to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Computer Network Security Training Ppt PowerPoint Presentation Slides Portfolio Cpb Pdf
Presenting this set of slides with name computer network security training ppt powerpoint presentation slides portfolio cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like computer network security training to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secure Hybrid Network Ppt PowerPoint Presentation Ideas Slides Cpb
Presenting this set of slides with name secure hybrid network ppt powerpoint presentation ideas slides cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure hybrid network to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Business Network Security Vector Icon Ppt PowerPoint Presentation Gallery Examples PDF
Presenting this set of slides with name business network security vector icon ppt powerpoint presentation gallery examples pdf. This is a three stage process. The stages in this process are business network security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Company Network Security Icon Ppt PowerPoint Presentation File Infographics PDF
Presenting this set of slides with name company network security icon ppt powerpoint presentation file infographics pdf. The topics discussed in these slide is company network security icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Securing Windows With Network Security System Ppt PowerPoint Presentation File Slides PDF
Presenting this set of slides with name securing windows with network security system ppt powerpoint presentation file slides pdf. The topics discussed in these slide is securing windows with network security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security For Network Protection From Unauthorized Access Vector Icon Ppt PowerPoint Presentation File Summary PDF
Presenting this set of slides with name security for network protection from unauthorized access vector icon ppt powerpoint presentation file summary pdf. This is a three stage process. The stages in this process are security for network protection from unauthorized access vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Importance Of Firewall Network Security In Business Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name importance of firewall network security in business vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are importance of firewall network security in business vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Transfer On Secured Network Vector Icon Ppt PowerPoint Presentation File Demonstration PDF
Presenting this set of slides with name data transfer on secured network vector icon ppt powerpoint presentation file demonstration pdf. This is a two stage process. The stages in this process are data transfer on secured network vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Vector Showing Wide Area Network Security Analysis Ppt PowerPoint Presentation Summary Templates PDF
Presenting this set of slides with name vector showing wide area network security analysis ppt powerpoint presentation summary templates pdf. This is a three stage process. The stages in this process are vector showing wide area network security analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Data Network Security With Lock Showing Online Safety Icon Ppt PowerPoint Presentation Infographic Template Graphics PDF
Presenting this set of slides with name data network security with lock showing online safety icon ppt powerpoint presentation infographic template graphics pdf. This is a two stage process. The stages in this process are data network security with lock showing online safety icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cloud Network Security Dimensions And Sections Ppt PowerPoint Presentation Icon Background Images PDF
Presenting cloud network security dimensions and sections ppt powerpoint presentation icon background images pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, service, threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
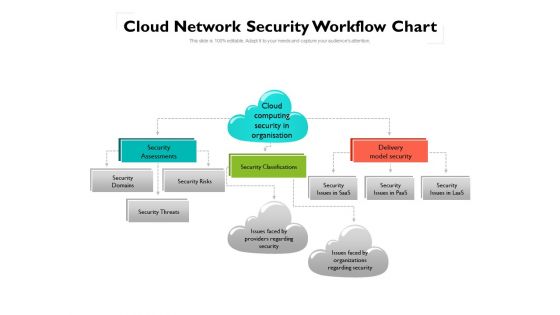
Cloud Network Security Workflow Chart Ppt PowerPoint Presentation Gallery Ideas PDF
This is a cloud network security workflow chart ppt powerpoint presentation gallery ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, organizations, domains. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
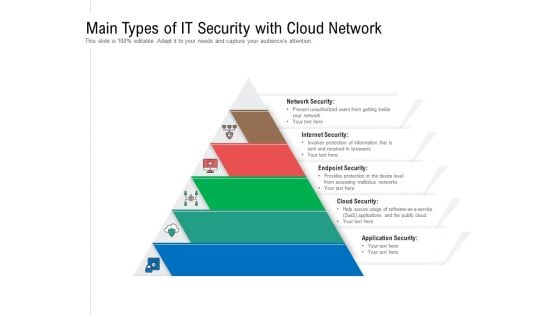
Main Types Of IT Security With Cloud Network Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main types of it security with cloud network ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including network security, internet security, endpoint security, cloud security, application security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Year Data Sharing Security Network Career Roadmap Clipart
Introducing our five year data sharing security network career roadmap clipart. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
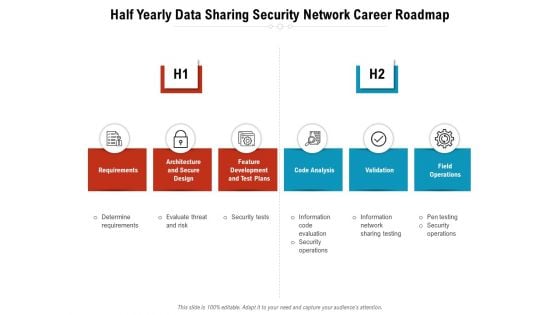
Half Yearly Data Sharing Security Network Career Roadmap Rules
We present our half yearly data sharing security network career roadmap rules. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly data sharing security network career roadmap rules in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
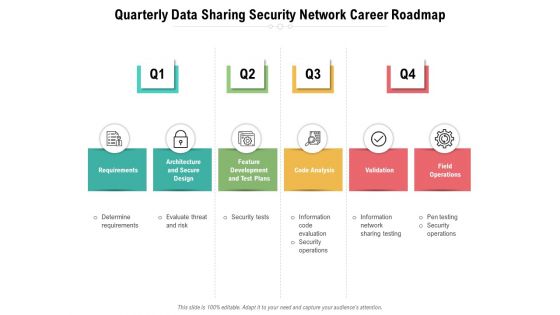
Quarterly Data Sharing Security Network Career Roadmap Guidelines
Presenting our jaw-dropping quarterly data sharing security network career roadmap guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.
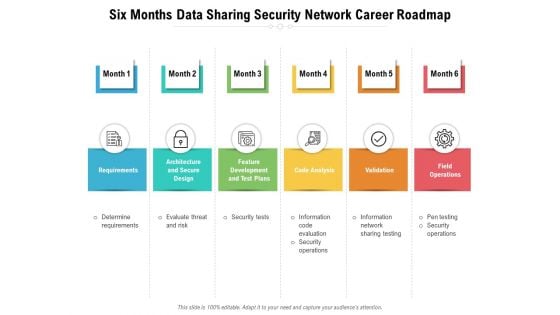
Six Months Data Sharing Security Network Career Roadmap Pictures
Introducing our six months data sharing security network career roadmap pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
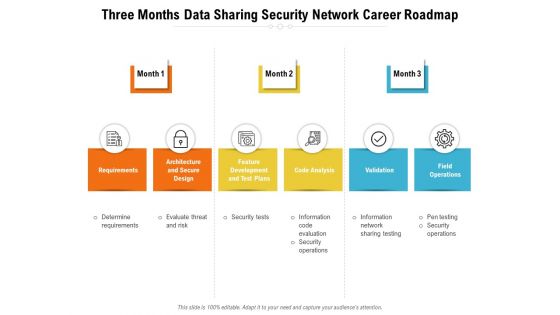
Three Months Data Sharing Security Network Career Roadmap Diagrams
Introducing our three months data sharing security network career roadmap diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Network Protection Icon For Securing Customer Information Ppt PowerPoint Presentation Icon Pictures PDF
Persuade your audience using this network protection icon for securing customer information ppt powerpoint presentation icon pictures pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including network protection icon for securing customer information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Online Technology Security Chip Icon For Network Safety Ppt PowerPoint Presentation File Graphics Example PDF
Persuade your audience using this online technology security chip icon for network safety ppt powerpoint presentation file graphics example pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including online technology security chip icon for network safety. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Three Phases Of Network Security Issues Ppt PowerPoint Presentation Icon Portrait PDF
Presenting three phases of network security issues ppt powerpoint presentation icon portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
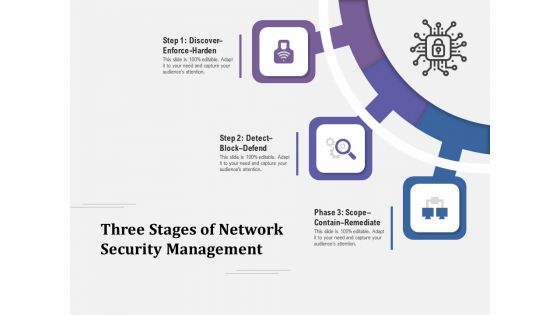
Three Stages Of Network Security Management Ppt PowerPoint Presentation Layouts Influencers PDF
Presenting three stages of network security management ppt powerpoint presentation layouts influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, detect block defend, scope contain remediate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Three Seps Of Enterprise Network Security With Icons Ppt PowerPoint Presentation Icon Slide Portrait PDF
Presenting three seps of enterprise network security with icons ppt powerpoint presentation icon slide portrait pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover enforce harden, scope contain remediate, detect block defend. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
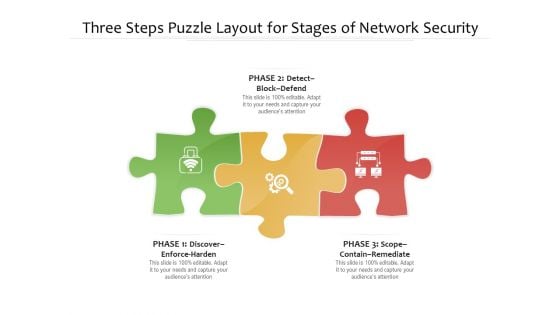
Three Steps Puzzle Layout For Stages Of Network Security Ppt PowerPoint Presentation File Vector PDF
Persuade your audience using this three steps puzzle layout for stages of network security ppt powerpoint presentation file vector pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including detect block defend, discover enforce harden, scope contain remediate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Structure Analysis Model For Security Management Ppt Styles Icons PDF
Showcasing this set of slides titled network structure analysis model for security management ppt styles icons pdf. The topics addressed in these templates are structure, management, analysis. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
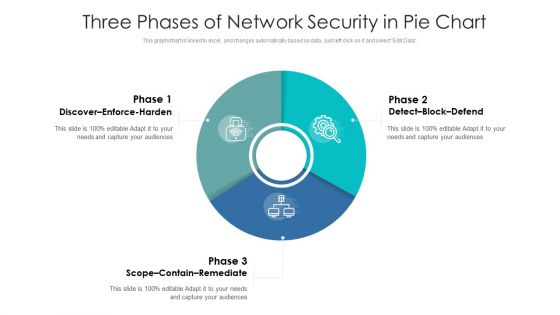
Three Phases Of Network Security In Pie Chart Ppt PowerPoint Presentation Gallery Graphics Download PDF
Pitch your topic with ease and precision using this three phases of network security in pie chart ppt powerpoint presentation gallery graphics download pdf. This layout presents information on discover enforce harden, detect block defend, scope contain remediate. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
VPN For Secure Network Vector Icon Ppt PowerPoint Presentation Pictures Example File PDF
Presenting vpn for secure network vector icon ppt powerpoint presentation pictures example file pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including vpn for secure network vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Secured Public Cloud Network On Premises Vector Icon Ppt PowerPoint Presentation Gallery Slideshow PDF
Persuade your audience using this secured public cloud network on premises vector icon ppt powerpoint presentation gallery slideshow pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including secured public cloud network on premises vector icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
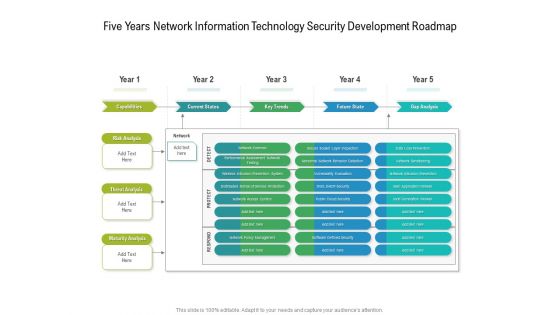
Five Years Network Information Technology Security Development Roadmap Mockup
Presenting our jaw dropping five years network information technology security development roadmap mockup. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Ratings and Reviews
Most relevant reviews, by romika dhamija.
January 21, 2021
by Kirti Jindal
January 24, 2021
by Ankita Jhamb
January 25, 2021
April 18, 2021
April 26, 2021
by Chetna Sharma
April 25, 2021
April 28, 2021
April 29, 2021
June 4, 2021
A quick note about our cookies
We use cookies so we can give you the best website experience possible and to provide us with anonymous data so we can improve our marketing efforts. Read our cookie policy and privacy policy.
Login to your account
New here? Sign up in seconds!
Use social account

Or login with an email
Create an account
Already have an account? Login here
Or sign up with an email

We’re uploading new templates every week
We’d like to send you infrequent emails with brief updates to let you know of the latest free templates. Is that okay?

Reset your Password
Please enter the email you registered with and we will send you a link to reset your password!
Check your email!
We’ve just sent you a link to . Please follow instructions from our email.
- Most Popular Templates
- Corporate & Business Models
- Data (Tables, Graphs & Charts)
- Organization & Planning
- Text Slides
- Our Presentation Services
Get your own design team
Tailored packages for corporates & teams
Cyber Security PowerPoint Template

Number of slides: 10
Cyber security is the set of practices and techniques to defend networks, servers, or electronic devices from malicious cyber-attacks. This is especially important in companies that work with lots of data in its operations. Use this PowerPoint template to train teams on cyber security. You’ll be able to cover from what cyber security means to the best cybersecurity practices in the world.
- About this template
- How to edit
- Custom Design Services
Free Cyber Security PowerPoint Template
Cyber security overview slide.
First things first. Introduce your audience to the basic concepts of cybersecurity. What is cyber security? What’s the importance of cybersecurity? Make sure to connect its benefits to real-life examples from your company.
Cyber Security Map Slide
This slide is ideal to address the best practices of cybersecurity around the world. It has a global map graphic where you can display facts and figures. You can also talk about the biggest cyber attacks in history, so your audience can understand how important this topic is for the company.
Cyber Security Tips Slide
Halfway through your presentation, it is likely that people will be eager to protect their data right away. So, if you’re doing a cyber security 101 session, use this slide to share some tips for beginners. And in case your public is more specialized, give them advice on safe practices to lower the risks of losing their data.
Cyber threats
Some common types of cyber threats include malwares, phishing, trojans, data breaches. Don’t forget to talk about them in your presentation.
Modern technology template
The Cyber Security PowerPoint template has a creative purple-and-blue layout that gives your whole presentation a professional and modern look.
Cyber security icons
You’ll find cyber security icons that will help you organize your content and keep the visual interest on every slide.
FIND OUT MORE ABOUT OUR CUSTOM DESIGN SERVICES
Todd Speranzo
VP of Marketing at Avella
"24Slides helps us get PowerPoints on-brand, and improve overall design in a timeframe that is often “overnight”. Leveraging the time zone change and their deep understanding of PowerPoint, our Marketing team has a partner in 24Slides that allows us to focus purely on slide content, leaving all of the design work to 24Slides."
Gretchen Ponts
Strata Research
"The key to the success with working with 24Slides has been the designers’ ability to revamp basic information on a slide into a dynamic yet clean and clear visual presentation coupled with the speed in which they do so. We do not work in an environment where time is on our side and the visual presentation is everything. In those regards, 24Slides has been invaluable."
"After training and testing, 24Slides quickly learnt how to implement our CVI, deliver at a high quality and provide a dedicated design team that always tries to accommodate our wishes in terms of design and deadlines."
What's included in Keynote Template?
I want this template customized class="mobile-none"for my needs!
69 beautifully designed slides 67 icons included PowerPoint and Keynote ready 16:9 full HD class="mobile-none"resolution
Check out other similar templates
Science Icon Template Pack
General PowerPoint Icons Template
Dark themed 30 Slide Template Pack
Generic Mobile Pack Templates

Cyber Security
What do you think of this template.

Product details
Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security. Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of data on computers and other devices. A significant portion of that data can be sensitive information, whether that be intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure could have negative consequences. Organizations transmit sensitive data across networks and to other devices in the course of doing businesses, and cyber security describes the discipline dedicated to protecting that information and the systems used to process or store it. For an effective cyber security, an organization needs to coordinate its efforts throughout its entire information system. Elements of cyber encompass all of the following – network security, application security, endpoint security, data security, protecting company and customer information, identity management, database and infrastructure security, cloud security, mobile security. The most difficult challenge in cyber security is the ever-evolving nature of security risks themselves. Traditionally, organizations and the government have focused most of their cyber security resources on perimeter security to protect only their most crucial system components and defend against known treats. Today, this approach is insufficient, as the threats advance and change more quickly than organizations can keep up with. As a result, advisory organizations promote more proactive and adaptive approaches to cyber security. Following a cyber risk assessment, develop and implement a plan to mitigate cyber risk. This plan should encompass both the processes and technologies required to build a mature cyber security program. An ever-evolving field, cyber security best practices must evolve to accommodate the increasingly sophisticated attacks carried out by attackers. Combining sound cyber security measures with an educated and security-minded employee base provides the best defense against cyber criminals. While it may seem like a daunting task, start small and focus on your most sensitive data, scaling your efforts as your cyber program matures.
Cyber Security template is intended primarily for companies providing data protection services. You can use the slides from this template when preparing a presentation of your services for a client. For example, you can describe the main areas of data protection that your company provides. Also, the slides of this template will be useful for startups when preparing a description of the data protection process in a new software product. The slides from this template can be used by educators in their data protection courses. All slides in the template are made in a cool color scheme and have modern infographics. If necessary, you can change the slides to suit your corporate style. Cyber Security template will be a worthy addition to your collection of professional presentations.
Related Products
Project Schedule Template

Escalation Matrix
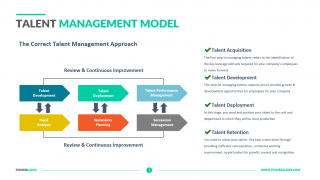
Talent Management Model

Total Quality Management

Incident Report

Data Governance
Pie Chart Analysis

Business Roadmap

Relationship Chart

Standard Operating Procedure
You dont have access, please change your membership plan., great you're all signed up..., verify your account.
PowerSlides.com will email you template files that you've chosen to dowload.
Please make sure you've provided a valid email address! Sometimes, our emails can end up in your Promotions/Spam folder.
Simply, verify your account by clicking on the link in your email.

Network and System Security
Jan 03, 2020
1.12k likes | 1.16k Views
Network and System Security. Introduction. Information Security. Computer security Protect system resources Protect data (dynamic/stored) Network security Protect network resources Protect exchanged data Security = confidentiality + integrity + availability + authenticity. Attacks.
Share Presentation

Presentation Transcript
Network and System Security Introduction CSE 5349/7349
Information Security • Computer security • Protect system resources • Protect data (dynamic/stored) • Network security • Protect network resources • Protect exchanged data Security = confidentiality + integrity + availability + authenticity CSE 5349/7349
Attacks • Passive attacks • Affects data confidentiality • More difficult to detect, less harmful • Active attacks • Affects data confidentiality, integrity, and/or availability • Easier detection, more harmful CSE 5349/7349
Attacks (cont’d) • Interruption • Interception • Modification • Fabrication CSE 5349/7349
Interruption • An asset of the system is destroyed of becomes unavailable or unusable • Attack on availability • Destruction of hardware • Cutting of a communication line • Disabling the file management system CSE 5349/7349
Interception • An unauthorized party gains access to an asset • Attack on confidentiality • Wiretapping to capture data in a network • Illicit copying of files or programs CSE 5349/7349
Modification • An unauthorized party not only gains access but tampers with an asset • Attack on integrity • Change values in a data file • Alter a program to make it perform differently • Modify content of messages transmitted on a network CSE 5349/7349
Fabrication • Unauthorized party inserts counterfeit objects into the system • Attack on authenticity • Insertion of spurious messages in a network • Addition of records to a file CSE 5349/7349
Network Security Services • Authentication • validate authenticity claims (identity/data) • Authorization • Enforce selective access (information/resources) • Confidentiality • Prevent disclosure of data (entire message/selected fields/traffic characteristics) • Integrity • Prevent tampering of data (entire message/selected fields) • Non-repudiation • Proof of origin, proof of delivery CIA CSE 5349/7349
Security Mechanisms • Specific mechanisms • Access control list - resource protection • Encryption – data confidentiality • Digital signature – origin verification, non-repudiation • Notarization – trusted third party assurance • Traffic padding – traffic characteristic confidentiality • Routing control – flow protection CSE 5349/7349
Mechanisms (cont’d) • Pervasive mechanisms • Event detection • Security audit trail • Security recovery CSE 5349/7349
Password Security CSE 5349/7349
System Security • Two issues • Attack by unauthorized users • Attack by authorized users • Solution • Unauthorized – authenticate • Authorized – access control CSE 5349/7349
Authentication • Usual User ID + passwd • ID public, passwd private • When to authenticate • Beginning of session • Periodically within session • After a pause • Beginning of sensitive operation CSE 5349/7349
Selection of Passwd • Psychological issues • Disclosing passwd – social engineering • Difficulty in entering • Difficulty in remembering • System issues • Targeted and general attacks • Multi-lateral security • User training CSE 5349/7349
Attacks on Passwd • Attack on passwd entry • Interface design • Eavesdropping • Trusted path (ex. Ctrl-Alt-Del) • Passwd retry counters • Timing attack • Attack on smart cards • Attack on passwd storage • Audit trail • Need for one-way encryption CSE 5349/7349
Passwd Cracking • Brute force attack • Use all combination of characters • Knowledge of victim • Names, license plate numbers… • Dictionary attack CSE 5349/7349
Defense • Use different passwds for users/systems • No default passwds • Against brute force • Longer passwds • More than letters and numbers • Case sensitive • Against dictionary • No words • No “obvious” passwds CSE 5349/7349
System Defenses • Run passwd filters to weed out weak ones • Generate random passwds for users • Enforce passwd life-time • Limit failed logins • Notifying history to users CSE 5349/7349
Salting the Passwd • What happens if two users choose the same passwd? • Will result in same hash • Add some random information (salt)to the passwd before hashing • Makes it harder to crack CSE 5349/7349
Access Control CSE 5349/7349
Authentication vs. Access Control • Authentication about who you are • Access control – who may do what to what? • Major portion of security breaches organized by authorized users CSE 5349/7349
Control Structures • Formalism • Subjects, Objects, Access permissions • Access control matrix • Example CSE 5349/7349
Capabilities and Access Control Lists (ACL) • For large systems • Large number of subjects and objects • Control matrix very large and sparse • Store the matrix rows and columns as linked lists • Rows – capabilities • Columns - ACLs CSE 5349/7349
Capabilities • What subject A is allowed to do • Whenever a new object is created, other subjects may be given the capabilities to access it CSE 5349/7349
Intermediate Solutions • Group permissions • Negative permissions • Protection rings • Permission trees CSE 5349/7349
Group Permissions • Place number of users in a named group • ACLs for groups CSE 5349/7349
Negative Permission • To exclude specific permission from the group grant CSE 5349/7349
Protection Rings • Assigning priority levels to objects and subjects • 0 kernel • 1 OS • 2 system utilities • 3 other programs • Access decisions based on comparing the levels of Ss and Os. CSE 5349/7349
Hardware Protection • Protection problem • Preventing one processor from interfering with another • Confinement problem • Preventing programs communicate outside the authorized channels • Memory management • Reference monitor CSE 5349/7349
Security Processors • Pentium 3 processor serial number • ARM (Acorn Risc Machine) • Smart cards • Protection of protection hardware • Tamper resistance CSE 5349/7349
Attack (cont’d) • Smashing the stack • Finger bug in UNIX • Does not check the length of the input string • Trailing edge could be used to overwrite the system stack • Want to be a root user? CSE 5349/7349
Cryptography CSE 5349/7349
Terminology • Cryptography • Cryptanalysis • Cryptology • Plain text • Cipher text CSE 5349/7349
Historical Background • Mono-alphabetic substitution • Caesar cipher • Stream ciphers C= P + K mod 26 • One-time pad • Perfect secrecy (Shannon’s theorem) • No integrity • Block codes • Playfair • One-way functions CSE 5349/7349
Formal Classifications • Type of operation • Substitution • Transposition • Number of keys used • Symmetric (one key, private) • Asymmetric (two keys, public) • Mode of plain text processing • Block vs. stream CSE 5349/7349
Cryptanalysis • Attacks • Known plain text attack • Chosen plain text • Chosen cipher text • Security • Unconditionally secure • Computationally secure CSE 5349/7349
Block Ciphers • Block of plain text converted into block of cipher of equal length • Based on Fiestal block structure • Unique transformation • Reversible • Example • Small blocks vulnerable to attacks • Large blocks impractical to implement CSE 5349/7349
Fiestal Cipher (FC) • Based on product ciphers • Alternate substitutions and permutations • Shannon’s proposal • Diffusion • Dissipate plain text statistics into long-range cipher statistics • Example: Averaging operation on characters • A permutation on binary bits followed by some operations • Confusion • To make the deduction of the key difficult CSE 5349/7349
FC Structure • Multiple rounds • Round function (based on the round key) • Substitution (XOR) • Permutation (Exchange of halves) • Parameters • Block size (64 bits) • Key size (128 bits) • Number of rounds (16) • Sub-key generation algorithm • Round function CSE 5349/7349
Plaintext Plaintext Encrypt with Decrypt with secret key secret key Ciphertext DES CSE 5349/7349
DES • Currently the most widely used block cipher in the world • IBM’s LUCIFER was the precursor • One of the largest users of the DES is the banking industry, particularly with EFT • Although the standard is public, the design criteria used are classified CSE 5349/7349
DES Security • Recent analysis has shown that DES is well designed (diffusion & confusion) • Rapid advances in computing speed though have rendered the 56 bit key susceptible to exhaustive key search • 1997 on a large network of computers in a few months • 1998 on dedicated h/w in a few days • 1999 above combined in 22hrs! • DES also theoretically broken using Differential or Linear Cryptanalysis • In practice, unlikely to be a problem yet CSE 5349/7349
Overview of DES Encryption • Basic process consists of: • An initial permutation (IP) • 16 rounds of a complex key dependent calculation F • A final permutation, being the inverse of IP CSE 5349/7349
Initial permutation Round 1 L R i – 1 i – 1 Round 2 K F 56-bit i key … + Round 16 L R i i Final permutation • Each Round • 64-bit key (56-bits + 8-bit parity) • 16 rounds CSE 5349/7349
Initial Permutation • No improvement in security, cipher gets more complex 58, 50, 42, 34, 26, 18, 10, 2, 60, 52, 44, 36, 28, 20, 12, 4, 62, 54, 46, 38, 30, 22, 14, 6, 57, 49, 41, 33, 25, 17, 9, 1, 59, 51, 43, 35, 27, 19, 11, 3, 61, 53, 45, 37, 29, 21, 13, 5, 63, 55, 47, 39, 31, 23, 15, 7 CSE 5349/7349
DES Key Generation • Sub-keys used in each round are formed by • An initial permutation of the key (PC1) which selects 56-bits in two 28-bit halves • 16 stages consisting of: • selecting 24-bits from each half • permuting them by PC2 for use in function f, • rotating each half separately either 1 or 2 places depending on the key rotation schedule KS • Can be described functionally as: SKi = PC2(KS(PC1(Key),i)) CSE 5349/7349
Expansion Function E • Expands RH side data input from 32 to 48 bits by duplicating some bits • Specifically split input into 8 groups of 4 bits • Duplicate bits from either side to form groups of 6 bits CSE 5349/7349
Substitution (S) Boxes • 8 S-boxes, each of which maps 6 bits to 4 bits • Each S-box is actually 4 little 4 bit boxes • Outer bits 1 & 6 (row bits) select one of the 4 rows • Inner bits 2-5 (col bits) are substituted for 4 others CSE 5349/7349
DES Decryption • To decrypt a block of data must unwind all steps of data computation • With Feistel design, same as just doing encryption steps again • Except that must use subkeys in reverse order (SK16 first, then SK15 etc.) CSE 5349/7349
- More by User

Operating System vs. Network Security
Operating System vs. Network Security. Butler Lampson Microsoft. Outline What security is about Operating systems security Network security How they fit together. Security: The Goal. People believe that computers are as secure as real world systems, and it’s true. This is hard because:
564 views • 30 slides

Telecommunications and Network Security
Telecommunications and Network Security. CISSP Guide to Security Essentials Chapter 10. Objectives. Wireline and wireless telecommunication technologies Wired and wireless network technologies Network topologies and cabling The OSI and TCP/IP network models. Objectives (cont.).
1.68k views • 102 slides

Cryptography and Network Security
Cryptography and Network Security. Third Edition by William Stallings Lecture slides by Lawrie Brown Edited by Dick Steflik. Web Security. Web now widely used by business, government, individuals but Internet & Web are vulnerable have a variety of threats integrity confidentiality
430 views • 23 slides

System and Network Security Overview
System and Network Security Overview. What is network security about ?. It is about secure communication What do we mean by secure communication? Everything is connected by the Internet We will often use Alice and Bob
766 views • 49 slides

System and Network Security Overview. What is network security about ?. It is about secure communication Why may the communication be insecure? Everything is connected by the Internet We will often use Alice and Bob
543 views • 42 slides

Network and System Support for Multi-Level Security
Network and System Support for Multi-Level Security. C. Edward Chow Department of Computer Science University of Colorado At Colorado Springs. Outline of the Talk. Motivation. Related Literature
282 views • 16 slides

computer and network security
computer and network security. matt barrie <[email protected]>. authentication. Hi! I’m Alice. Alice. Bob. insecure channel. Eve (Eve owns the channel!). How does Bob know that Alice is Alice, not Eve?. authentication. Authentication is a means by which identity is established.
487 views • 35 slides

Network and Communications Network Security
Network and Communications Network Security. Department of Computer Science. Virginia Commonwealth University. Topics. Elements of Number Theory Public-Key Cryptography Principles Knapsack Algorithm RSA algorithm Computational aspects Diffie – Hellman Key Exchange.
543 views • 39 slides

Network Programming and Network Security
Network Programming and Network Security. Lane Thames Graduate Research Assistant. Outline for Today. Discuss Network security and how it relates to network programming After the presentation, we will go to DNAL to tour our data center. Then we are going to hack some computers :>).
471 views • 23 slides

Network and Communications Network Security. Department of Computer Science. Virginia Commonwealth University. Key Distribution. How to deliver a key to two parties A and B wishing to exchange data Key selected by A, Physically delivered to B
533 views • 39 slides

Information and Network Security
Information and Network Security. Ch 2: Classical Encryption Techniques. Symmetric Encryption. or conventional / private-key / single-key sender and recipient share a common key all classical encryption algorithms are private-key was only type prior to invention of public-key in 1970’s
569 views • 40 slides

Cryptography and Network Security. Public Key Cryptography and RSA. Chapter 9 – Public Key Cryptography and RSA.
434 views • 32 slides

Network Video Recorder | Security System Singapore
Network Video Recorder or NVR is a software program that is a solution to an easier recording. The NVR converts video into digital formats to store in your disk drive or on memory slot. It does not capture video itself, but is connected to a hardware dedicated for the purpose of video capturing. It is most commonly connected with the IP video surveillance system. This is a unique method to safely store your data on the system and you can see your happening from your computer or a device far from the original location where the camera is placed.
219 views • 6 slides

Network security and firewall | network security firewall
VRStech expert team comprises certified, experienced professionals who are skilled at quickly finding a perfect network security and firewall solution for your specified issues.
100 views • 6 slides

System and network security in Hyderabad
Hyderabad is the one of the biggest IT hub of the country. There might be many engineers who possess the knowledge of network security but Qadit provides security service to its clients with highly skilled and well knowledgeable personals. We can proudly say that we have satisfied our clients on optimum level by our highly regarded employees who have undergone key system and network security in Hyderabad. Source: qadit.com
74 views • 6 slides

UCCS Network/System Security Research
UCCS Network/System Security Research. C. Edward Chow Xiaobo Joe Zhou Yu Cai Ganesh Godavari Department of Computer Science University of Colorado at Colorado Springs.
588 views • 57 slides

Network and System Security Risk Assessment
Network and System Security Risk Assessment. --Introduction. Outline. Why to begin this subject? Network Security System Security What is in this course? Network protocols and problems System security configuration and programming 知己知彼,百战不殆。. some interesting examples. Conan
225 views • 21 slides

Network and System Security Risk Assessment. --Firewall. About redirect again. Compare the attacking effect of netwox and our redirect Network unreachable caused by the missing gateway We can have a little more control over our system and network. For example:.
740 views • 73 slides

IMAGES
VIDEO
COMMENTS
Network Security Basics. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.
X.800 defines it as: a service provided by a protocol layer of communicating open systems, which ensures adequate security of the systems or of data transfers; RFC 2828 defines it as: a processing or communication service provided by a system to give a specific kind of protection to system resources; X.800 defines it in 5 major categories
This network security PowerPoint presentation will be helpful to throw light on the current scenario of the organization, the requirement of network security in different sectors, and its work. In addition, computer security PPT contains the critical elements of network security, network risk identification, and assessment, steps to mitigate ...
Designing an eyecatching presentation template is time-consuming. Download the following free and ready-to-use Network security powerpoint templates and Google slides themes for the upcoming presentation. You only need to change text, logo or colors on the professional PPT templates.
Contains easy-to-edit graphics such as graphs, maps, tables, timelines and mockups. Includes 500+ icons and Flaticon's extension for customizing your slides. Designed to be used in Google Slides, Canva, and Microsoft PowerPoint. 16:9 widescreen format suitable for all types of screens.
Presenting this set of slides with name network security ppt powerpoint presentation infographics graphics example cpb. This is an editable Powerpoint four stages graphic that deals with topics like network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 ...
network security PPT Templates Download over 6,300+ complete free templates in high resolution. Ready-Made Slide Variety of templates for each industries. ... security Company Pitch Deck PowerPoint Presentation Design. Modern, simple, and clean design Easy customization 100% fully editable PowerPoint slides
Vulnerability • Intentional attacks on computing resources and networks persist for a number of reasons • Complexity of computer software and newly emerging hardware and software combinations make computer and the network susceptible to intrusion • It is difficult to thoroughly test an application for all possible intrusions. Security ...
Cyber security experts, security consultants, and network security engineers can use these fantastic PowerPoint slides to shed light on the types of network security attacks, including brute force attacks, malware, phishing, etc. You can also use this set to explain the importance and advantages of network security.
Network Security Basics. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.
This network security course provides a comprehensive overview of both theory and practice, covering topics such as cryptography, key exchange, email security, web security, hacking, and anti-hacker techniques. The course also explores recent developments in the field. Prerequisites include knowledge of computer communication and networks, TCP/IP protocol stack, and Ethernet.
Presenting this set of slides with name network security ppt powerpoint presentation infographics graphics example cpb. This is an editable Powerpoint four stages graphic that deals with topics like network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 ...
Presenting this set of slides with name network security ppt powerpoint presentation infographics graphics example cpb. This is an editable Powerpoint four stages graphic that deals with topics like network security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 ...
You'll find cyber security icons that will help you organize your content and keep the visual interest on every slide. Get your presentation custom designed by us, starting at just $10 per slide. STEP 1. UPLOAD PRESENTATION. Share your presentation and design preferences via our easy-to-use order form. STEP 2.
Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security. Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store ...
Introduction to Network Security. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.
921 likes | 1.73k Views. Introduction to network security . L. Tahani Al jehani. COMPUTER SECURITY CONCEPTS. Information security : Before the widespread use of data processing equipment, the security of information felt to be valuable to an organization was provide primarily by physical and administrative means. Download Presentation.
Network and System Security. An Image/Link below is provided (as is) to download presentation Download Policy: Content on the Website is provided to you AS IS for your information and personal use and may not be sold / licensed / shared on other websites without getting consent from its author. Download presentation by click this link.