What Is a Research Paper?
- An Introduction to Punctuation
Olivia Valdes was the Associate Editorial Director for ThoughtCo. She worked with Dotdash Meredith from 2017 to 2021.
:max_bytes(150000):strip_icc():format(webp)/Olivia-Valdes_WEB1-1e405fc799d9474e9212215c4f21b141.jpg)
- B.A., American Studies, Yale University
A research paper is a common form of academic writing . Research papers require students and academics to locate information about a topic (that is, to conduct research ), take a stand on that topic, and provide support (or evidence) for that position in an organized report.
The term research paper may also refer to a scholarly article that contains the results of original research or an evaluation of research conducted by others. Most scholarly articles must undergo a process of peer review before they can be accepted for publication in an academic journal.

Define Your Research Question
The first step in writing a research paper is defining your research question . Has your instructor assigned a specific topic? If so, great—you've got this step covered. If not, review the guidelines of the assignment. Your instructor has likely provided several general subjects for your consideration. Your research paper should focus on a specific angle on one of these subjects. Spend some time mulling over your options before deciding which one you'd like to explore more deeply.
Try to choose a research question that interests you. The research process is time-consuming, and you'll be significantly more motivated if you have a genuine desire to learn more about the topic. You should also consider whether you have access to all of the resources necessary to conduct thorough research on your topic, such as primary and secondary sources .
Create a Research Strategy
Approach the research process systematically by creating a research strategy. First, review your library's website. What resources are available? Where will you find them? Do any resources require a special process to gain access? Start gathering those resources—especially those that may be difficult to access—as soon as possible.
Second, make an appointment with a reference librarian . A reference librarian is nothing short of a research superhero. He or she will listen to your research question, offer suggestions for how to focus your research, and direct you toward valuable sources that directly relate to your topic.
Evaluate Sources
Now that you've gathered a wide array of sources, it's time to evaluate them. First, consider the reliability of the information. Where is the information coming from? What is the origin of the source? Second, assess the relevance of the information. How does this information relate to your research question? Does it support, refute, or add context to your position? How does it relate to the other sources you'll be using in your paper? Once you have determined that your sources are both reliable and relevant, you can proceed confidently to the writing phase.
Why Write Research Papers?
The research process is one of the most taxing academic tasks you'll be asked to complete. Luckily, the value of writing a research paper goes beyond that A+ you hope to receive. Here are just some of the benefits of research papers.
- Learning Scholarly Conventions: Writing a research paper is a crash course in the stylistic conventions of scholarly writing. During the research and writing process, you'll learn how to document your research, cite sources appropriately, format an academic paper, maintain an academic tone, and more.
- Organizing Information: In a way, research is nothing more than a massive organizational project. The information available to you is near-infinite, and it's your job to review that information, narrow it down, categorize it, and present it in a clear, relevant format. This process requires attention to detail and major brainpower.
- Managing Time: Research papers put your time management skills to the test. Every step of the research and writing process takes time, and it's up to you to set aside the time you'll need to complete each step of the task. Maximize your efficiency by creating a research schedule and inserting blocks of "research time" into your calendar as soon as you receive the assignment.
- Exploring Your Chosen Subject: We couldn't forget the best part of research papers—learning about something that truly excites you. No matter what topic you choose, you're bound to come away from the research process with new ideas and countless nuggets of fascinating information.
The best research papers are the result of genuine interest and a thorough research process. With these ideas in mind, go forth and research. Welcome to the scholarly conversation!
- Documentation in Reports and Research Papers
- Thesis: Definition and Examples in Composition
- An Introduction to Academic Writing
- How to Use Footnotes in Research Papers
- How to Write an Abstract
- Definition and Examples of Analysis in Composition
- What Is a Critique in Composition?
- How to Take Better Notes During Lectures, Discussions, and Interviews
- What Is a Literature Review?
- Research in Essays and Reports
- Topic In Composition and Speech
- Focusing in Composition
- What Is a Citation?
- What Are Endnotes, Why Are They Needed, and How Are They Used?
- What Is Plagiarism?
- Definition of Appendix in a Book or Written Work
- Skip to main content
- Skip to ChatBot Assistant
- Academic Writing
What is a Research Paper?
- Steps in Writing a Research Paper
- Critical Reading and Writing
- Punctuation
- Writing Exercises
- ELL/ESL Resources
"Research paper." What image comes into mind as you hear those words: working with stacks of articles and books, hunting the "treasure" of others' thoughts? Whatever image you create, it's a sure bet that you're envisioning sources of information--articles, books, people, artworks. Yet a research paper is more than the sum of your sources, more than a collection of different pieces of information about a topic, and more than a review of the literature in a field. A research paper analyzes a perspective argues a point . Regardless of the type of research paper you are writing, your finished research paper should present your own thinking backed up by others' ideas and information.
To draw a parallel, a lawyer researches and reads about many cases and uses them to support his or her own case. A scientist reads many case studies to support an idea about a scientific principle. In the same way, a history student writing about the Vietnam War might read newspaper articles and books and interview veterans to develop and/or confirm a viewpoint and support it with evidence.
A research paper is an expanded essay that presents your own interpretation or evaluation or argument. When you write an essay, you use everything that you personally know and have thought about a subject. When you write a research paper you build upon what you know about the subject and make a deliberate attempt to find out what experts know. A research paper involves surveying a field of knowledge in order to find the best possible information in that field. And that survey can be orderly and focused, if you know how to approach it. Don't worry--you won't get lost in a sea of sources.
In fact, this guide is designed to help you navigate the research voyage, through developing a research question and thesis, doing the research, writing the paper, and correctly documenting your sources.
Need Assistance?
If you would like assistance with any type of writing assignment, learning coaches are available to assist you. Please contact Academic Support by emailing [email protected].
Questions or feedback about SUNY Empire's Writing Support?
Contact us at [email protected] .
Smart Cookies
They're not just in our classes – they help power our website. Cookies and similar tools allow us to better understand the experience of our visitors. By continuing to use this website, you consent to SUNY Empire State University's usage of cookies and similar technologies in accordance with the university's Privacy Notice and Cookies Policy .
Reference management. Clean and simple.
Types of research papers
Analytical research paper
Argumentative or persuasive paper, definition paper, compare and contrast paper, cause and effect paper, interpretative paper, experimental research paper, survey research paper, frequently asked questions about the different types of research papers, related articles.
There are multiple different types of research papers. It is important to know which type of research paper is required for your assignment, as each type of research paper requires different preparation. Below is a list of the most common types of research papers.
➡️ Read more: What is a research paper?
In an analytical research paper you:
- pose a question
- collect relevant data from other researchers
- analyze their different viewpoints
You focus on the findings and conclusions of other researchers and then make a personal conclusion about the topic. It is important to stay neutral and not show your own negative or positive position on the matter.
The argumentative paper presents two sides of a controversial issue in one paper. It is aimed at getting the reader on the side of your point of view.
You should include and cite findings and arguments of different researchers on both sides of the issue, but then favor one side over the other and try to persuade the reader of your side. Your arguments should not be too emotional though, they still need to be supported with logical facts and statistical data.
Tip: Avoid expressing too much emotion in a persuasive paper.
The definition paper solely describes facts or objective arguments without using any personal emotion or opinion of the author. Its only purpose is to provide information. You should include facts from a variety of sources, but leave those facts unanalyzed.
Compare and contrast papers are used to analyze the difference between two:
Make sure to sufficiently describe both sides in the paper, and then move on to comparing and contrasting both thesis and supporting one.
Cause and effect papers are usually the first types of research papers that high school and college students write. They trace probable or expected results from a specific action and answer the main questions "Why?" and "What?", which reflect effects and causes.
In business and education fields, cause and effect papers will help trace a range of results that could arise from a particular action or situation.
An interpretative paper requires you to use knowledge that you have gained from a particular case study, for example a legal situation in law studies. You need to write the paper based on an established theoretical framework and use valid supporting data to back up your statement and conclusion.
This type of research paper basically describes a particular experiment in detail. It is common in fields like:
Experiments are aimed to explain a certain outcome or phenomenon with certain actions. You need to describe your experiment with supporting data and then analyze it sufficiently.
This research paper demands the conduction of a survey that includes asking questions to respondents. The conductor of the survey then collects all the information from the survey and analyzes it to present it in the research paper.
➡️ Ready to start your research paper? Take a look at our guide on how to start a research paper .
In an analytical research paper, you pose a question and then collect relevant data from other researchers to analyze their different viewpoints. You focus on the findings and conclusions of other researchers and then make a personal conclusion about the topic.
The definition paper solely describes facts or objective arguments without using any personal emotion or opinion of the author. Its only purpose is to provide information.
Cause and effect papers are usually the first types of research papers that high school and college students are confronted with. The answer questions like "Why?" and "What?", which reflect effects and causes. In business and education fields, cause and effect papers will help trace a range of results that could arise from a particular action or situation.
This type of research paper describes a particular experiment in detail. It is common in fields like biology, chemistry or physics. Experiments are aimed to explain a certain outcome or phenomenon with certain actions.

Research Paper
- Icon Calendar 11 June 2024
- Icon Page 2825 words
- Icon Clock 13 min read
A research paper is a product of seeking information, analysis, human thinking, and time. Basically, when scholars want to get answers to questions, they start to search for information to expand, use, approve, or deny findings. In simple words, research papers are results of processes by considering writing works and following specific requirements. Besides, scientists study and expand many theories, developing social or technological aspects of human science. However, in order to provide a quality product, they need to know the definition of such a work, its characteristics, type, structure, format, and how to write it in 7 steps.
What Is a Research Paper and Its Purpose
According to its definition, a research paper is a detailed and structured academic document that presents an individual’s analysis, interpretation, or argument based on existing knowledge and literature. The main purpose of writing a research paper is to contribute to existing literature, develop critical thinking and scientific skills, support academic and professional growth, share findings, demonstrate knowledge and competence, and encourage lifelong learning (Wankhade, 2018). Moreover, such a work is one of the types of papers where scholars analyze questions or topics, look for secondary sources, and write papers on defined themes. For example, if an assignment is to write about some causes of global warming or any other topic, a person must write a research proposal on it, analyzing important points and credible sources (Goodson, 2024). Although essays focus on personal knowledge, writing a scholarly document means analyzing sources by following academic standards. In turn, scientists must meet the strict structure of research papers (Busse & August, 2020). As such, writers need to analyze their topics, start to search for sources, cover key aspects, process credible articles, and organize final studies properly. However, a research paper’s length can vary significantly depending on its academic level and purpose.
- Length: Typically 2-10 pages.
- Word Count: Approximately 500-2,500 words.
- Length: Usually 10-30 pages.
- Word Count: Around 2,500-7,500 words.
- Length: Master’s theses are generally 40-80 pages, while doctoral dissertations can be 100-300 pages or more.
- Word Count: Master’s theses are typically 10,000-20,000 words, and doctoral dissertations can range from 20,000-100,000 words, depending on the discipline and complexity.
- Length: Generally 8-12 pages for short articles, but review articles and comprehensive studies can be longer.
- Word Count: Approximately 3,000-8,000 words.
- Length: Usually 5-10 pages.
- Word Count: Around 2,000-4,000 words.
- Length: Typically 6-12 pages.
- Word Count: Approximately 2,500-6,000 words.
- Length: Varies widely, often 20-100 pages.
- Word Count: Around 5,000-30,000 words.
- Length: Generally 5-15 pages.
- Word Count: Approximately 2,000-5,000 words.
- Length: Varies, usually 20-40 pages per chapter.
- Word Count: Around 5,000-10,000 words.
- Length: Typically 100-300 pages.
- Word Count: Approximately 30,000-100,000 words.
Research Characteristics
Any type of work must meet some standards. By considering a research paper, this work must be written accordingly. In this case, their main characteristics are the length, style, format, and sources (Graham & McCoy, 2014). Firstly, the study’s length defines the number of needed sources to be analyzed. Then, the style must be formal and cover impersonal and inclusive language (Graham & McCoy, 2014). Moreover, the format means academic standards of how to organize final works, including its structure and norms. Finally, sources and their number define works as research papers because of the volume of analyzed information (Graham & McCoy, 2014). Hence, these characteristics must be considered while writing scholarly documents. In turn, general formatting guidelines are:
- Use a standard font (e.g., Times New Roman, 12-point).
- Double-space the text.
- Include 1-inch margins on all sides.
- Indent the first line of each paragraph.
- Number all pages consecutively, usually in the upper right corner.
Types of Research Papers
In general, the length of assignments can be different because of instructions. For example, there are two main types of research papers, such as typical and serious works. Firstly, a typical research paper may include definitive, argumentative, interpretive, and other works (Goodson, 2024). In this case, typical papers are from 2 to 10 pages, where students analyze study questions or specific topics. Then, a serious research composition is the expanded version of typical works. In turn, the length of such a paper is more than 10 pages (Wankhade, 2018). Basically, such works cover a serious analysis with many sources. Therefore, typical and serious works are two types that scholars should consider when writing their documents.
Typical Research Works
Basically, typical research works depend on assignments, the number of sources, and the paper’s length. So, this composition is usually a long essay with the analyzed evidence. For example, students in high school and college get such assignments to learn how to research and analyze topics (Goodson, 2024). In this case, they do not need to conduct serious experiments with the analysis and calculation of data. Moreover, students must use the Internet or libraries in searching for credible secondary sources to find potential answers to specific questions. As a result, students gather information on topics and learn how to take defined sides, present unique positions, or explain new directions (Goodson, 2024). Hence, they require an analysis of primary and secondary sources without serious experiments or data.
Serious Research Studies
Although long papers require a lot of time for finding and analyzing credible sources, real experiments are an integral part of research work. Firstly, scholars at universities need to analyze the information from past studies to expand or disapprove of topics (Wankhade, 2018). Then, if scholars want to prove specific positions or ideas, they must get real evidence. In this case, experiments can be surveys, calculations, or other types of data that scholars do personally. Moreover, a dissertation is a serious research paper that young scientists write based on the analysis of topics, data from conducted experiments, and conclusions at the end of work (Wankhade, 2018). Thus, they are studies that take a lot of time, analysis of sources with gained data, and interpretation of results.
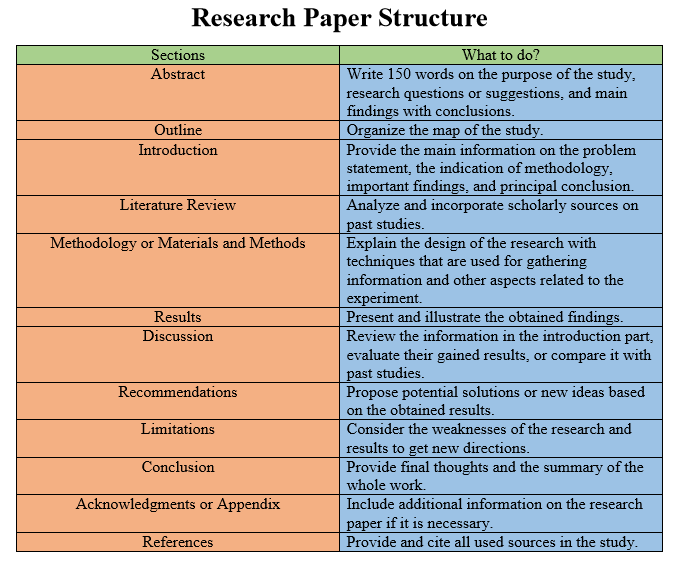
The structure and format of research papers depend on assignment requirements. In fact, when students get their assignments and instructions, they need to analyze specific research questions or topics, find reliable sources, and write final works. Basically, their structure and format consist of the abstract, outline, introduction, literature review, methodology, results, discussion, recommendations, limitations, conclusion, acknowledgments, and references (Graham & McCoy, 2014). However, students may not include some of these sections because of assigned instructions that they have and specific types they must follow. For instance, if instructions are not supposed to conduct real experiments, the methodology section can be skipped because of the data’s absence. In turn, the structure of the final work consists of:
Join our satisfied customers who have received perfect papers from Wr1ter Team.
🔸 The First Part of a Research Study
Abstract or Executive Summary means the first section of a research paper that provides the study’s purpose, its questions or suggestions, and main findings with conclusions. Moreover, this paragraph of about 150 words should be written when the whole work is finished already (Graham & McCoy, 2014). Hence, abstract sections should describe key aspects of studies, including discussions about the relevance of findings.
Outline or Table of Contents serves as a clear map of the structure of a study.
Introduction provides the main information on problem statements, the indication of methodology, important findings, and principal conclusion. Basically, this section covers rationales behind the work or background research, explanation of the importance, defending its relevance, a brief description of experimental designs, defined study questions, hypotheses, or key aspects (Busse & August, 2020). Hence, scholars should provide a short overview of their studies.
🔸 Literature Review and Research or Experiment
Literature Review is needed for the analysis of past studies or scholarly articles to be familiar with research questions or topics. For example, this section summarizes and synthesizes arguments and ideas from scholarly sources without adding new contributions (Scholz, 2022). In turn, this part is organized around arguments or ideas, not sources.
Methodology or Materials and Methods covers explanations of research designs. Basically, techniques for gathering information and other aspects related to experiments must be described in a research paper. For instance, students and scholars document all specialized materials and general procedures (Turbek et al., 2016). In this case, individuals may use some or all of the methods in further studies or judge the scientific merit of the work. Moreover, scientists should explain how they are going to conduct their experiments.
Results mean the gained information or data after the study or experiment. Basically, scholars should present and illustrate their findings (Turbek et al., 2016). Moreover, this section may include tables or figures.
🔸 Analysis of Findings
Discussion is a section where scientists review the information in the introduction part, evaluate gained results, or compare it with past studies. In particular, students and scholars interpret gained data or findings in appropriate depth. For example, if results differ from expectations at the beginning, scientists should explain why that may have happened (Turbek et al., 2016). However, if results agree with rationales, scientists should describe theories that the evidence is supported.
Recommendations take their roots from a discussion section where scholars propose potential solutions or new ideas based on obtained results. In this case, if scientists have any recommendations on how to improve this research so that other scholars can use evidence in further studies, they must write what they think in this section (Graham & McCoy, 2014). Besides, authors can provide their suggestions for further investigation after their evaluations.
Limitations mean a consideration of research weaknesses and results to get new directions. For instance, if scholars find any limitations in their studies that may affect experiments, scholars must not use such knowledge because of the same mistakes (Busse & August, 2020). Moreover, scientists should avoid contradicting results, and, even more, they must write them in this section.
🔸 The Final Part of a Conducted Research
Conclusion includes final claims of a research paper based on findings. Basically, this section covers final thoughts and the summary of the whole work. Moreover, this section may be used instead of limitations and recommendations that would be too small by themselves (Wankhade, 2018). In this case, scientists do not need to use headings as recommendations and limitations.
Acknowledgments or Appendix may take different forms, from paragraphs to charts. In this section, scholars include additional information about what they did.
References mean a section where students, scholars, or scientists provide all used sources by following the format and academic rules.
How to Write a Research Paper in 7 Steps
Writing any research paper requires following a systematic process. Firstly, writers need to select a focused topic they want to analyze. To achieve this objective, comprehensive preliminary research must be conducted to gather credible and relevant sources (Scholz, 2022). After reviewing the existing literature, writers must develop a clear and concise thesis statement sentence to guide the direction of their studies. Then, organizing the main arguments and evidence into a detailed outline ensures a coherent structure. In turn, the initial draft should be started with a compelling introduction, proceeded with body paragraphs that substantiate the thesis through analysis, and ended with a conclusion that underscores the study’s importance (Turbek et al., 2016). Basically, concluding the work by summarizing the findings and emphasizing the significance of the study is crucial. Moreover, revising and editing for content, coherence, and clarity ensures quality (Busse & August, 2020). Finally, proofreading for grammatical accuracy and ensuring adherence to the required formatting guidelines is necessary before submitting the final paper. Hence, when starting a research paper, writers should do the next:
Step 1: Choose a Topic
- Select a Broad Subject: Begin by identifying a specific subject or theme of interest.
- Narrow Down Your Topic: Focus on a specific aspect of the subject or theme to make your examination more focused.
- Establish the Background: Do a preliminary analysis of sources to ensure there is enough information available and refine your topic further.
- Formulate a Research Question : Create a first draft of a clear, concise research question or thesis statement to guide your study.
Step 2: Conduct Preliminary Analysis
- Gather Credible Sources: Use books, academic journals, scholarly articles, reputable websites, and other primary and secondary sources.
- Choose Only Relevant Sources: Review chosen sources for their content and pick only relevant ones.
- Take Notes: Organize your notes, highlighting key points and evidence and how they relate to your initial thesis.
- Create an Annotated Bibliography: Summarize each source in one paragraph and note how it will contribute to your paper.
Step 3: Develop a Working Thesis Statement
- Be Specific: Revise your initial thesis, making it a working one, outlining the main argument or position of your paper.
- Make It Debatable: Ensure that your working thesis presents a viewpoint that others might challenge or debate.
- Be Concise: Write your working thesis statement in one or two sentences.
- Stay Focused: Your working thesis must be focused and specific.
Step 4: Create an Outline
- Beginning: Outline your opening paragraph, including your working thesis statement.
- Middle Sections : Separate your body into sections with headings for each main point or argument and include sub-points and supporting evidence.
- Ending: Plan your concluding section to summarize your findings and restate your thesis in the light of the evidence presented.
- The List of Sources: Finish your outline by providing citation entries of your sources.
Step 5: Write the First Draft
- Introduction: Start with an engaging opening, provide background information, and state your thesis.
- Body Section: Each body paragraph should focus on a single idea and start with a specific topic sentence, followed by evidence and analysis that supports your thesis.
- Conclusion: Summarize your arguments, restate the importance of your topic, and suggest further investigation, analysis, examination, or possible implications.
- Reference Page: Include the list of references used in your first draft.
Step 6: Revise and Edit
- Content Review: Check for clarity, coherence, and whether each part supports your thesis.
- Structure and Flow: Ensure logical flow of ideas between sections and paragraphs.
- Grammar and Style: Correct grammatical errors, improve sentence structure, and refine your writing style.
- Citations: Ensure all sources are correctly cited in your chosen citation style (APA, MLA, Chicago/Turabian, Harvard, etc.).
Step 7: Finalize Your Paper
- Proofread: Carefully proofread for any remaining errors or typos.
- Format: Ensure your paper adheres to the required format, including title page, headers, font, and margins.
- Reference List: Double-check your bibliography, reference, or works cited page for accuracy.
- Submit: Make sure to submit your paper by the deadline.
In conclusion, a research paper is a formal academic document designed to provide a detailed analysis, interpretation, or argument based on in-depth study. Its structured format includes providing opening components, such as the abstract, outline, and introduction; study aspects, such as literature review, methodology, and results; analysis of findings, such as discussion, recommendations, and limitations; and final parts, such as conclusion, acknowledgments, appendices, and references. Understanding the essential elements and adhering to academic standards ensures the creation of a well-organized and meaningful research paper.
Busse, C., & August, E. (2020). How to write and publish a research paper for a peer-reviewed journal. Journal of Cancer Education , 36 (5), 909–913. https://doi.org/10.1007/s13187-020-01751-z
Goodson, P. (2024). Becoming an academic writer: 50 exercises for paced, productive, and powerful writing . Sage.
Graham, L., & McCoy, I. (2014). How to write a great research paper: A step-by-step handbook. Incentive Publications by World Book.
Scholz, F. (2022). Writing and publishing a scientific paper. ChemTexts , 8 (1), 1–7. https://doi.org/10.1007/s40828-022-00160-7
Turbek, S. P., Chock, T. M., Donahue, K., Havrilla, C. A., Oliverio, A. M., Polutchko, S. K., Shoemaker, L. G., & Vimercati, L. (2016). Scientific writing made easy: A step‐by‐step guide to undergraduate writing in the Biological Sciences. The Bulletin of the Ecological Society of America , 97 (4), 417–426. https://doi.org/10.1002/bes2.1258
Wankhade, L. (2018). How to write and publish a research paper: A complete guide to writing and publishing a research paper . Independent Published.

Want to create or adapt books like this? Learn more about how Pressbooks supports open publishing practices.
11.1 The Purpose of Research Writing
Learning objectives.
- Identify reasons to research writing projects.
- Outline the steps of the research writing process.
Why was the Great Wall of China built? What have scientists learned about the possibility of life on Mars? What roles did women play in the American Revolution? How does the human brain create, store, and retrieve memories? Who invented the game of football, and how has it changed over the years?
You may know the answers to these questions off the top of your head. If you are like most people, however, you find answers to tough questions like these by searching the Internet, visiting the library, or asking others for information. To put it simply, you perform research.
Whether you are a scientist, an artist, a paralegal, or a parent, you probably perform research in your everyday life. When your boss, your instructor, or a family member asks you a question that you do not know the answer to, you locate relevant information, analyze your findings, and share your results. Locating, analyzing, and sharing information are key steps in the research process, and in this chapter, you will learn more about each step. By developing your research writing skills, you will prepare yourself to answer any question no matter how challenging.
Reasons for Research
When you perform research, you are essentially trying to solve a mystery—you want to know how something works or why something happened. In other words, you want to answer a question that you (and other people) have about the world. This is one of the most basic reasons for performing research.
But the research process does not end when you have solved your mystery. Imagine what would happen if a detective collected enough evidence to solve a criminal case, but she never shared her solution with the authorities. Presenting what you have learned from research can be just as important as performing the research. Research results can be presented in a variety of ways, but one of the most popular—and effective—presentation forms is the research paper . A research paper presents an original thesis, or purpose statement, about a topic and develops that thesis with information gathered from a variety of sources.
If you are curious about the possibility of life on Mars, for example, you might choose to research the topic. What will you do, though, when your research is complete? You will need a way to put your thoughts together in a logical, coherent manner. You may want to use the facts you have learned to create a narrative or to support an argument. And you may want to show the results of your research to your friends, your teachers, or even the editors of magazines and journals. Writing a research paper is an ideal way to organize thoughts, craft narratives or make arguments based on research, and share your newfound knowledge with the world.
Write a paragraph about a time when you used research in your everyday life. Did you look for the cheapest way to travel from Houston to Denver? Did you search for a way to remove gum from the bottom of your shoe? In your paragraph, explain what you wanted to research, how you performed the research, and what you learned as a result.
Research Writing and the Academic Paper
No matter what field of study you are interested in, you will most likely be asked to write a research paper during your academic career. For example, a student in an art history course might write a research paper about an artist’s work. Similarly, a student in a psychology course might write a research paper about current findings in childhood development.
Having to write a research paper may feel intimidating at first. After all, researching and writing a long paper requires a lot of time, effort, and organization. However, writing a research paper can also be a great opportunity to explore a topic that is particularly interesting to you. The research process allows you to gain expertise on a topic of your choice, and the writing process helps you remember what you have learned and understand it on a deeper level.
Research Writing at Work
Knowing how to write a good research paper is a valuable skill that will serve you well throughout your career. Whether you are developing a new product, studying the best way to perform a procedure, or learning about challenges and opportunities in your field of employment, you will use research techniques to guide your exploration. You may even need to create a written report of your findings. And because effective communication is essential to any company, employers seek to hire people who can write clearly and professionally.
Writing at Work
Take a few minutes to think about each of the following careers. How might each of these professionals use researching and research writing skills on the job?
- Medical laboratory technician
- Small business owner
- Information technology professional
- Freelance magazine writer
A medical laboratory technician or information technology professional might do research to learn about the latest technological developments in either of these fields. A small business owner might conduct research to learn about the latest trends in his or her industry. A freelance magazine writer may need to research a given topic to write an informed, up-to-date article.
Think about the job of your dreams. How might you use research writing skills to perform that job? Create a list of ways in which strong researching, organizing, writing, and critical thinking skills could help you succeed at your dream job. How might these skills help you obtain that job?
Steps of the Research Writing Process
How does a research paper grow from a folder of brainstormed notes to a polished final draft? No two projects are identical, but most projects follow a series of six basic steps.
These are the steps in the research writing process:
- Choose a topic.
- Plan and schedule time to research and write.
- Conduct research.
- Organize research and ideas.
- Draft your paper.
- Revise and edit your paper.
Each of these steps will be discussed in more detail later in this chapter. For now, though, we will take a brief look at what each step involves.
Step 1: Choosing a Topic
As you may recall from Chapter 8 “The Writing Process: How Do I Begin?” , to narrow the focus of your topic, you may try freewriting exercises, such as brainstorming. You may also need to ask a specific research question —a broad, open-ended question that will guide your research—as well as propose a possible answer, or a working thesis . You may use your research question and your working thesis to create a research proposal . In a research proposal, you present your main research question, any related subquestions you plan to explore, and your working thesis.
Step 2: Planning and Scheduling
Before you start researching your topic, take time to plan your researching and writing schedule. Research projects can take days, weeks, or even months to complete. Creating a schedule is a good way to ensure that you do not end up being overwhelmed by all the work you have to do as the deadline approaches.
During this step of the process, it is also a good idea to plan the resources and organizational tools you will use to keep yourself on track throughout the project. Flowcharts, calendars, and checklists can all help you stick to your schedule. See Chapter 11 “Writing from Research: What Will I Learn?” , Section 11.2 “Steps in Developing a Research Proposal” for an example of a research schedule.
Step 3: Conducting Research
When going about your research, you will likely use a variety of sources—anything from books and periodicals to video presentations and in-person interviews.
Your sources will include both primary sources and secondary sources . Primary sources provide firsthand information or raw data. For example, surveys, in-person interviews, and historical documents are primary sources. Secondary sources, such as biographies, literary reviews, or magazine articles, include some analysis or interpretation of the information presented. As you conduct research, you will take detailed, careful notes about your discoveries. You will also evaluate the reliability of each source you find.
Step 4: Organizing Research and the Writer’s Ideas
When your research is complete, you will organize your findings and decide which sources to cite in your paper. You will also have an opportunity to evaluate the evidence you have collected and determine whether it supports your thesis, or the focus of your paper. You may decide to adjust your thesis or conduct additional research to ensure that your thesis is well supported.
Remember, your working thesis is not set in stone. You can and should change your working thesis throughout the research writing process if the evidence you find does not support your original thesis. Never try to force evidence to fit your argument. For example, your working thesis is “Mars cannot support life-forms.” Yet, a week into researching your topic, you find an article in the New York Times detailing new findings of bacteria under the Martian surface. Instead of trying to argue that bacteria are not life forms, you might instead alter your thesis to “Mars cannot support complex life-forms.”
Step 5: Drafting Your Paper
Now you are ready to combine your research findings with your critical analysis of the results in a rough draft. You will incorporate source materials into your paper and discuss each source thoughtfully in relation to your thesis or purpose statement.
When you cite your reference sources, it is important to pay close attention to standard conventions for citing sources in order to avoid plagiarism , or the practice of using someone else’s words without acknowledging the source. Later in this chapter, you will learn how to incorporate sources in your paper and avoid some of the most common pitfalls of attributing information.
Step 6: Revising and Editing Your Paper
In the final step of the research writing process, you will revise and polish your paper. You might reorganize your paper’s structure or revise for unity and cohesion, ensuring that each element in your paper flows into the next logically and naturally. You will also make sure that your paper uses an appropriate and consistent tone.
Once you feel confident in the strength of your writing, you will edit your paper for proper spelling, grammar, punctuation, mechanics, and formatting. When you complete this final step, you will have transformed a simple idea or question into a thoroughly researched and well-written paper you can be proud of!
Review the steps of the research writing process. Then answer the questions on your own sheet of paper.
- In which steps of the research writing process are you allowed to change your thesis?
- In step 2, which types of information should you include in your project schedule?
- What might happen if you eliminated step 4 from the research writing process?
Key Takeaways
- People undertake research projects throughout their academic and professional careers in order to answer specific questions, share their findings with others, increase their understanding of challenging topics, and strengthen their researching, writing, and analytical skills.
- The research writing process generally comprises six steps: choosing a topic, scheduling and planning time for research and writing, conducting research, organizing research and ideas, drafting a paper, and revising and editing the paper.
Writing for Success Copyright © 2015 by University of Minnesota is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License , except where otherwise noted.
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
Genre and the Research Paper

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
Research: What it is.
A research paper is the culmination and final product of an involved process of research, critical thinking, source evaluation, organization, and composition. It is, perhaps, helpful to think of the research paper as a living thing, which grows and changes as the student explores, interprets, and evaluates sources related to a specific topic. Primary and secondary sources are the heart of a research paper, and provide its nourishment; without the support of and interaction with these sources, the research paper would morph into a different genre of writing (e.g., an encyclopedic article). The research paper serves not only to further the field in which it is written, but also to provide the student with an exceptional opportunity to increase her knowledge in that field. It is also possible to identify a research paper by what it is not.
Research: What it is not.
A research paper is not simply an informed summary of a topic by means of primary and secondary sources. It is neither a book report nor an opinion piece nor an expository essay consisting solely of one's interpretation of a text nor an overview of a particular topic. Instead, it is a genre that requires one to spend time investigating and evaluating sources with the intent to offer interpretations of the texts, and not unconscious regurgitations of those sources. The goal of a research paper is not to inform the reader what others have to say about a topic, but to draw on what others have to say about a topic and engage the sources in order to thoughtfully offer a unique perspective on the issue at hand. This is accomplished through two major types of research papers.
Two major types of research papers.
Argumentative research paper:
The argumentative research paper consists of an introduction in which the writer clearly introduces the topic and informs his audience exactly which stance he intends to take; this stance is often identified as the thesis statement . An important goal of the argumentative research paper is persuasion, which means the topic chosen should be debatable or controversial. For example, it would be difficult for a student to successfully argue in favor of the following stance.
Perhaps 25 years ago this topic would have been debatable; however, today, it is assumed that smoking cigarettes is, indeed, harmful to one's health. A better thesis would be the following.
In this sentence, the writer is not challenging the current accepted stance that both firsthand and secondhand cigarette smoke is dangerous; rather, she is positing that the social acceptance of the latter over the former is indicative of a cultural double-standard of sorts. The student would support this thesis throughout her paper by means of both primary and secondary sources, with the intent to persuade her audience that her particular interpretation of the situation is viable.
Analytical research paper:
The analytical research paper often begins with the student asking a question (a.k.a. a research question) on which he has taken no stance. Such a paper is often an exercise in exploration and evaluation. For example, perhaps one is interested in the Old English poem Beowulf . He has read the poem intently and desires to offer a fresh reading of the poem to the academic community. His question may be as follows.
His research may lead him to the following conclusion.
Though his topic may be debatable and controversial, it is not the student's intent to persuade the audience that his ideas are right while those of others are wrong. Instead, his goal is to offer a critical interpretation of primary and secondary sources throughout the paper--sources that should, ultimately, buttress his particular analysis of the topic. The following is an example of what his thesis statement may look like once he has completed his research.
This statement does not negate the traditional readings of Beowulf ; instead, it offers a fresh and detailed reading of the poem that will be supported by the student's research.
It is typically not until the student has begun the writing process that his thesis statement begins to take solid form. In fact, the thesis statement in an analytical paper is often more fluid than the thesis in an argumentative paper. Such is one of the benefits of approaching the topic without a predetermined stance.
- Privacy Policy

Home » Research Paper Introduction – Writing Guide and Examples
Research Paper Introduction – Writing Guide and Examples
Table of Contents

Research Paper Introduction
Research paper introduction is the first section of a research paper that provides an overview of the study, its purpose, and the research question (s) or hypothesis (es) being investigated. It typically includes background information about the topic, a review of previous research in the field, and a statement of the research objectives. The introduction is intended to provide the reader with a clear understanding of the research problem, why it is important, and how the study will contribute to existing knowledge in the field. It also sets the tone for the rest of the paper and helps to establish the author’s credibility and expertise on the subject.
How to Write Research Paper Introduction
Writing an introduction for a research paper can be challenging because it sets the tone for the entire paper. Here are some steps to follow to help you write an effective research paper introduction:
- Start with a hook : Begin your introduction with an attention-grabbing statement, a question, or a surprising fact that will make the reader interested in reading further.
- Provide background information: After the hook, provide background information on the topic. This information should give the reader a general idea of what the topic is about and why it is important.
- State the research problem: Clearly state the research problem or question that the paper addresses. This should be done in a concise and straightforward manner.
- State the research objectives: After stating the research problem, clearly state the research objectives. This will give the reader an idea of what the paper aims to achieve.
- Provide a brief overview of the paper: At the end of the introduction, provide a brief overview of the paper. This should include a summary of the main points that will be discussed in the paper.
- Revise and refine: Finally, revise and refine your introduction to ensure that it is clear, concise, and engaging.
Structure of Research Paper Introduction
The following is a typical structure for a research paper introduction:
- Background Information: This section provides an overview of the topic of the research paper, including relevant background information and any previous research that has been done on the topic. It helps to give the reader a sense of the context for the study.
- Problem Statement: This section identifies the specific problem or issue that the research paper is addressing. It should be clear and concise, and it should articulate the gap in knowledge that the study aims to fill.
- Research Question/Hypothesis : This section states the research question or hypothesis that the study aims to answer. It should be specific and focused, and it should clearly connect to the problem statement.
- Significance of the Study: This section explains why the research is important and what the potential implications of the study are. It should highlight the contribution that the research makes to the field.
- Methodology: This section describes the research methods that were used to conduct the study. It should be detailed enough to allow the reader to understand how the study was conducted and to evaluate the validity of the results.
- Organization of the Paper : This section provides a brief overview of the structure of the research paper. It should give the reader a sense of what to expect in each section of the paper.
Research Paper Introduction Examples
Research Paper Introduction Examples could be:
Example 1: In recent years, the use of artificial intelligence (AI) has become increasingly prevalent in various industries, including healthcare. AI algorithms are being developed to assist with medical diagnoses, treatment recommendations, and patient monitoring. However, as the use of AI in healthcare grows, ethical concerns regarding privacy, bias, and accountability have emerged. This paper aims to explore the ethical implications of AI in healthcare and propose recommendations for addressing these concerns.
Example 2: Climate change is one of the most pressing issues facing our planet today. The increasing concentration of greenhouse gases in the atmosphere has resulted in rising temperatures, changing weather patterns, and other environmental impacts. In this paper, we will review the scientific evidence on climate change, discuss the potential consequences of inaction, and propose solutions for mitigating its effects.
Example 3: The rise of social media has transformed the way we communicate and interact with each other. While social media platforms offer many benefits, including increased connectivity and access to information, they also present numerous challenges. In this paper, we will examine the impact of social media on mental health, privacy, and democracy, and propose solutions for addressing these issues.
Example 4: The use of renewable energy sources has become increasingly important in the face of climate change and environmental degradation. While renewable energy technologies offer many benefits, including reduced greenhouse gas emissions and energy independence, they also present numerous challenges. In this paper, we will assess the current state of renewable energy technology, discuss the economic and political barriers to its adoption, and propose solutions for promoting the widespread use of renewable energy.
Purpose of Research Paper Introduction
The introduction section of a research paper serves several important purposes, including:
- Providing context: The introduction should give readers a general understanding of the topic, including its background, significance, and relevance to the field.
- Presenting the research question or problem: The introduction should clearly state the research question or problem that the paper aims to address. This helps readers understand the purpose of the study and what the author hopes to accomplish.
- Reviewing the literature: The introduction should summarize the current state of knowledge on the topic, highlighting the gaps and limitations in existing research. This shows readers why the study is important and necessary.
- Outlining the scope and objectives of the study: The introduction should describe the scope and objectives of the study, including what aspects of the topic will be covered, what data will be collected, and what methods will be used.
- Previewing the main findings and conclusions : The introduction should provide a brief overview of the main findings and conclusions that the study will present. This helps readers anticipate what they can expect to learn from the paper.
When to Write Research Paper Introduction
The introduction of a research paper is typically written after the research has been conducted and the data has been analyzed. This is because the introduction should provide an overview of the research problem, the purpose of the study, and the research questions or hypotheses that will be investigated.
Once you have a clear understanding of the research problem and the questions that you want to explore, you can begin to write the introduction. It’s important to keep in mind that the introduction should be written in a way that engages the reader and provides a clear rationale for the study. It should also provide context for the research by reviewing relevant literature and explaining how the study fits into the larger field of research.
Advantages of Research Paper Introduction
The introduction of a research paper has several advantages, including:
- Establishing the purpose of the research: The introduction provides an overview of the research problem, question, or hypothesis, and the objectives of the study. This helps to clarify the purpose of the research and provide a roadmap for the reader to follow.
- Providing background information: The introduction also provides background information on the topic, including a review of relevant literature and research. This helps the reader understand the context of the study and how it fits into the broader field of research.
- Demonstrating the significance of the research: The introduction also explains why the research is important and relevant. This helps the reader understand the value of the study and why it is worth reading.
- Setting expectations: The introduction sets the tone for the rest of the paper and prepares the reader for what is to come. This helps the reader understand what to expect and how to approach the paper.
- Grabbing the reader’s attention: A well-written introduction can grab the reader’s attention and make them interested in reading further. This is important because it can help to keep the reader engaged and motivated to read the rest of the paper.
- Creating a strong first impression: The introduction is the first part of the research paper that the reader will see, and it can create a strong first impression. A well-written introduction can make the reader more likely to take the research seriously and view it as credible.
- Establishing the author’s credibility: The introduction can also establish the author’s credibility as a researcher. By providing a clear and thorough overview of the research problem and relevant literature, the author can demonstrate their expertise and knowledge in the field.
- Providing a structure for the paper: The introduction can also provide a structure for the rest of the paper. By outlining the main sections and sub-sections of the paper, the introduction can help the reader navigate the paper and find the information they are looking for.
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

Research Design – Types, Methods and Examples

Context of the Study – Writing Guide and Examples

Figures in Research Paper – Examples and Guide

Research Objectives – Types, Examples and...

Ethical Considerations – Types, Examples and...

Delimitations in Research – Types, Examples and...
Canvas | University | Ask a Librarian
- Library Homepage
- Arrendale Library
Writing a Research Paper
Types of research papers.
- About This Guide
- Choosing a Topic
- Writing a Thesis Statement
- Gathering Research
- Journals and Magazines This link opens in a new window
- Creating an Outline
- Writing Your Paper
- Citing Resources
- Academic Integrity This link opens in a new window
- Contact Us!
Call us at 706-776-0111
Chat with a Librarian
Send Us Email
Library Hours
Although research paper assignments may vary widely, there are essentially two basic types of research papers. These are argumentative and analytical .
Argumentative
In an argumentative research paper, a student both states the topic they will be exploring and immediately establishes the position they will argue regarding that topic in a thesis statement . This type of paper hopes to persuade its reader to adopt the view presented.
Example : a paper that argues the merits of early exposure to reading for children would be an argumentative essay.
An analytical research paper states the topic that the writer will be exploring, usually in the form of a question, initially taking a neutral stance. The body of the paper will present multifaceted information and, ultimately, the writer will state their conclusion, based on the information that has unfolded throughout the course of the essay. This type of paper hopes to offer a well-supported critical analysis without necessarily persuading the reader to any particular way of thinking.
Example : a paper that explores the use of metaphor in one of Shakespeare's sonnets would be an example of an analytical essay.
*Please note that this LibGuide will primarily be concerning itself with argumentative or rhetorical research papers.
- << Previous: About This Guide
- Next: Choosing a Topic >>
- Last Updated: May 16, 2024 10:46 AM
- URL: https://library.piedmont.edu/research_paper
- Ebooks & Online Video
- New Materials
- Renew Checkouts
- Faculty Resources
- Library Friends
- Library Services
- Our Mission
- Library History
- Ask a Librarian!
- Making Citations
- Working Online
Arrendale Library Piedmont University 706-776-0111
All Formats
Table of Contents
Research paper definition & meaning, what is a research paper, 10 types of research papers, research paper review, research paper uses, purpose, importance, what’s in a research paper, how to design a research paper, research paper vs. argumentative essay, what’s the difference between research paper, thesis, and proposal, research paper sizes, research paper ideas & examples, research paper.
A research paper is an important document that is widely used by students and academics. It is a common requirement needed to pass a certain course or subject.

Research Paper Report
College Research Paper

APA Research Paper

Career Research Paper
Quantitative Research Paper

Conclusion Research Paper
Legal Research Paper
Research Paper Format

Business Research Paper

Enhance One’s Writing Skills
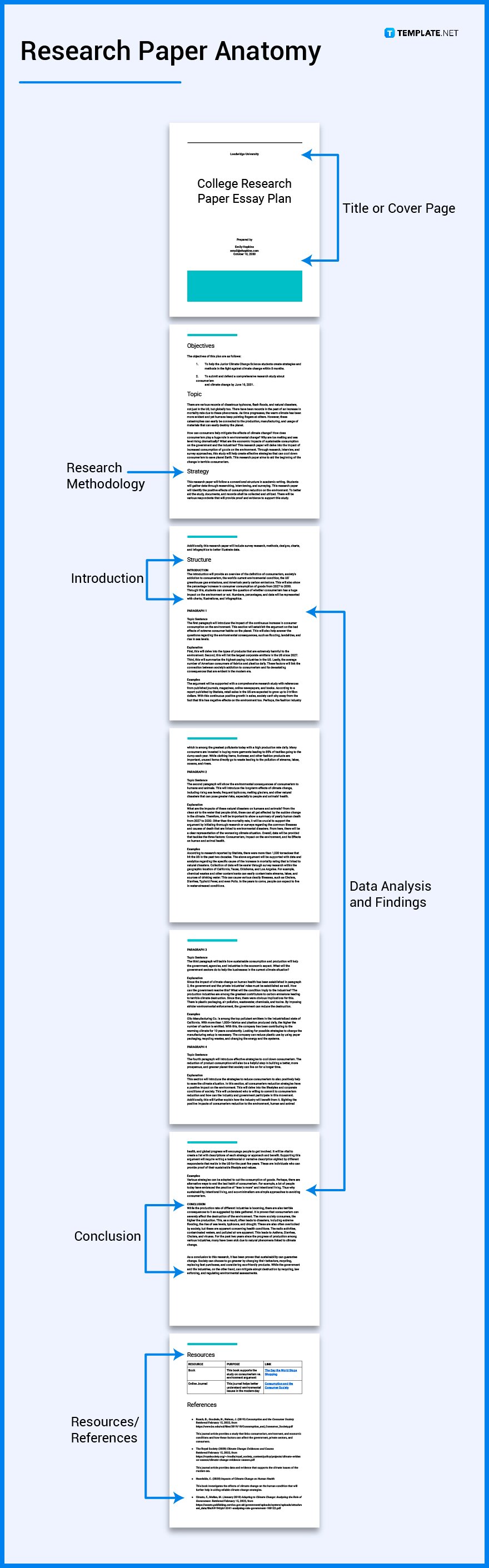
Provide feedback and insights, research skills, originality, builds confidence in handling complicated tasks, title or cover page, introduction, literature review, research methodology, data analysis and findings, resources/references.
- Research Paper Outline Ideas and Examples
- Research Paper Proposal Ideas and Examples
- Formal Research Paper Ideas and Examples
- Simple Research Paper Ideas and Examples
- Market Research White Paper Ideas and Examples
- Research Paper Table of Contents Ideas and Examples
- Covid 19 Research Paper Essay Ideas and Examples
- Research Paper Rubric Ideas and Examples
- Career Research Paper Essay Ideas and Examples
- Research Paper Essay Format Ideas and Examples
What should be included in a research paper?
What is the role of a research paper in business, what are the steps to writing a research paper, what is a mini-research paper, how do you properly cite a research paper, what is a qualitative research paper, what is the role of a research paper, what person are research papers written in, what are the common research paper issues and problems, why research paper is important to students, more in documents.
School Essay Template
Reflective essay template, interview essay in apa documentation style template, job interview essay report with introduction template, professional student interview essay template, orientation speech, closing ceremony speech template for event, business comparative research template, comparative market research template, comparative research outline template.
- How To Create a Schedule in Microsoft Word [Template + Example]
- How To Create a Schedule in Google Docs [Template + Example]
- How To Create a Quotation in Google Docs [Template + Example]
- How To Create a Quotation in Microsoft Word [Template + Example]
- How To Make a Plan in Google Docs [Template + Example]
- How To Make a Plan in Microsoft Word [Template + Example]
- How To Make/Create an Inventory in Google Docs [Templates + Examples]
- How To Create Meeting Minutes in Microsoft Word [Template + Example]
- How To Create Meeting Minutes in Google Docs [Template + Example]
- How To Make/Create an Estimate in Microsoft Word [Templates + Examples] 2023
- How To Make/Create an Estimate in Google Docs [Templates + Examples] 2023
- How To Make/Create a Manual in Google Docs [Templates + Examples] 2023
- How To Make/Create a Manual in Microsoft Word [Templates + Examples] 2023
- How To Make/Create a Statement in Google Docs [Templates + Examples] 2023
- How To Make/Create a Statement in Microsoft Word [Templates + Examples] 2023
File Formats
Word templates, google docs templates, excel templates, powerpoint templates, google sheets templates, google slides templates, pdf templates, publisher templates, psd templates, indesign templates, illustrator templates, pages templates, keynote templates, numbers templates, outlook templates.
- USC Libraries
- Research Guides
Organizing Your Social Sciences Research Paper
- 8. The Discussion
- Purpose of Guide
- Design Flaws to Avoid
- Independent and Dependent Variables
- Glossary of Research Terms
- Reading Research Effectively
- Narrowing a Topic Idea
- Broadening a Topic Idea
- Extending the Timeliness of a Topic Idea
- Academic Writing Style
- Applying Critical Thinking
- Choosing a Title
- Making an Outline
- Paragraph Development
- Research Process Video Series
- Executive Summary
- The C.A.R.S. Model
- Background Information
- The Research Problem/Question
- Theoretical Framework
- Citation Tracking
- Content Alert Services
- Evaluating Sources
- Primary Sources
- Secondary Sources
- Tiertiary Sources
- Scholarly vs. Popular Publications
- Qualitative Methods
- Quantitative Methods
- Insiderness
- Using Non-Textual Elements
- Limitations of the Study
- Common Grammar Mistakes
- Writing Concisely
- Avoiding Plagiarism
- Footnotes or Endnotes?
- Further Readings
- Generative AI and Writing
- USC Libraries Tutorials and Other Guides
- Bibliography
The purpose of the discussion section is to interpret and describe the significance of your findings in relation to what was already known about the research problem being investigated and to explain any new understanding or insights that emerged as a result of your research. The discussion will always connect to the introduction by way of the research questions or hypotheses you posed and the literature you reviewed, but the discussion does not simply repeat or rearrange the first parts of your paper; the discussion clearly explains how your study advanced the reader's understanding of the research problem from where you left them at the end of your review of prior research.
Annesley, Thomas M. “The Discussion Section: Your Closing Argument.” Clinical Chemistry 56 (November 2010): 1671-1674; Peacock, Matthew. “Communicative Moves in the Discussion Section of Research Articles.” System 30 (December 2002): 479-497.
Importance of a Good Discussion
The discussion section is often considered the most important part of your research paper because it:
- Most effectively demonstrates your ability as a researcher to think critically about an issue, to develop creative solutions to problems based upon a logical synthesis of the findings, and to formulate a deeper, more profound understanding of the research problem under investigation;
- Presents the underlying meaning of your research, notes possible implications in other areas of study, and explores possible improvements that can be made in order to further develop the concerns of your research;
- Highlights the importance of your study and how it can contribute to understanding the research problem within the field of study;
- Presents how the findings from your study revealed and helped fill gaps in the literature that had not been previously exposed or adequately described; and,
- Engages the reader in thinking critically about issues based on an evidence-based interpretation of findings; it is not governed strictly by objective reporting of information.
Annesley Thomas M. “The Discussion Section: Your Closing Argument.” Clinical Chemistry 56 (November 2010): 1671-1674; Bitchener, John and Helen Basturkmen. “Perceptions of the Difficulties of Postgraduate L2 Thesis Students Writing the Discussion Section.” Journal of English for Academic Purposes 5 (January 2006): 4-18; Kretchmer, Paul. Fourteen Steps to Writing an Effective Discussion Section. San Francisco Edit, 2003-2008.
Structure and Writing Style
I. General Rules
These are the general rules you should adopt when composing your discussion of the results :
- Do not be verbose or repetitive; be concise and make your points clearly
- Avoid the use of jargon or undefined technical language
- Follow a logical stream of thought; in general, interpret and discuss the significance of your findings in the same sequence you described them in your results section [a notable exception is to begin by highlighting an unexpected result or a finding that can grab the reader's attention]
- Use the present verb tense, especially for established facts; however, refer to specific works or prior studies in the past tense
- If needed, use subheadings to help organize your discussion or to categorize your interpretations into themes
II. The Content
The content of the discussion section of your paper most often includes :
- Explanation of results : Comment on whether or not the results were expected for each set of findings; go into greater depth to explain findings that were unexpected or especially profound. If appropriate, note any unusual or unanticipated patterns or trends that emerged from your results and explain their meaning in relation to the research problem.
- References to previous research : Either compare your results with the findings from other studies or use the studies to support a claim. This can include re-visiting key sources already cited in your literature review section, or, save them to cite later in the discussion section if they are more important to compare with your results instead of being a part of the general literature review of prior research used to provide context and background information. Note that you can make this decision to highlight specific studies after you have begun writing the discussion section.
- Deduction : A claim for how the results can be applied more generally. For example, describing lessons learned, proposing recommendations that can help improve a situation, or highlighting best practices.
- Hypothesis : A more general claim or possible conclusion arising from the results [which may be proved or disproved in subsequent research]. This can be framed as new research questions that emerged as a consequence of your analysis.
III. Organization and Structure
Keep the following sequential points in mind as you organize and write the discussion section of your paper:
- Think of your discussion as an inverted pyramid. Organize the discussion from the general to the specific, linking your findings to the literature, then to theory, then to practice [if appropriate].
- Use the same key terms, narrative style, and verb tense [present] that you used when describing the research problem in your introduction.
- Begin by briefly re-stating the research problem you were investigating and answer all of the research questions underpinning the problem that you posed in the introduction.
- Describe the patterns, principles, and relationships shown by each major findings and place them in proper perspective. The sequence of this information is important; first state the answer, then the relevant results, then cite the work of others. If appropriate, refer the reader to a figure or table to help enhance the interpretation of the data [either within the text or as an appendix].
- Regardless of where it's mentioned, a good discussion section includes analysis of any unexpected findings. This part of the discussion should begin with a description of the unanticipated finding, followed by a brief interpretation as to why you believe it appeared and, if necessary, its possible significance in relation to the overall study. If more than one unexpected finding emerged during the study, describe each of them in the order they appeared as you gathered or analyzed the data. As noted, the exception to discussing findings in the same order you described them in the results section would be to begin by highlighting the implications of a particularly unexpected or significant finding that emerged from the study, followed by a discussion of the remaining findings.
- Before concluding the discussion, identify potential limitations and weaknesses if you do not plan to do so in the conclusion of the paper. Comment on their relative importance in relation to your overall interpretation of the results and, if necessary, note how they may affect the validity of your findings. Avoid using an apologetic tone; however, be honest and self-critical [e.g., in retrospect, had you included a particular question in a survey instrument, additional data could have been revealed].
- The discussion section should end with a concise summary of the principal implications of the findings regardless of their significance. Give a brief explanation about why you believe the findings and conclusions of your study are important and how they support broader knowledge or understanding of the research problem. This can be followed by any recommendations for further research. However, do not offer recommendations which could have been easily addressed within the study. This would demonstrate to the reader that you have inadequately examined and interpreted the data.
IV. Overall Objectives
The objectives of your discussion section should include the following: I. Reiterate the Research Problem/State the Major Findings
Briefly reiterate the research problem or problems you are investigating and the methods you used to investigate them, then move quickly to describe the major findings of the study. You should write a direct, declarative, and succinct proclamation of the study results, usually in one paragraph.
II. Explain the Meaning of the Findings and Why They are Important
No one has thought as long and hard about your study as you have. Systematically explain the underlying meaning of your findings and state why you believe they are significant. After reading the discussion section, you want the reader to think critically about the results and why they are important. You don’t want to force the reader to go through the paper multiple times to figure out what it all means. If applicable, begin this part of the section by repeating what you consider to be your most significant or unanticipated finding first, then systematically review each finding. Otherwise, follow the general order you reported the findings presented in the results section.
III. Relate the Findings to Similar Studies
No study in the social sciences is so novel or possesses such a restricted focus that it has absolutely no relation to previously published research. The discussion section should relate your results to those found in other studies, particularly if questions raised from prior studies served as the motivation for your research. This is important because comparing and contrasting the findings of other studies helps to support the overall importance of your results and it highlights how and in what ways your study differs from other research about the topic. Note that any significant or unanticipated finding is often because there was no prior research to indicate the finding could occur. If there is prior research to indicate this, you need to explain why it was significant or unanticipated. IV. Consider Alternative Explanations of the Findings
It is important to remember that the purpose of research in the social sciences is to discover and not to prove . When writing the discussion section, you should carefully consider all possible explanations for the study results, rather than just those that fit your hypothesis or prior assumptions and biases. This is especially important when describing the discovery of significant or unanticipated findings.
V. Acknowledge the Study’s Limitations
It is far better for you to identify and acknowledge your study’s limitations than to have them pointed out by your professor! Note any unanswered questions or issues your study could not address and describe the generalizability of your results to other situations. If a limitation is applicable to the method chosen to gather information, then describe in detail the problems you encountered and why. VI. Make Suggestions for Further Research
You may choose to conclude the discussion section by making suggestions for further research [as opposed to offering suggestions in the conclusion of your paper]. Although your study can offer important insights about the research problem, this is where you can address other questions related to the problem that remain unanswered or highlight hidden issues that were revealed as a result of conducting your research. You should frame your suggestions by linking the need for further research to the limitations of your study [e.g., in future studies, the survey instrument should include more questions that ask..."] or linking to critical issues revealed from the data that were not considered initially in your research.
NOTE: Besides the literature review section, the preponderance of references to sources is usually found in the discussion section . A few historical references may be helpful for perspective, but most of the references should be relatively recent and included to aid in the interpretation of your results, to support the significance of a finding, and/or to place a finding within a particular context. If a study that you cited does not support your findings, don't ignore it--clearly explain why your research findings differ from theirs.
V. Problems to Avoid
- Do not waste time restating your results . Should you need to remind the reader of a finding to be discussed, use "bridge sentences" that relate the result to the interpretation. An example would be: “In the case of determining available housing to single women with children in rural areas of Texas, the findings suggest that access to good schools is important...," then move on to further explaining this finding and its implications.
- As noted, recommendations for further research can be included in either the discussion or conclusion of your paper, but do not repeat your recommendations in the both sections. Think about the overall narrative flow of your paper to determine where best to locate this information. However, if your findings raise a lot of new questions or issues, consider including suggestions for further research in the discussion section.
- Do not introduce new results in the discussion section. Be wary of mistaking the reiteration of a specific finding for an interpretation because it may confuse the reader. The description of findings [results section] and the interpretation of their significance [discussion section] should be distinct parts of your paper. If you choose to combine the results section and the discussion section into a single narrative, you must be clear in how you report the information discovered and your own interpretation of each finding. This approach is not recommended if you lack experience writing college-level research papers.
- Use of the first person pronoun is generally acceptable. Using first person singular pronouns can help emphasize a point or illustrate a contrasting finding. However, keep in mind that too much use of the first person can actually distract the reader from the main points [i.e., I know you're telling me this--just tell me!].
Analyzing vs. Summarizing. Department of English Writing Guide. George Mason University; Discussion. The Structure, Format, Content, and Style of a Journal-Style Scientific Paper. Department of Biology. Bates College; Hess, Dean R. "How to Write an Effective Discussion." Respiratory Care 49 (October 2004); Kretchmer, Paul. Fourteen Steps to Writing to Writing an Effective Discussion Section. San Francisco Edit, 2003-2008; The Lab Report. University College Writing Centre. University of Toronto; Sauaia, A. et al. "The Anatomy of an Article: The Discussion Section: "How Does the Article I Read Today Change What I Will Recommend to my Patients Tomorrow?” The Journal of Trauma and Acute Care Surgery 74 (June 2013): 1599-1602; Research Limitations & Future Research . Lund Research Ltd., 2012; Summary: Using it Wisely. The Writing Center. University of North Carolina; Schafer, Mickey S. Writing the Discussion. Writing in Psychology course syllabus. University of Florida; Yellin, Linda L. A Sociology Writer's Guide . Boston, MA: Allyn and Bacon, 2009.
Writing Tip
Don’t Over-Interpret the Results!
Interpretation is a subjective exercise. As such, you should always approach the selection and interpretation of your findings introspectively and to think critically about the possibility of judgmental biases unintentionally entering into discussions about the significance of your work. With this in mind, be careful that you do not read more into the findings than can be supported by the evidence you have gathered. Remember that the data are the data: nothing more, nothing less.
MacCoun, Robert J. "Biases in the Interpretation and Use of Research Results." Annual Review of Psychology 49 (February 1998): 259-287; Ward, Paulet al, editors. The Oxford Handbook of Expertise . Oxford, UK: Oxford University Press, 2018.
Another Writing Tip
Don't Write Two Results Sections!
One of the most common mistakes that you can make when discussing the results of your study is to present a superficial interpretation of the findings that more or less re-states the results section of your paper. Obviously, you must refer to your results when discussing them, but focus on the interpretation of those results and their significance in relation to the research problem, not the data itself.
Azar, Beth. "Discussing Your Findings." American Psychological Association gradPSYCH Magazine (January 2006).
Yet Another Writing Tip
Avoid Unwarranted Speculation!
The discussion section should remain focused on the findings of your study. For example, if the purpose of your research was to measure the impact of foreign aid on increasing access to education among disadvantaged children in Bangladesh, it would not be appropriate to speculate about how your findings might apply to populations in other countries without drawing from existing studies to support your claim or if analysis of other countries was not a part of your original research design. If you feel compelled to speculate, do so in the form of describing possible implications or explaining possible impacts. Be certain that you clearly identify your comments as speculation or as a suggestion for where further research is needed. Sometimes your professor will encourage you to expand your discussion of the results in this way, while others don’t care what your opinion is beyond your effort to interpret the data in relation to the research problem.
- << Previous: Using Non-Textual Elements
- Next: Limitations of the Study >>
- Last Updated: Aug 13, 2024 12:57 PM
- URL: https://libguides.usc.edu/writingguide
Have a language expert improve your writing
Run a free plagiarism check in 10 minutes, generate accurate citations for free.
- Knowledge Base
Methodology

Research Methods | Definitions, Types, Examples
Research methods are specific procedures for collecting and analyzing data. Developing your research methods is an integral part of your research design . When planning your methods, there are two key decisions you will make.
First, decide how you will collect data . Your methods depend on what type of data you need to answer your research question :
- Qualitative vs. quantitative : Will your data take the form of words or numbers?
- Primary vs. secondary : Will you collect original data yourself, or will you use data that has already been collected by someone else?
- Descriptive vs. experimental : Will you take measurements of something as it is, or will you perform an experiment?
Second, decide how you will analyze the data .
- For quantitative data, you can use statistical analysis methods to test relationships between variables.
- For qualitative data, you can use methods such as thematic analysis to interpret patterns and meanings in the data.
Table of contents
Methods for collecting data, examples of data collection methods, methods for analyzing data, examples of data analysis methods, other interesting articles, frequently asked questions about research methods.
Data is the information that you collect for the purposes of answering your research question . The type of data you need depends on the aims of your research.
Qualitative vs. quantitative data
Your choice of qualitative or quantitative data collection depends on the type of knowledge you want to develop.
For questions about ideas, experiences and meanings, or to study something that can’t be described numerically, collect qualitative data .
If you want to develop a more mechanistic understanding of a topic, or your research involves hypothesis testing , collect quantitative data .
| Qualitative | to broader populations. . | |
|---|---|---|
| Quantitative | . |
You can also take a mixed methods approach , where you use both qualitative and quantitative research methods.
Primary vs. secondary research
Primary research is any original data that you collect yourself for the purposes of answering your research question (e.g. through surveys , observations and experiments ). Secondary research is data that has already been collected by other researchers (e.g. in a government census or previous scientific studies).
If you are exploring a novel research question, you’ll probably need to collect primary data . But if you want to synthesize existing knowledge, analyze historical trends, or identify patterns on a large scale, secondary data might be a better choice.
| Primary | . | methods. |
|---|---|---|
| Secondary |
Descriptive vs. experimental data
In descriptive research , you collect data about your study subject without intervening. The validity of your research will depend on your sampling method .
In experimental research , you systematically intervene in a process and measure the outcome. The validity of your research will depend on your experimental design .
To conduct an experiment, you need to be able to vary your independent variable , precisely measure your dependent variable, and control for confounding variables . If it’s practically and ethically possible, this method is the best choice for answering questions about cause and effect.
| Descriptive | . . | |
|---|---|---|
| Experimental |
Receive feedback on language, structure, and formatting
Professional editors proofread and edit your paper by focusing on:
- Academic style
- Vague sentences
- Style consistency
See an example
| Research method | Primary or secondary? | Qualitative or quantitative? | When to use |
|---|---|---|---|
| Primary | Quantitative | To test cause-and-effect relationships. | |
| Primary | Quantitative | To understand general characteristics of a population. | |
| Interview/focus group | Primary | Qualitative | To gain more in-depth understanding of a topic. |
| Observation | Primary | Either | To understand how something occurs in its natural setting. |
| Secondary | Either | To situate your research in an existing body of work, or to evaluate trends within a research topic. | |
| Either | Either | To gain an in-depth understanding of a specific group or context, or when you don’t have the resources for a large study. |
Your data analysis methods will depend on the type of data you collect and how you prepare it for analysis.
Data can often be analyzed both quantitatively and qualitatively. For example, survey responses could be analyzed qualitatively by studying the meanings of responses or quantitatively by studying the frequencies of responses.
Qualitative analysis methods
Qualitative analysis is used to understand words, ideas, and experiences. You can use it to interpret data that was collected:
- From open-ended surveys and interviews , literature reviews , case studies , ethnographies , and other sources that use text rather than numbers.
- Using non-probability sampling methods .
Qualitative analysis tends to be quite flexible and relies on the researcher’s judgement, so you have to reflect carefully on your choices and assumptions and be careful to avoid research bias .
Quantitative analysis methods
Quantitative analysis uses numbers and statistics to understand frequencies, averages and correlations (in descriptive studies) or cause-and-effect relationships (in experiments).
You can use quantitative analysis to interpret data that was collected either:
- During an experiment .
- Using probability sampling methods .
Because the data is collected and analyzed in a statistically valid way, the results of quantitative analysis can be easily standardized and shared among researchers.
| Research method | Qualitative or quantitative? | When to use |
|---|---|---|
| Quantitative | To analyze data collected in a statistically valid manner (e.g. from experiments, surveys, and observations). | |
| Meta-analysis | Quantitative | To statistically analyze the results of a large collection of studies. Can only be applied to studies that collected data in a statistically valid manner. |
| Qualitative | To analyze data collected from interviews, , or textual sources. To understand general themes in the data and how they are communicated. | |
| Either | To analyze large volumes of textual or visual data collected from surveys, literature reviews, or other sources. Can be quantitative (i.e. frequencies of words) or qualitative (i.e. meanings of words). |
Prevent plagiarism. Run a free check.
If you want to know more about statistics , methodology , or research bias , make sure to check out some of our other articles with explanations and examples.
- Chi square test of independence
- Statistical power
- Descriptive statistics
- Degrees of freedom
- Pearson correlation
- Null hypothesis
- Double-blind study
- Case-control study
- Research ethics
- Data collection
- Hypothesis testing
- Structured interviews
Research bias
- Hawthorne effect
- Unconscious bias
- Recall bias
- Halo effect
- Self-serving bias
- Information bias
Quantitative research deals with numbers and statistics, while qualitative research deals with words and meanings.
Quantitative methods allow you to systematically measure variables and test hypotheses . Qualitative methods allow you to explore concepts and experiences in more detail.
In mixed methods research , you use both qualitative and quantitative data collection and analysis methods to answer your research question .
A sample is a subset of individuals from a larger population . Sampling means selecting the group that you will actually collect data from in your research. For example, if you are researching the opinions of students in your university, you could survey a sample of 100 students.
In statistics, sampling allows you to test a hypothesis about the characteristics of a population.
The research methods you use depend on the type of data you need to answer your research question .
- If you want to measure something or test a hypothesis , use quantitative methods . If you want to explore ideas, thoughts and meanings, use qualitative methods .
- If you want to analyze a large amount of readily-available data, use secondary data. If you want data specific to your purposes with control over how it is generated, collect primary data.
- If you want to establish cause-and-effect relationships between variables , use experimental methods. If you want to understand the characteristics of a research subject, use descriptive methods.
Methodology refers to the overarching strategy and rationale of your research project . It involves studying the methods used in your field and the theories or principles behind them, in order to develop an approach that matches your objectives.
Methods are the specific tools and procedures you use to collect and analyze data (for example, experiments, surveys , and statistical tests ).
In shorter scientific papers, where the aim is to report the findings of a specific study, you might simply describe what you did in a methods section .
In a longer or more complex research project, such as a thesis or dissertation , you will probably include a methodology section , where you explain your approach to answering the research questions and cite relevant sources to support your choice of methods.
Is this article helpful?
Other students also liked, writing strong research questions | criteria & examples.
- What Is a Research Design | Types, Guide & Examples
- Data Collection | Definition, Methods & Examples
More interesting articles
- Between-Subjects Design | Examples, Pros, & Cons
- Cluster Sampling | A Simple Step-by-Step Guide with Examples
- Confounding Variables | Definition, Examples & Controls
- Construct Validity | Definition, Types, & Examples
- Content Analysis | Guide, Methods & Examples
- Control Groups and Treatment Groups | Uses & Examples
- Control Variables | What Are They & Why Do They Matter?
- Correlation vs. Causation | Difference, Designs & Examples
- Correlational Research | When & How to Use
- Critical Discourse Analysis | Definition, Guide & Examples
- Cross-Sectional Study | Definition, Uses & Examples
- Descriptive Research | Definition, Types, Methods & Examples
- Ethical Considerations in Research | Types & Examples
- Explanatory and Response Variables | Definitions & Examples
- Explanatory Research | Definition, Guide, & Examples
- Exploratory Research | Definition, Guide, & Examples
- External Validity | Definition, Types, Threats & Examples
- Extraneous Variables | Examples, Types & Controls
- Guide to Experimental Design | Overview, Steps, & Examples
- How Do You Incorporate an Interview into a Dissertation? | Tips
- How to Do Thematic Analysis | Step-by-Step Guide & Examples
- How to Write a Literature Review | Guide, Examples, & Templates
- How to Write a Strong Hypothesis | Steps & Examples
- Inclusion and Exclusion Criteria | Examples & Definition
- Independent vs. Dependent Variables | Definition & Examples
- Inductive Reasoning | Types, Examples, Explanation
- Inductive vs. Deductive Research Approach | Steps & Examples
- Internal Validity in Research | Definition, Threats, & Examples
- Internal vs. External Validity | Understanding Differences & Threats
- Longitudinal Study | Definition, Approaches & Examples
- Mediator vs. Moderator Variables | Differences & Examples
- Mixed Methods Research | Definition, Guide & Examples
- Multistage Sampling | Introductory Guide & Examples
- Naturalistic Observation | Definition, Guide & Examples
- Operationalization | A Guide with Examples, Pros & Cons
- Population vs. Sample | Definitions, Differences & Examples
- Primary Research | Definition, Types, & Examples
- Qualitative vs. Quantitative Research | Differences, Examples & Methods
- Quasi-Experimental Design | Definition, Types & Examples
- Questionnaire Design | Methods, Question Types & Examples
- Random Assignment in Experiments | Introduction & Examples
- Random vs. Systematic Error | Definition & Examples
- Reliability vs. Validity in Research | Difference, Types and Examples
- Reproducibility vs Replicability | Difference & Examples
- Reproducibility vs. Replicability | Difference & Examples
- Sampling Methods | Types, Techniques & Examples
- Semi-Structured Interview | Definition, Guide & Examples
- Simple Random Sampling | Definition, Steps & Examples
- Single, Double, & Triple Blind Study | Definition & Examples
- Stratified Sampling | Definition, Guide & Examples
- Structured Interview | Definition, Guide & Examples
- Survey Research | Definition, Examples & Methods
- Systematic Review | Definition, Example, & Guide
- Systematic Sampling | A Step-by-Step Guide with Examples
- Textual Analysis | Guide, 3 Approaches & Examples
- The 4 Types of Reliability in Research | Definitions & Examples
- The 4 Types of Validity in Research | Definitions & Examples
- Transcribing an Interview | 5 Steps & Transcription Software
- Triangulation in Research | Guide, Types, Examples
- Types of Interviews in Research | Guide & Examples
- Types of Research Designs Compared | Guide & Examples
- Types of Variables in Research & Statistics | Examples
- Unstructured Interview | Definition, Guide & Examples
- What Is a Case Study? | Definition, Examples & Methods
- What Is a Case-Control Study? | Definition & Examples
- What Is a Cohort Study? | Definition & Examples
- What Is a Conceptual Framework? | Tips & Examples
- What Is a Controlled Experiment? | Definitions & Examples
- What Is a Double-Barreled Question?
- What Is a Focus Group? | Step-by-Step Guide & Examples
- What Is a Likert Scale? | Guide & Examples
- What Is a Prospective Cohort Study? | Definition & Examples
- What Is a Retrospective Cohort Study? | Definition & Examples
- What Is Action Research? | Definition & Examples
- What Is an Observational Study? | Guide & Examples
- What Is Concurrent Validity? | Definition & Examples
- What Is Content Validity? | Definition & Examples
- What Is Convenience Sampling? | Definition & Examples
- What Is Convergent Validity? | Definition & Examples
- What Is Criterion Validity? | Definition & Examples
- What Is Data Cleansing? | Definition, Guide & Examples
- What Is Deductive Reasoning? | Explanation & Examples
- What Is Discriminant Validity? | Definition & Example
- What Is Ecological Validity? | Definition & Examples
- What Is Ethnography? | Definition, Guide & Examples
- What Is Face Validity? | Guide, Definition & Examples
- What Is Non-Probability Sampling? | Types & Examples
- What Is Participant Observation? | Definition & Examples
- What Is Peer Review? | Types & Examples
- What Is Predictive Validity? | Examples & Definition
- What Is Probability Sampling? | Types & Examples
- What Is Purposive Sampling? | Definition & Examples
- What Is Qualitative Observation? | Definition & Examples
- What Is Qualitative Research? | Methods & Examples
- What Is Quantitative Observation? | Definition & Examples
- What Is Quantitative Research? | Definition, Uses & Methods
"I thought AI Proofreading was useless but.."
I've been using Scribbr for years now and I know it's a service that won't disappoint. It does a good job spotting mistakes”

Title Page Setup
A title page is required for all APA Style papers. There are both student and professional versions of the title page. Students should use the student version of the title page unless their instructor or institution has requested they use the professional version. APA provides a student title page guide (PDF, 199KB) to assist students in creating their title pages.
Student title page
The student title page includes the paper title, author names (the byline), author affiliation, course number and name for which the paper is being submitted, instructor name, assignment due date, and page number, as shown in this example.
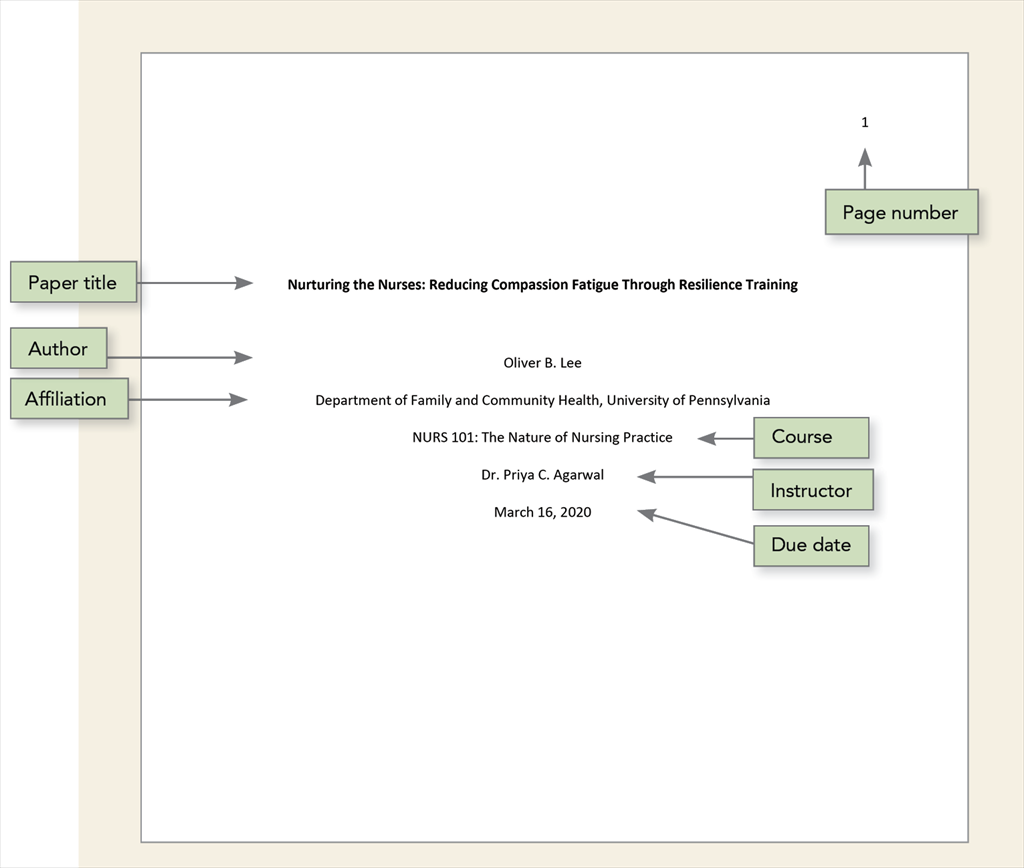
Title page setup is covered in the seventh edition APA Style manuals in the Publication Manual Section 2.3 and the Concise Guide Section 1.6
Related handouts
- Student Title Page Guide (PDF, 263KB)
- Student Paper Setup Guide (PDF, 3MB)
Student papers do not include a running head unless requested by the instructor or institution.
Follow the guidelines described next to format each element of the student title page.
|
|
|
|
|---|---|---|
| Paper title | Place the title three to four lines down from the top of the title page. Center it and type it in bold font. Capitalize of the title. Place the main title and any subtitle on separate double-spaced lines if desired. There is no maximum length for titles; however, keep titles focused and include key terms. |
|
| Author names | Place one double-spaced blank line between the paper title and the author names. Center author names on their own line. If there are two authors, use the word “and” between authors; if there are three or more authors, place a comma between author names and use the word “and” before the final author name. | Cecily J. Sinclair and Adam Gonzaga |
| Author affiliation | For a student paper, the affiliation is the institution where the student attends school. Include both the name of any department and the name of the college, university, or other institution, separated by a comma. Center the affiliation on the next double-spaced line after the author name(s). | Department of Psychology, University of Georgia |
| Course number and name | Provide the course number as shown on instructional materials, followed by a colon and the course name. Center the course number and name on the next double-spaced line after the author affiliation. | PSY 201: Introduction to Psychology |
| Instructor name | Provide the name of the instructor for the course using the format shown on instructional materials. Center the instructor name on the next double-spaced line after the course number and name. | Dr. Rowan J. Estes |
| Assignment due date | Provide the due date for the assignment. Center the due date on the next double-spaced line after the instructor name. Use the date format commonly used in your country. | October 18, 2020 |
|
| Use the page number 1 on the title page. Use the automatic page-numbering function of your word processing program to insert page numbers in the top right corner of the page header. | 1 |
Professional title page
The professional title page includes the paper title, author names (the byline), author affiliation(s), author note, running head, and page number, as shown in the following example.
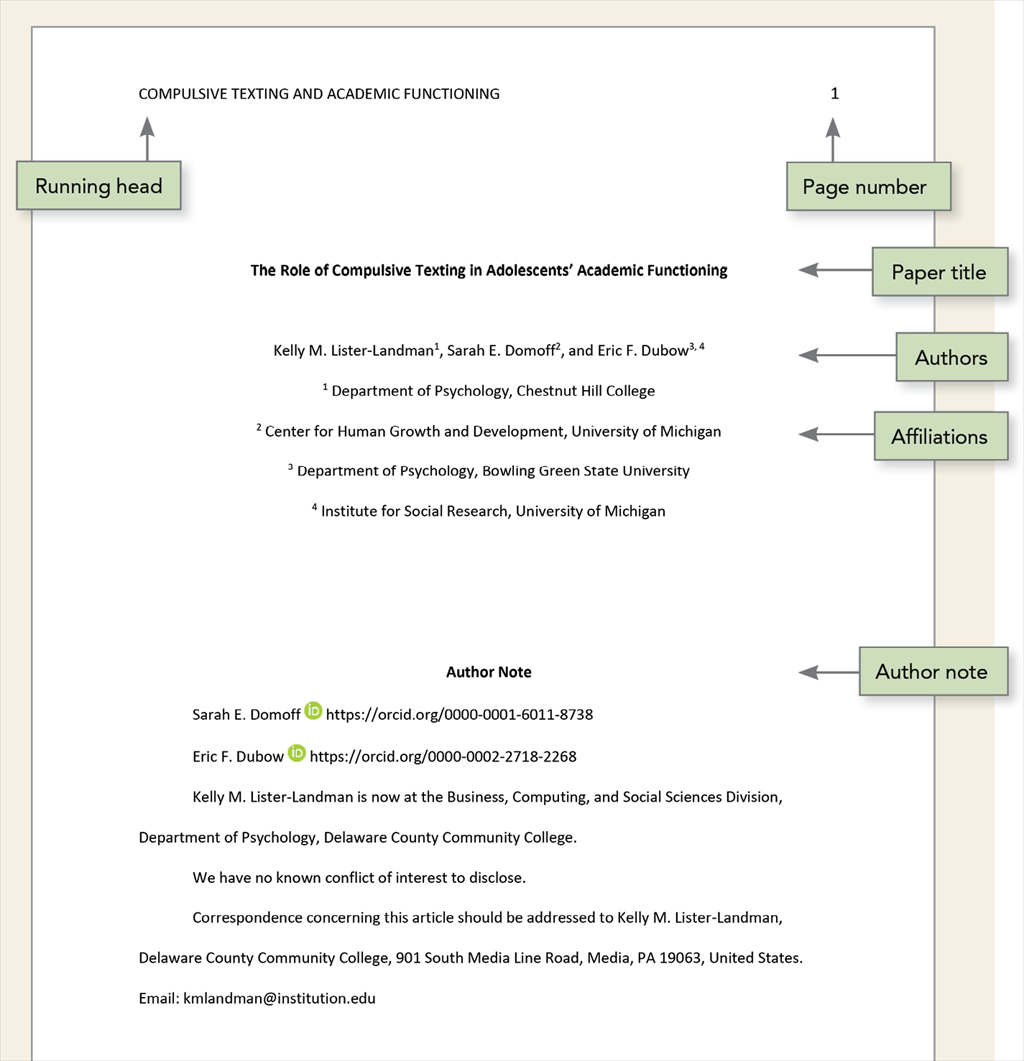
Follow the guidelines described next to format each element of the professional title page.
|
|
|
|
|---|---|---|
| Paper title | Place the title three to four lines down from the top of the title page. Center it and type it in bold font. Capitalize of the title. Place the main title and any subtitle on separate double-spaced lines if desired. There is no maximum length for titles; however, keep titles focused and include key terms. |
|
| Author names
| Place one double-spaced blank line between the paper title and the author names. Center author names on their own line. If there are two authors, use the word “and” between authors; if there are three or more authors, place a comma between author names and use the word “and” before the final author name. | Francesca Humboldt |
| When different authors have different affiliations, use superscript numerals after author names to connect the names to the appropriate affiliation(s). If all authors have the same affiliation, superscript numerals are not used (see Section 2.3 of the for more on how to set up bylines and affiliations). | Tracy Reuter , Arielle Borovsky , and Casey Lew-Williams | |
| Author affiliation
| For a professional paper, the affiliation is the institution at which the research was conducted. Include both the name of any department and the name of the college, university, or other institution, separated by a comma. Center the affiliation on the next double-spaced line after the author names; when there are multiple affiliations, center each affiliation on its own line.
| Department of Nursing, Morrigan University |
| When different authors have different affiliations, use superscript numerals before affiliations to connect the affiliations to the appropriate author(s). Do not use superscript numerals if all authors share the same affiliations (see Section 2.3 of the for more). | Department of Psychology, Princeton University | |
| Author note | Place the author note in the bottom half of the title page. Center and bold the label “Author Note.” Align the paragraphs of the author note to the left. For further information on the contents of the author note, see Section 2.7 of the . | n/a |
|
| The running head appears in all-capital letters in the page header of all pages, including the title page. Align the running head to the left margin. Do not use the label “Running head:” before the running head. | Prediction errors support children’s word learning |
|
| Use the page number 1 on the title page. Use the automatic page-numbering function of your word processing program to insert page numbers in the top right corner of the page header. | 1 |
Grab your spot at the free arXiv Accessibility Forum
Help | Advanced Search
Computer Science > Computation and Language
Title: rag foundry: a framework for enhancing llms for retrieval augmented generation.
Abstract: Implementing Retrieval-Augmented Generation (RAG) systems is inherently complex, requiring deep understanding of data, use cases, and intricate design decisions. Additionally, evaluating these systems presents significant challenges, necessitating assessment of both retrieval accuracy and generative quality through a multi-faceted approach. We introduce RAG Foundry, an open-source framework for augmenting large language models for RAG use cases. RAG Foundry integrates data creation, training, inference and evaluation into a single workflow, facilitating the creation of data-augmented datasets for training and evaluating large language models in RAG settings. This integration enables rapid prototyping and experimentation with various RAG techniques, allowing users to easily generate datasets and train RAG models using internal or specialized knowledge sources. We demonstrate the framework effectiveness by augmenting and fine-tuning Llama-3 and Phi-3 models with diverse RAG configurations, showcasing consistent improvements across three knowledge-intensive datasets. Code is released as open-source in this https URL .
| Comments: | 10 pages |
| Subjects: | Computation and Language (cs.CL); Artificial Intelligence (cs.AI); Information Retrieval (cs.IR); Machine Learning (cs.LG) |
| Cite as: | [cs.CL] |
| (or [cs.CL] for this version) | |
| Focus to learn more arXiv-issued DOI via DataCite |
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Forensic research of satellite images forgery: a comprehensive survey
- Open access
- Published: 14 August 2024
- Volume 57 , article number 253 , ( 2024 )
Cite this article
You have full access to this open access article

- Xiangling Ding 1 , 2 ,
- Yuchen Nie 1 ,
- Jizhou Yao 1 ,
- Jia Tang 1 &
- Yubo Lang 2 , 3
Satellite imagery is a significant and attractive area in remote sensing applications, widely applied in monitoring, managing, and tracking natural disasters. Due to the proliferation of commercial satellites, there is an increasing availability of high-resolution satellite images. However, the ubiquity of image editing tools and the advancement of image processing technologies have made satellite image forgery relatively easy, allowing for the arbitrary addition, removal, or modification of target objects. In recent years, satellite image forgery has caused significant negative effects and potential threats to the nation, society, and individuals, drawing the attention of many scholars. Although forensics of satellite image tampering is an emerging research field that offers new insights into the field of information security, there has been a scarcity of comprehensive surveys in this area. This paper aims to fill this gap and investigates recent advances in satellite image forensics, focusing on tampering strategies and forensic methodologies. First, we discuss the concept of satellite images, the definition of satellite image forgery from global and local perspectives, and the datasets commonly used for satellite image forensics. We then detail each tampering detection and localization method, including their characteristics, advantages, disadvantages, and performance in detection or localization across various notable datasets. We also compare some representative forensic networks using evaluation metrics and public datasets. Finally, the anticipated future directions for satellite image forgery forensics are discussed.
Explore related subjects
- Artificial Intelligence
Avoid common mistakes on your manuscript.
1 Introduction
With the increasing number of satellite launches, advanced satellite products like satellite images have significantly enhanced the quality of life. Satellite images, also known as remote sensing images, are widely applied in various fields in our society. Specifically, in agriculture, they are used for crop monitoring (Ali et al. 2022 ), yield prediction (Muruganantham et al. 2022 ), and irrigation planning (Foster and Mieno 2020 ). Meanwhile, they are also adopted in forest management for mapping (Lewis et al. 2022 ), monitoring (Salaria et al. 2023 ), and other management tasks. In addition, they are applied for environmental monitoring to track (Dinh et al. 2023 ), water quality (Singh et al. 2020 ), and natural disasters (Attia et al. 2022 ) as well. Ultimately, they can also serve critical functions in defense and intelligence missions. However, with the rapid development of image editing software and processing technology, manipulating satellite images by intentionally adding, removing, or modifying target objects is becoming easier. Recently, satellite image forgery has caused severe negative effects and potential threats to the nation, society, and individuals, such as fake satellite images of the Malaysia Airlines Flight MH370 wreckage, Diwali celebrations in India, and the curved Hong Kong-Zhuhai-Macao Bridge, as shown in Fig. 1 . Consequently, the forensics of satellite image forgery has attracted broad research interest in the security field. With the growing use of satellite images, the development of forensic technology to verify their authenticity and integrity has become urgent.
Examples of satellite image forgery. a The wreckage of Malaysia Airlines Flight MH370; b Diwali in India; c The curved Hong Kong-Zhuhai-Macao Bridge

Categorization of satellite image forensics methods. Only representative works are listed on this diagram
Research in image forensics has witnessed significant progression and enrichment (Hao et al. 2021 ; Bhagtani et al. 2022 ; Kaur et al. 2023 ), including detection methods for the traces of basic image operations such as resampling, median filtering, copy-move-paste, splicing, image smoothing, sharpening, and other operations analyses. It also encompasses detection methods for various image operation chains, including double JPEG compression, JPEG compression, combinations of resampling, continuous resampling, and combinations of diversified operations, as well as universal detection methods employing deep learning-based detectors. These methods consider the authenticity of digital images from multiple perspectives and enable effective detection. However, applying forensic methods to satellite image forgery remains a challenge due to the unique features of satellite images in terms of spectral bands and data representation, as well as the complexities involved in compression strategies, post-processing techniques, and sensor technology. Thus, the detection and localization of satellite image forgery, also known as satellite image forensics (Abady et al. 2024 ), has become increasingly interesting in the security field. Here, we will focus solely on a systematic review of forensic methods for satellite image tampering.
Satellite image forgery can be conveniently divided into global tampering and local tampering. Global tampering (Abady et al. 2022 ; Yates et al. 2022 ; Mansourifar et al. 2023 ; Ghelichkhani et al. 2023 ; Alibani et al. 2024 ) usually generates fake satellite images directly using Generative Adversarial Network (GAN). The general local forgery usually involves three types: copy-move (copying and moving pixels from one area of the image to another), splicing (creating a new image by combining two or more image patches), and inpainting (filling a deleted region using an inpainting algorithm) Chen et al. ( 2021 ). However, since satellite image tampering is an emerging research field, only the splicing operation is adopted to construct forgery datasets (Yarlagadda et al. 2018 ; Horváth et al. 2020 , 2021a , b ; Niloy et al. 2023 ) in the research literature, in which the tampering methods used for satellite images are similar to those used in general image forgery. As a consequence, the corresponding datasets for the other two tampering ways will be generated in future studies. Consequently, global tampering of satellite images can lead to different styles, while for local splicing tampering of satellite images, some objects can be spliced from other satellite images, which is usually difficult to detect with the naked eye, but changes key information.
In particular, multispectral satellite images are composed of multiple bands or channels. These channels capture the energy reflected or radiated by ground objects within specific wavelength ranges, indicating their unique properties. In remote sensing image analysis, the information of each channel is important, and the information of one channel may be used as a supplement to the information of another channel. Forgery can disrupt the interrelationships between the multiple channels of multispectral images, which may mislead the interpretation of surface features and result in unreliable analysis.
Since satellite images play an important role in the field of remote sensing, their tampering detection in the authenticity identification of satellite images has made some positive progress. Depending on the types of tampering of satellite images, detection methods can be classified as global tampering detection and local tampering detection. Figure 2 lists the milestones in recent research on global and local tampering detection algorithms for satellite images. It is concluded from systematic investigation that with the improvement of computing power, detection technology has gradually transitioned from hand-crafted to deep learning methods, and research in satellite image forensics has also been increasing annually. At present, there are some published articles on the overview of image forensic tasks (Hao et al. 2021 ; Bhagtani et al. 2022 ; Kaur et al. 2023 ). But unlike these works, we address the gap and investigate recent developments in forensics research on satellite image tampering from the viewpoints of tampering means and forensic traces. We introduce two types of satellite image forgeries and their corresponding forensic methods, and then we highlight the underlying forensic clues and some constructive suggestions for further research in this field. We aim to assist readers with a detailed survey of current state-of-the-art forensic techniques for satellite image tampering, together with future potential research directions for researchers in this field. The following are the primary contributions of our work.
We provide a comprehensive survey of forensic methods for satellite image tampering, including definitions of forgery, public benchmark datasets, evaluation metrics, and a systematic comparison of existing forensic methods.
We summarize the detection and localization accuracy of representative methods in public benchmark datasets. Additionally, we list their characteristics, advantages, and key factors affecting detection efficiency.
We outline the challenges and future trends in satellite image forensics research, focusing on providing insightful guidance to this community.
The paper is laid out as follows. In Sect. 2 , we expound on the basic content of satellite image forensics, including the concept of satellite images, the definition of forgery, and commonly used datasets. In Sect. 3 , we introduce and analyze methods for global tampering detection. In Sect. 4 , we categorize and discuss forensic methods for local tampering into three main groups, analyzing their advantages and disadvantages and comparing their performance across various datasets. Finally, in Sects. 5 and 6 , we outline future research directions and provide a summary of the survey.
2 Base concepts
2.1 concept of satellite images.
Remote sensing is a comprehensive detection technology that uses sensors on platforms such as drones, airplanes, and artificial earth satellites to detect and reveal the characteristics and changes of objects by analyzing the electromagnetic wave signatures from a distance. From a macro perspective, remote sensing takes the Earth as the research object, based on the interaction between electromagnetic waves and Earth’s surface matter, to explore the spatial distribution characteristics and spatio-temporal changes of Earth’s resources and environment. A complete remote sensing system includes six parts: information characteristics of the measured target, information acquisition, information recording, transmission and reception, information processing, and information application.
Satellite images, also known as remote sensing images, carry information about remote sensing observation targets. Common sources of satellite images include various types of satellites, each with different purposes and characteristics. Some common satellites that provide remote sensing images include the Landsat program, the Sentinel series, the National Oceanic and Atmospheric Administration series, the Geo Operational Environment Satellite series, etc. Here are some characteristics of satellite images.
High resolution and wide coverage. Remote sensing offers broad spatial coverage that allows the simultaneous observation of large areas. Currently, understanding the macroscopic spatial distribution of objects on the Earth’s surface often requires space remote sensing. For example, an American Landsat TM image covers an area of \(185 \times 185\) km, and it only needs more than 500 images to cover the entire territory of China.
Spectral range and rich information. Multi-spectral and hyper-spectral sensors can capture electromagnetic waves from visible light to infrared and even microwave bands. This allows satellite images to provide rich information about surface features. Therefore, the amount of information in remote sensing images far exceeds that in ordinary conventional images. Let us take Landsat 8 remote sensing images as an example, its spectral range covers 11 wave-bands, as detailed in Table 1 .
Time-efficient. Geosynchronous meteorological satellites observe the Earth every half hour, while Solar Synchronous Orbit meteorological satellites observe the same area twice a day. Satellite images are utilized to monitor the changing rules of nature, especially in weather conditions and natural disasters, which fully embodies its superior timeliness.
Different distributions. The statistical properties of satellite images can be described by specific statistical models, such as negative exponential distribution, gamma distribution, etc., which help to understand the heterogeneity and non-uniformity of images. In contrast, the statistical properties of ordinary camera images typically exhibit Gaussian distribution (Zenghui and Wenxian 2016 ).
2.2 Definition of satellite images forgery
2.2.1 global forgery.
Global forgery usually occurs when fake images are generated using GAN methods (such as using CycleGAN to perform domain transfer on images) or the diffusion model, and the generated images are defined as global fake images. The forensic method for satellite image forgery treats the detection task as a binary classification problem, that is, correctly classifying an image as real or fake.

Examples of real images and fake images using global manipulation method CycleGAN

Examples of local spliced satellite images (left) and their forgery masks (right)
Examples of global forgery of satellite images generated by CycleGAN are reported in Fig. 3 b. Comparing Fig. 3 a with Fig. 3 b reveals that the real and fake satellite images are nearly indistinguishable to the naked eye. This poses a significant challenge in satellite image forensics. However, this kind of global forgery also goes through down-sampling and then bilinear up-sampling to complete the synthesis from feature space to whole high-resolution and high-quality satellite frames by adopting advanced deep learning techniques. Despite the deep network paradigm, these techniques can produce satellite images that appear natural and smooth and cannot be observed with the human eye, but they unavoidably leave some subtle tampering traces between the various bands of signals because of different strategies of compression schemes, post-processing, and sensors.
2.2.2 Local forgery
Local forgery is mainly concerned with splicing operations in satellite images. That is, using a spliced object from another image to cover a certain area in the image, which can fabricate certain objects or mask their existence. Therefore, satellite image forgery forensics can be approached from two dimensions: tampering detection and tampering localization. Tampering detection aims to verify the authenticity of satellite images, determining whether an image has been forged. In contrast, tampering localization seeks to identify the specific areas where splicing tampering occurred (Abady et al. 2022a ).
Usually, a satellite image f is expressed by the resolution size of \(X \times Y\) . f ( x , y ) represents the grayscale value at position ( x , y ) in the satellite image. Use a forgery mask M ( x , y ) with the same resolution size as the satellite image to indicate its integrity. There are only two distinct values in M : 0 or 1. In M , assign a value of 1 to the tampered area points and 0 to the original area points. A formal definition is expressed as.
Some examples of local forgery of satellite images are shown in Fig. 4 a–f, including tampering objects and their corresponding white markers. Figure 4 a is a Landsat8 satellite image that has forged pixels from a normal camera. Figure 4 b is a Sentinel-2 satellite image containing a spliced object. Figure 4 c is a WorldView-3 satellite image containing a spliced object from another PlanetScope satellite image. Figure 4 d, e are Sentinel-2 satellite images that include forged pixels generated by GANs. Figure 4 f is a WorldView-3 satellite image containing a spliced object. The results of these figures have shown that all achieve the effect of being real. However, this presents a challenge for the forensics of such satellite images. In fact, local tampering of satellite images can be regarded as a complex signal processing system, because the tampering operation needs to add objects to the satellite images, which may change the inter-pixel correlation between the object regions and the background regions to a certain extent. In addition, the correlation between pixels in different bands of satellite images may also change to a certain extent. All of these provide ideas for further developing the forensic methods of satellite image tampering.
2.3 Forgery dataset of satellite images
In this subsection, we introduce several commonly used datasets in research for the detection of satellite image forgeries. For unavailable datasets, we do not provide download links and only give a brief introduction based on their content in the corresponding papers. In Tables 2 and 3 , we have listed the comparison of global and local tampering datasets, and detailed information about these datasets is described in the next two subsections.
2.3.1 Global forgery dataset of satellite images
UW (Zhao et al. 2021 ): the UW dataset was created using the image-to-image translation method based on CycleGAN, and is the first open-source dataset for forged satellite images. The real satellite images are downloaded from Google Earth, and the fake ones are synthesized images of the Seattle and Beijing urban landscape produced by CycleGAN on the CartoDB base map. In this dataset, the ratio of real satellite images to fake ones is 1:1.
LC, Scand and China (Abady et al. 2022b ): the creation of these three datasets signifies the initial focus on multi-spectral satellite image forensics by researchers. These datasets use Sentinel-2 level1-C images as the original images and synthesize fake images by style transfer using GAN on the original images. Each dataset is trained with two GANs, one for generating 13 band images and the other for generating 4 band images. The Land Cover Dataset (LC) is created using CycleGAN to transform between barren and vegetated landscapes. The Scandinavian Dataset (Scand) and China Dataset (China) were created using Pix2pix transfer from summer to winter and vice versa. Each dataset has 4000 original images and 4000 generated images.
2.3.2 Local forgery dataset of satellite images
Dataset1 (Yarlagadda et al. 2018 ): this is the first dataset used for satellite image forensics. Dataset1 is established from Landsat8 satellite images, which comprise 130 real images with \(650 \times 650\) pixels. In these images, 30 images are sliced into \(64 \times 64\) patches for training and validation (20%), so \(D_{train}\) contains 8664 patches while \(D_{val}\) has 2166 ones. The rest 100 images are utilized to create \(D_{test}\) , of which 50 images are used as original images and the rest 50 images are used to produce forged images. Then, we splice three sizes of splicing objects (Small, Medium, and Large respectively with \(32 \times 32\) , \(64 \times 64\) , and \(128 \times 128\) pixels), such as airplanes and clouds, onto 50 selected images in random positions for creating a total of 150 forged images. But all the forged pixels are from a normal camera. In 150 forged images, 50 images contain small objects ( \(D_S\) ), 50 images contain medium objects ( \(D_M\) ), and 50 images contain large objects ( \(D_L\) ). Therefore, \(D_{test}\) contains 200 images, including 50 pristine images, and 150 faked images.
Dataset2 (Horváth et al. 2020 ): it is constructed by orthorectified images from Sentinel-2 satellite. All images were first cropped to a size of \(1000 \times 1000\) pixels, and then 293 images were selected. From these, 100 satellite images were chosen to generate 500 forged images through splicing operations. Note that the spliced objects are extracted from satellite images, which are common and less likely to cause suspicion. These spliced objects include clouds, airplanes, smoke, and drones, with a resolution of \(16 \times 16\) , \(32 \times 32\) , \(64 \times 64\) , \(128 \times 128\) , and \(256 \times 256\) pixels. The training set includes 98 original images, while the test set contains 595 images, including 95 original images, 500 forged images, and their corresponding forgery masks. Compared to Dataset1 , Dataset2 offers a greater variety of shapes for splicing objects, allowing for a more thorough verification of the effectiveness of forensic techniques.
Dataset3 (Horváth et al. 2021a ): the base data of Dataset3 comes from WorldView-3 satellite. Splicing objects are extracted from images captured by the PlanetScope satellite and spliced into WorldView-3 satellite images to form forged images. Its training set includes 28 original images, while the test set includes 859 forged images and their corresponding forgery masks. The original pixels and forged pixels in Dataset3 come from different satellites, enriching the previous satellite image forgery data where forged pixels came from ordinary cameras.
Dataset4-6 (Horváth et al. 2021b ): the original satellite images in these three datasets are from the Sentinel-2 satellite, with an image resolution of \(512 \times 512\) pixels. The proportion of original and forged images in each dataset is approximately 1:1. Dataset4 contains splicing objects generated by StyleGAN2 (Karras et al. 2020 ), Dataset5 contains splicing objects generated by CycleGAN (Zhu et al. 2017 ), and Dataset6 contains splicing objects generated by ProGAN (Karras et al. 2017 ). StyleGAN2, ProGAN, and CycleGAN are trained on Sentinel-2 images (Schmitt et al. 2019 ). The GAN network is trained on a portion of the original images until it can synthesize images similar to the original images. Subsequently, unsupervised Watershed segmentation (Roerdink and Meijster 2000 ) is applied to the original image to divide the region, and segments covering 10% or 50% of the image area were selected as the splicing region. The forged images are created by cropping the spliced objects from the GAN-generated images and splicing them into the original images. Datasets4 , Datasets5 , and Datasets6 contain 17,921, 17,438, and 17,640 images respectively. Dataset4-6 , created using deep learning technology, demonstrate that as technology advances, so too do the methods of satellite image forgery, necessitating more sophisticated forensic techniques for detection.
Dataset7 (Niloy et al. 2023 ): the original images come from the benchmark dataset DeepGlobe (Demir et al. 2018 ), and the forged images are created using the method of Dataset2 , with a resolution of \(1000 \times 1000\) pixels. Due to the scarcity of public datasets, the emergence of Dataset7 enriches the tampered satellite image dataset.
3 Forensic methods for global forgery of satellite images
According to the display format, the forensic methods for global forgery of satellite images can be classified as global tampering detection in RGB satellite images and multi-spectral satellite images.
3.1 Global tampering detection of RGB satellite images
Satellite images can be displayed in the traditional RGB format, hence most image forensics algorithms can be adopted directly or indirectly for satellite image forensics. However, due to different compression schemes, post-processing, and sensors, existing image forensic methods exhibit varying levels of detection accuracy. Therefore, the multi-band satellite image to be tested first converts into RBG bands followed by detection with advanced image forensic algorithms. As a result, some typical forensics methods for satellite images are summarized and classified as RGB image forensics methods for satellite images.

CycleGAN’s application to generate fake satellite images
Zhao et al. ( 2021 ) first believe that deepfake primarily relies on GANs as algorithmic mechanisms, and created the first publicly available deepfake satellite image dataset using CycleGAN (as shown in Fig. 5 ). The visual features that distinguish GAN-generated fake images from real ones include color and texture inconsistency, and frequency domain abnormalities. Fake satellite images differ significantly from real ones, exhibiting more complex and uneven textures, more skewed gray-scale histograms, and clearer edges. Therefore, 26 hand-crafted features are extracted from color histograms, and spatial and frequency domains to distinguish real and fake satellite images followed by feeding them into the Support Vector Machine (SVM) for image authenticity identification.

Geo-DefakeHop method (Chen et al. 2021 ) of geographic fake image detection
Inspired by DefakeHop (Chen et al. 2021 ), Chen et al. ( 2021 ) proposed a robust method to detect forged satellite images, namely Geo-DefakeHop, as shown in Fig. 6 . The assumption is made that GANs can generate low-frequency components well but struggle to generate high-frequency components effectively. Based on this, focusing on the differences in high-frequency components between original and forged satellite images can aid in correct classification. This method uses parallel multiple single-level Saab transform to capture discriminative features, and then utilizes XGBoost classifier to implement the classifying task for true or fake satellite images. Experiments have shown that high-frequency channels are more discriminative for fake satellite image detection than low-frequency channels. During the test, the most discriminative features of several channels are selected for fusion on the basis of the performance of the validation set followed by a classifier for binary classification.
In the case of various image distortion post-processing, namely image resizing, adding white Gaussian noise additive, and JPEG compression, the author verified the performance of Geo-DefakeHop. The results show that the model performs slightly worse with image resizing and JPEG compression distortion than without image processing. For adding additive white Gaussian noise, Geo-DefakeHop’s detection accuracy will be significantly reduced, but it is still better than other models due to its integrated nature. This shows that Geo-DefakeHop has good robustness.
Then, Fezza et al. explored the applicability of four typical convolutional neural network (CNN) architectures, including VGG16 (Simonyan 2014 ), ResNet-50 (He et al. 2016 ), Inception-V3 (Szegedy et al. 2016 ), and Xception (Chollet 2017 ) for fake satellite image detection (Fezza et al. 2022 ). In this method, transfer-learning techniques are used to train and adjust these classical classification networks to classify true or fake satellite images, yielding satisfactory results in the UW dataset. This paper also comes to a conclusion that deep-learning-based approaches have higher accuracy than hand-crafted-based algorithms (Zhao et al. 2021 ) (i.e. spatial, histogram, and frequency features). The authors used two post-processing operations on the test images: adding white Gaussian noise and JPEG compression, to verify the robustness of the four CNN models. Under JPEG compression distortion, the detection performance of Inception-V3 and Xception models decreased with the decrease of the Quality Factor (QF) value, while the performance of VGG16 and ResNet-50 was almost unaffected. However, the detection performance of all methods on Gaussian noise-added images decreased significantly. This indicates that existing CNN models struggle with Gaussian noise attacks. In addition, the author also conducted a comprehensive evaluation of CNN’s performance in fake satellite image detection tasks for the first time, promoting the development of geographic fake image detection, an underdeveloped field.

The framework diagram of hybrid network proposed in method (Liu et al. 2024 )
A lightweight and efficient hybrid network is proposed by combining CNN and Transformers for deepfake satellite image detection tasks (Liu et al. 2024 ), shown in Fig. 7 . Although the excellent performance of fake satellite image detection had been achieved using CNNs, these networks had limited ability to model global information over long distances due to the focus on local information modeling by convolutional layers. Subsequently, inspired by the tremendous success of Transformers in image classification, the authors introduced it to the detection of deepfake satellite images. They designed a hybrid network that includes convolutional-based local feature blocks (LFB) and Transformer-based global feature blocks (GFB), which can offer a powerful blend of local spatial information and global semantic information in satellite images. Furthermore, Channel Attention (CA) is also introduced in LFBs to make the model more focused on important spatial information. The proposed hybrid model exhibits almost perfect detection capability on the UW dataset.
The authors used three post-processing operations: JPEG compression, adding Gaussian noise, and applying Gaussian blur, to compare the robustness of the proposed method with other advanced methods. For JPEG compression, the evaluation metrics for the CNN network, Transformer network, and the proposed Hybrid network all decrease as the QF value decreases, while the performance of the manual feature-based method improves due to capturing more discriminative features. Adding noise and applying blur significantly reduce the detection ability of all methods, but the proposed method still performs better than others. The hybrid network performs well under all attacks, proving its good robustness.

VQ-VAE2 with 3-layer structure in method (Abady et al. 2024 )
3.2 Global tampering detection of multi-Spectral satellite images
Except for the RGB format, there is another format, i.e. multi-spectral. Therefore, some researchers have proposed forensic methods from a multi-spectral perspective, and representative methods are summarized below.
In this research orientation, Abady et al. ( 2022b ) conducted the first authenticity study on the fake multi-spectral satellite images generated by GANs. They applied CycleGAN for land cover style transfer or Pix2pix for seasonal transfer on Sentinel-2 level1-C satellite images and then created three 13-band or 4-band generated satellite image datasets, i.e. Land Cover Dataset, Scandinavian Dataset, and China Dataset. The detection capability of EfficientNet-B4, especially in EfficientNet-B4 without downsampling in the initial layer, was explored for multi-spectral fake satellite images, and good results were obtained. When using EfficientNet-B4 to classify multi-spectral satellite images to distinguish their authenticity, the author modified the input channel dimension to 4 or 13 to adapt the images. In matched detection scenarios, where both training and test sets are produced by the same GAN, it can achieve a detection accuracy of more than 0.98. However, in mismatched detection scenarios, especially for Land Cover Datasets, the detection accuracy seriously degrades due to different spectral distributions.
To overcome the weak generalization capability, the same team proposed a one-class classification VQ-VAE2-based detection method (Abady et al. 2024 ) to identify the authenticity of multi-spectral satellite images. The modified VQ-VAE2 model applies three levels of latent space, shown in Fig. 8 , enabling the learning of more complex spectral distributions, and capturing global and local information of images. This method used VQ-VAE2 (Van Den Oord and Vinyals 2017 ; Razavi et al. 2019 ) to reconstruct the original image, distinguishing the GAN-generated satellite images from the original ones by analyzing the reconstruction differences between the input images and the output images. The authors conducted experiments on three datasets: LC , Scand , and China . Since the multi-spectral satellite images used have 4 bands or 13 bands, the authors trained a VQ-VAE2 model for each band. A reconstruction error is obtained using VQ-VAE2 for each band of satellite images during the prediction phase. The reconstruction error is threshold-processed to output a result indicating whether a certain band of the image is real or generated. 100 original images are selected from the test set of each dataset, and the false positive rate of the model on these 100 images is fixed at 0.1 to determine a detection threshold, which can ensure the accuracy and reliability of the VQ-VAE2 detector.
VQ-VAE2 is trained on the pristine images and then directly tests fake satellite images from different GANs. Even when encountering new types of GAN-generated satellite images, it does not need to be retrained to fit the distribution of these new synthesized satellite images to detect them correctly. As a result, this detector has superior generalization capability.
3.3 Forensic survey for global tampering of satellite images
Based on the description and analysis mentioned above, the highlights of forensic methods for the global manipulation of satellite images are summarized in Table 4 . In general, each forensic method for fake satellite images uses different forensic characteristics and hence has different superiority. In the field of satellite image forensics, more in-depth research into the analysis of generation traces and the characteristics of generative networks is needed to develop more efficient detection strategies aimed at improving accuracy.
4 Forensic methods for local tampering of satellite images
According to the backbone models adopted, forensic methods for local tampering of satellite images are classified into three categories: generative model-based approaches, segmentation model-based approaches and mixture model-based approaches. The key point of the generative model-based approach is to adopt the generative model to extract the distribution pattern of the pristine satellite image, effectively distinguish the pristine satellite image from the manipulated one, and then accurately locate the spliced area in the manipulated satellite image. They are usually unsupervised and trained without annotated data. The central theme of the segmentation model-based approach is to transform the satellite image tampering detection task into a pixel-level binary classification problem. Through end-to-end segmentation algorithms, each pixel in the satellite image is judged whether it has been tampered with, thereby localizing the splicing area in the tampered image. These methods are usually supervised and require annotated data during training, but often achieve better localization performance. The last category generally integrates generative model-based approaches with segmentation model-based approaches to combine both advantages for better detection performance and generalization ability. The information for all types of methods is listed in Table 5 .
4.1 Generative model-based methods
The generative model is a type of probability model that can simulate unknown probability distributions that exist in the training dataset. After training, samples are taken from the generative model to synthesize new observation results that look similar to the data in the training dataset, as if they are also included in the training dataset. Currently, there are two different generative models: machine learning-based and deep learning-based models. Among them, the Hidden Markov Model (HMM) (Eddy Sean 2004 ), the Gaussian Mixture Model (GMM) (Reynolds et al. 2009 ), and the Deep Belief Network (DBN) (Hinton and Salakhutdinov 2006 ), etc. belong to the former category, while the Autoregressive model (Bond-Taylor et al. 2021 ), the AutoEncoder (Goodfellow et al. 2016 ), the Generative Adversarial Networks (GAN), the Normalizing Flow (Flow) (Dinh et al. 2014 ), and the Denoising Diffusion Probabilistic Model (Diffusion) (Ho et al. 2020 ), etc. belong to the latter category. The rest of this subsection will investigate the application of the generative model in satellite image tampering detection and localization tasks.
As the forerunner, Yarlagadda et al. used the autoencoder (Goodfellow et al. 2016 ) to extract recognizable features for detecting forged satellite image (Yarlagadda et al. 2018 ). They first divide the original image into small overlapping patches with \(64 \times 64\) pixels, then these patches are reconstructed by autoencoder. In this way, the encoder of the autoencoder can fully capture the probability distribution of the pristine satellite image. Here, the autoencoder is used as a generator, and a discriminator is added to form a GAN structure, which can then be trained in adversarial ways. The structure of the GAN is shown in Fig. 9 a. Due to the powerful classification capabilities of One-Class SVM (Wang et al. 2004 ), this method uses it to learn the features of each original image patch to detect whether there are tampered parts in the test satellite image on a block-by-patch basis, shown in Fig. 9 b. Localization results can be obtained by stitching the SVM output on each patch of the image according to the corresponding position and applying a threshold. The authors have conducted some experiments on Dataset1 and achieved good results.
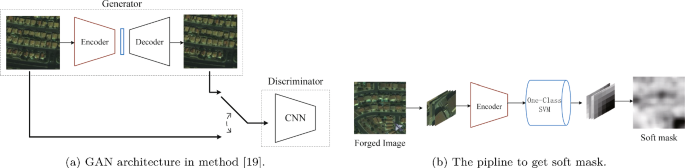
The proposed autoencoder and One-Class SVM method (Yarlagadda et al. 2018 )
To perform integrity checks on high-resolution satellite images, manipulation detection is usually performed patch by patch. Although this improves inspection efficiency, individual image patches lack spatial contextual information, making it difficult to distinguish and accurately locate the spliced areas within satellite imagery at the pixel level. The same image-to-patch strategy is also used in the following methods (Horváth et al. 2019 , 2020 , 2021a ).
The same team used the GAN strategy and the One-Class classifier to identify tampering regions in satellite images with high localization accuracy (Yarlagadda et al. 2018 ). At the same time, the Conditional Adversarial Generative Network (Conditional GAN) (Mirza and Osindero 2014 ) is employed to discover the hidden correlation between satellite images and their corresponding forgery masks (Bartusiak et al. 2019 ).

The pix2pix structure used in method (Bartusiak et al. 2019 )
Subsequently, Bartusiak et al. extended pix2pix, a variant of the Conditional GAN, to execute tampering localization (Bartusiak et al. 2019 ), and its structure is provided in Fig. 10 . Dataset1 is selected to conduct experiments because of the availability of satellite images ( I ) and their forgery masks ( M ). I and M (used as conditions) are embed into the generator. By using the GAN for training, the correspondence between I and M is learned to make the generator ultimately generate a soft forgery mask ( \(\hat{\textbf{M}}\) ) similar to the forgery mask ( M ), i.e. \(\hat{\textbf{M}} \approx\) M. Here, the loss of the generator is represented as.
where \(\mathcal {L}_{cGAN}\) and \(\mathcal {L}_R\) are the cGAN loss, and the binary cross entropy, respectively. As a result, the generator of the Conditional GAN can be regarded as a tampering detector for satellite images. Based on the number and position of pixels with a value of 1 in \(\hat{\textbf{M}}\) , it can be determined which position in the image it has been tampered with. This method requires manipulated satellite images and the corresponding masks for training and thus belongs to supervised learning. Besides, threshold processing is a necessary step of this method to locate the forged regions from satellite images. In brief, this method achieves 100% detection performance for Dataset1 .
Evolving from Yarlagadda et al.’s method, Horváth et al. designed an improved Deep Support Vector Data Description (SVDD), i.e., Satellite Support Vector Data Description (SatSVDD) (Horváth et al. 2019 ) as a single classifier to detect and localize spliced regions using only information from pristine satellite images. In this method, an autoencoder obtains recognizable features from image patches, and then they are fed into SVDD to construct a hypersphere to make a final decision. Similarly to Yarlagadda et al. ( 2018 ), it is also inspired by a reconstruction error to force an autoencoder to reconstruct small patches from the original image. Because forgery images were not trained, SatSVDD will decide image patches outside the hypersphere during prediction as forgery ones and output a large outlier. Outliers are combined in order of position to generate a soft forgery mask \(\hat{\textbf{M}}\) . The value of the \(\hat{\textbf{M}}\) at the overlapping position of the image patch is filled by the average of all outliers at that position. To enhance the accuracy of tampering detection, \(\hat{\textbf{M}}\) -based detection function is proposed as.
Where \(\mu _{\hat{\textbf{M}}}\) and max( \(\hat{\textbf{M}}\) ) are the average and maximum values of all pixels in \(\hat{\textbf{M}}\) , respectively. Perhaps because of simultaneous training of autoencoder and SVDD, this method has achieved better results. In addition, a comprehensive manipulation detection score was proposed to improve the ROC_AUC and PR_AUC of tampering detection above 92%.
A one-class classification approach (Horváth et al. 2020 ) based on the principle of DBN is developed to locate manipulated regions in satellite images. They conducted experiments on Dataset2 . Training requires only the original satellite image, and after training, the forgery regions can be identified due to the difference from the distribution of the original satellite image.

DBN structure used in method (Horváth et al. 2020 )
Since RBM (Freund et al. 1991 ) is a symmetrically coupled, stochastic recurrent neural network, the DBN introduces two-level RBMs as an encoder-decoder structure to reconstruct images, shown in Fig. 11 . The first-level RBM represents the image block as a hidden representation, while the second-level RBM utilizes the hidden representation to obtain the reconstructed image. Because it is trained only on original images, the DBN learns only the distribution of original images and cannot learn that of spliced objects. As a consequence, the DBN can accurately reconstruct the original patches, but it is unable to reconstruct the spliced regions. Therefore, image patches containing spliced objects will obtain larger mean square error (MSE) values than the original ones during DBN reconstruction. Based on the calculated MSE values, a heatmap is generated. The positions with higher values in the heatmap are more likely to belong to the tampered area. Apply a threshold on the heatmap to obtain the final soft forgery mask, indicating the potential tampered area in the image. This model is highly effective in detecting small spliced objects and is also very competitive in doing so.

Vision transformer pipeline proposed in method (Horváth et al. 2021a )
Using an autoencoder to reconstruct a known target image, after training, it is possible to distinguish this type from other types based on the reconstruction error. As a result, this idea of reconstruction error is fully adopted in the one-class classifier, which can be specially designed to identify a known target class and determine other unknown classes as abnormal data. This idea is also utilized in the detection of satellite image manipulation, such as references Van Den Oord et al. ( 2016 ) and Horváth et al. ( 2021a ).
As an attempt, Montserrat et al. integrate autoregressive models, PixelCNNs (Van Den Oord et al. 2016 ), and Gated PixelCNNs (Van den Oord et al. 2016 ) to realize the solution of detection and localization of satellite image tampering (Montserrat et al. 2020 ), and uses Dataset2 as the satellite image dataset. The adopted PixelCNNs can obtain the global distribution of satellite images by taking stock of the distribution of all pixels. The procedure for computing the distribution of the image f is to multiply the conditional distributions of all pixels \(fp_i\) together, expressed as.
It generates all pixels one by one, and the current generated pixel value \(fp_i\) is calculated on the basis of all previously generated pixels, \(fp_{1},\dots , fp_{i-1}\) . In RGB satellite images, the values of each pixel on the R, G, and B channels are calculated in order one by one, calculated as.
Subsequently, this process is extended to multi-spectral satellite images and then the values of the points at each position in the image are a multi-tuple, defined as.
where C and \(fp_{i,j}\) are the channel number and the i th pixel of the j th channel of the satellite image, respectively.
Since the training phase is performed only on the pristine image, PixelCNNs and Gated PixelCNNs can learn the distribution of the pristine satellite image and detect the region out of the learned distribution. Then, the authors use negative log-likelihood loss to determine whether the image contains tampered pixels. When processing the tampered pixel or the untouched one, a low or high likelihood value respectively outputs. If the likelihood of a pixel is greater than the set threshold, the pixel is considered to have been tampered with. Obviously this method is also unsupervised. Compared to previous forensic methods, it performs superior in small spliced objects by processing the entire image in a fully convolutional manner and providing pixel-level localization.
Guided by this new research direction, Horváth et al. proposed another unsupervised satellite image forgery detection method (Horváth et al. 2021a ) based on Vision Transformer (Dosovitskiy et al. 2020 ), as shown in Fig. 12 . Two different datasets, Dataset2 and Dataset3 are used to evaluate performance. The core idea is similar to DBN, where the Vision Transformer serves as the autoencoder to catch the distribution of the pristine satellite image and can correctly reconstruct it. During the prediction phase, the image f is used as input and the reconstructed image \(f_r\) is generated through the Vision Transformer, and then \(3\times 3\) Laplace filters are used to convolve each f , \(f_r\) for the other two images \(f_d\) , \(f_{rd}\) . The Laplace filter is adopted as an edge detector to emphasize high-frequency components on the f and fr . After calculating the differences between f and \(f_r\) , and between \(f_d\) and \(f_{rd}\) , a heatmap is obtained by taking the mean of these two differences.
Next, the heatmap is first subjected to threshold processing, followed by a specially designed post-processing stage to obtain a soft forgery mask. The post-processing is composed of several ErodeIsolated operations, which is a new type of morphological filter that can remove smaller objects from an image without affecting the larger ones. A part of post-processing is defined as:

Two examples of ErodeIsolated that proposed in method (Horváth et al. 2021a )
There are two examples depicted in the Fig. 13 , where \(\wedge\) is a logical OR operation and \(\vee\) is a logical AND operation. The structural element of ErodeIsolated is a square with sides of length \(2b + 1\) , which contains an inner square with sides of length \(2a + 1\) . In the structural element, the values in the inner square take 1, and the remaining values take 0. The post-processing composed of ErodeIsolated can reduce the false positive caused by the noise introduced, resulting in more accurate localization. This method is by far the best method for unsupervised detection.
4.2 Segmentation model-based method
The semantic segmentation of images has undergone a long period of development and is gradually becoming mature (Mo et al. 2022 ). The general segmentation process of an end-to-end segmentation network utilizes its internal structure to shrink the dimensions of the original image and capture features (Long et al. 2015 ). Subsequently, the smaller feature maps are gradually restored to a prediction image with the same resolution as the input image. Each pixel in the prediction image contains information about the classification of that pixel. Thus, when using segmentation models in satellite image tampering localization tasks, it is only necessary to simplify the multi-classification task of semantic segmentation into a 2-classification task, that is, perform a 2-classification on each pixel to determine whether it has been tampered with, and the final predicted image is a forgery mask. Segmentation model-based methods can achieve prediction at the pixel level, using supervised training. Here, some typical segmentation model-based methods for satellite images are summarized.

Nested attention U-Net architecture used in method (Horváth et al. 2021b )
Network architecture of HRFNet proposed in method (Niloy et al. 2023 )

The mixture model of the method (Horváth et al. 2022 )
In this subcategory of research, Horváth et al. designed the first segmentation model-based approach to detect counterfeit objects of satellite images by introducing a variant of the U-Net architecture, namely Nested Attention U-Net (NAU-N) (Horváth et al. 2021b ), shown in Fig. 14 . In this work, objects selected from GAN-generated satellite images are spliced into the original satellite images to create three evaluated datasets, Dataset4-6 .
Several versions of U-Net, such as Attention U-Net (Oktay et al. 2018 ) and Nested U-Net (Zhou et al. 2018 ), have been developed to execute the task of image segmentation. Inspired by them, the structure of NAU-N is designed by embedding “U-Net”, attention gates, and dense skip connections. These components can reduce semantic differences between feature maps of different scales, and highlight important features while suppressing irrelevant information. The NAU-N is trained on three datasets in an unsupervised learning mode, and outputs a heatmap with a real number at the position of each pixel. In this heatmap, if the number value at a certain position is large, there may be a spliced object generated by GAN at that position. When threshold processing on the heatmap is performed, the localization of GAN-generated objects within the satellite images is picked out. From the experimental results of this article, we can infer that using semantic segmentation methods for satellite image forgery localization tasks is feasible. Besides, the generalization performance of NAU-N in mismatched scenarios is highly variable. However, NAU-N trained on StyleGAN2-synthesized images can accurately detect whether the satellite image involves ProGAN or CycleGAN-generated objects.
Soon afterward, a new strategy (Niloy et al. 2023 ) is specifically developed for tampering localization tasks in high-resolution satellite images with strong semantic segmentation characteristics. In this work, a new model, namely “HRFNet”, is designed and its core idea is to transform satellite image tampering detection tasks into pixel-level binary segmentation problems. The HRFNet network consists of the RGB branch and the SRM branch, represented in Fig. 15 . The former distinguishes between manipulated and real areas by capturing visual inconsistencies in tampered boundaries, while the latter uses SRM filters (Fridrich and Kodovsky 2012 ) to analyze local noise features in the image. Then, both branches are constructed with shallow and deep parts, where the shallow part can extract features globally with a large receptive field, better capturing spatial information, while the deep part effectively extracts advanced semantic information. Due to the complementarity of deep and shallow parts, feature fusion can improve segmentation performance. After merging features from the RGB and SRM branches, the ASPP module (Chen et al. 2017 ) captures features on multiple scales using different atrous convolutions, obtaining richer contextual information. Finally, it enters the decoder and generates the final segmentation mask, which indicates the manipulated area. The experiments are guided on Dataset7 , and valuable experimental results indicate that the design of the RGB and SRM branches can better locate tampered regions, while the design of the deep and shallow parts can achieve a balance between high AUC values, memory requirements, and processing speed. This strategy is the latest development in satellite image tampering localization tasks.
4.3 Mixture model-based methods
There is only one reported work (Horváth et al. 2022 ), which has adopted the mixture model for locating spliced regions in satellite images. This method utilizes supervised fusion to combine the results of several unsupervised tampering localization techniques to enhance its detection accuracy and generalization ability.
The architectures of this work are shown in Fig. 16 a, b. It receives the mixture of the satellite image, the output of the Gated PixelCNN Ensemble method, and the result of the Vision Transformer method. Note that Gated PixelCNN Ensemble and Vision Transformer methods are two unsupervised detection networks. Besides, MultiTransNAUNet (Multi-Transformer Nested Attention U-Net) leverages the benefits of attention gates, nested architecture, and Transformers’ powerful decoding capabilities to learn all available information from the original satellite image. Finally, a heatmap is also output to produce tampered regions with positive scores. This method is assessed on two large datasets, Dataset3 and Dataset4 . After fusing the outputs from two other methods with the input of the MultiTransNAunet, this method achieves excellent performance. The generated mask is almost identical or very similar to the ground-truth mask. The results also demonstrate that this mixture model-based method can detect spliced regions on satellite images from other datasets (not used during training) under mild retraining conditions.
4.4 Advantage and disadvantage analysis for forensic methods of local tampering of satellite images
Here, we analyze several existing forensic methods for satellite image tampering. There are three main types: generative model-based, segmentation model-based, and mixture model-based. Among them, unsupervised approaches are more suitable for detecting unknown tampering operations, while supervised approaches often have better performance, but need to provide original and annotated faked satellite images. All methods have proposed available solutions for a certain challenge in tampering detection of satellite images. The positive and negative aspects of existing local tampering detection and localization approaches are listed in Table 6 . From it, we can obtain that the ViT-based generative model method is by far the best method for unsupervised detection, HRFNet is the latest development in satellite image tampering localization tasks, and the integration of multiple detection methods has been verified as an effective strategy to improve detection accuracy and generalization ability.
4.5 Evaluation metrics and comparative discussion
4.5.1 evaluation metrics.
The detection of satellite image forgery, that is, whether they have been tampered with, is an image-level binary classification problem. The tampering localization of satellite images, that is, whether a certain block or pixel in the satellite image has been tampered with, is a pixel-level binary classification problem. For binary classification problems, examples can be divided according to the combination of their real categories and the predicted categories of the model. It can be divided into four situations: True Positive (TP), False Positive (FP), True Negative (TN), and False Negative (FN). Thus, for the forensic task of counterfeit satellite images, evaluation metrics commonly use ROC_AUC, P/R_AUC, F1-score, and Jaccard index.
ROC_AUC : true Positive Rate (TPR) and False Positive Rate (FPR) are first calculated as \(TPR=\frac{TP}{TP+FP}, \hspace{5.0pt}FPR=\frac{FP}{TN+FP}\) . Then, the ROC curve is drawn with FPR and TPR as horizontal and vertical axes, respectively. Finally, ROC_AUC is computed as the area under the curve. The closer it gets to 1, the better (Zhou 2021 ).
P/R_AUC : precision and Recall are defined as \(Precision=\frac{TP}{TP+FP}, \hspace{5.0pt}Recall=\frac{TP}{TP+FN}\) . A P/R curve is plotted with Recall as the horizontal axis and Precision as the vertical axes. P/R_AUC is the area under the P/R curve, which reflects the comprehensive performance of the model in terms of precision and recall, the closer it is to 1, the better. Generally, ROC_AUC also focuses on positive and negative samples, while PR_AUC focuses more on positive samples. If the numbers of positive and negative samples are relatively balanced, ROC_AUC can be used, while PR_AUC is better when the number is extremely uneven.
F1-score : the definition of F1-score (Dice Lee 1945 ) is described in Eq. ( 11 ). The range of F1-score is from 0 to 1. A high F1-score indicates that the model has fewer false positives and fewer false negatives on the data.
Jaccard index (JI) : the Jaccard index represents the similarity between the predicted mask generated for localization purposes and the ground-truth (Levandowsky and Winter 1971 ), expressed as.

Localization results in Dataset2 among GAN+SVM (Yarlagadda et al. 2018 ), SatSVDD (Horváth et al. 2019 ) and UU-DBN (Horváth et al. 2020 )

Localization results in Dataset3 and Dataset4 among NAU-N (Horváth et al. 2021b ) and Sat U-net (Horváth et al. 2022 )

Localization results in Dataset2 and Dataset3 among Gated PixelCNN Ensemble (Montserrat et al. 2020 ) and ViT (Horváth et al. 2021a )
4.5.2 Objective results
Then, we compare the performance of various forensic methods in Dataset1-Dataset7 with the evaluation metrics mentioned above, including image-level detection methods [GAN+SVM (Yarlagadda et al. 2018 ), cGANs (Bartusiak et al. 2019 ), SatSVDD (Horváth et al. 2019 ), UU-DBN (Horváth et al. 2020 ), NAU-N (Horváth et al. 2021b )], and pixel-level localization methods [GAN+SVM (Yarlagadda et al. 2018 ), cGANs (Bartusiak et al. 2019 ), SatSVDD (Horváth et al. 2019 ), UU-DBN (Horváth et al. 2020 ), Gated PixelCNN Ensemble (Montserrat et al. 2020 ), ViT (Horváth et al. 2021a ), NAU-N (Horváth et al. 2021b ), Sat U-net (Horváth et al. 2022 ), HRFNet (Niloy et al. 2023 )].
The comparison results of detection performance and location performance of these methods on satellite image datasets are reported in Table 7 and Table 8 . Among all satellite image datasets, only Dataset1 and Dataset2 contain spliced objects with different sizes. Therefore, in Tables 7 and 8 , some metrics include subscripts, which means the performance of the method on images containing stitching objects of a certain size. For example, ROC_AUC \(_{32}\) represents the ROC_AUC value of the forensic method on images containing \(32 \times 32\) pixels spliced objects.
In general, models with good localization performance will also have better detection performance in local manipulation detection and localization tasks for satellite image forgery. Therefore, we pay more attention to the localization efficiency of these models. On Dataset1 , cGANs achieved the best results due to their strong ability to capture satellite image distributions and the fact that supervised methods often achieve higher performance. In unsupervised methods, SatSVDD achieved good results because the joint training of Autoencoder and SVDD can extract more discriminative features, and the proposed detection score considering the mask attribute of manipulated images can better detect tampering. Although GAN+SVM performs the worst, it was the first method for satellite image forensics and pioneered the use of generative models to detect satellite image manipulation. Compared to Dataset1, Dataset2 has higher resolution and richer splicing objects, and many works have been researched on Dataset2 . For Dataset2 , the proven best-performing method is ViT, due to the excellent global modeling capability of the vision transformer and specially designed post-processing modules that can better identify “inconsistencies” in manipulated images. The performance of Gated PixelCNN Ensemble is second, but its full convolutional and pixel-by-pixel processing method can effectively recognize small splicing objects. The performance of UU-DBN is the worst, but it is the first to describe the systematic application of the “reconstruction+error” method in satellite image forensics, which still has a high reference value. Dataset3 contains a more diverse range of spliced objects, with each image containing different spliced objects. Currently, Sat U-net has achieved the best results in Dataset3 , which integrates two localization methods and carefully designs a network structure by incorporating multi-scale global information into the network to accurately locate tampered areas. NAU-N performs second but still outperforms other unsupervised methods. For Dataset4-6 , spliced objects contained in the manipulated image are generated by GAN. On all three datasets, supervised methods are far superior to unsupervised methods. NAU-N achieved good performance because the use of attention gates in the network makes the tampered area more attractive. On Dataset7 , HRFNet performed best due to the ASPP module extracting multi-scale information and supervised training methods.
4.5.3 Subjective results
In addition to quantitative comparisons, we also compared some subjective localization results on Dataset2 , Dataset3 and Dataset4 . The results are visually displayed in Figs. 17 , 18 , and 19 . From Fig. 17 , we can find that UU-DBN achieved the best localization results because DBN can fully capture the distribution of the original image, thus accurately identifying nonoriginal regions. GAN+SVM and SatSVDD are prone to misidentifying the original area as a tampered area. In Fig. 18 , we can see that the mask generated by Sat U-Net is very similar to the real forgery mask because the integrated method will strengthen the attention to the tampered area. In the absence of sufficient global information to learn, the mask generated by NAU-N has internal holes. In Fig. 19 , ViT achieved better localization results, especially on dataset2, indicating that the unsupervised method can already obtain results close to ground truth when detecting spliced objects from cameras in satellite images. However, due to the limitations of full convolution, the generated mask of the Gated PixelCNN Ensemble contains only a portion of the ground truth.
From the above quantitative and subjective analysis, we can conclude that the “reconstruction+error” method based on generative models has achieved excellent performance in detecting local manipulation, making this unsupervised approach very promising. Global information in satellite images helps to fully locate and splice objects, often resulting in better results.
5 Challenges and future researches
So far, some forensic methods for satellite image forgery have appeared, but they mainly focus on patch-level detection or larger target object detection. Whether in global or local tampering detection, supervised methods often achieve higher localization performance. However, they may struggle to achieve effective generalization when faced with tampering operations that have not appeared in the training data. Therefore, unsupervised strategies that do not rely on tampered satellite images during the training process are the preferred method. It is projected that the fusion of supervised and unsupervised approaches will become a popular trend in future research. Besides, mainstreams of the existing approaches are tailored to work with RGB satellite images, so there should be more excellent work for forensic analysis of multi-spectral satellite images.
In addition, accompanied by the advancement of the representation ability of deep learning, novel deep or large model generation techniques can weaken the negative effects of high-frequency components and the boundary effects between the object and the background, and adopt the end-to-end training strategy to extract features and search for the optimal parameters, so as to obtain better forgery effect. In particular, the global and local generation of satellite images has achieved unprecedented visual effects in recent years. Thus, for the in-depth satellite image generation technology, the study of practical and effective detection is the new direction of future research in the detection and localization field. The following four issues merit further research.
5.1 Deeply mining the subtle relationship between satellite image tampering and deep generation models
Although the generation model of satellite images can infer good global and local tampering results, it is a complex processing system of multi-level joint convolutional filtering, which will inevitably leave source generator attribution. In addition, satellite image has the characteristics of various band types, complex structures, and sensor information. The detection and localization of satellite image forgery must mine the subtle relationship between satellite image manipulation and deep generation models. Therefore, this is more challenging, which makes the research work on satellite image manipulation detection still very lacking.
5.2 Advanced explainable AI applications
With the widespread application of machine learning and deep learning in image forensics, model explainability has become particularly important. Although machine learning and deep learning models have improved the efficiency and accuracy of tamper detection and localization, they have also brought about the problem of the "black box" model. That is, the decision-making process of the model is not transparent enough, and it is difficult for humans to understand how the model obtains detection results. The emergence of eXplainable AI (XAI) has alleviated this problem, making the decision-making process of the model more transparent and easy to understand.
Popular XAI tools include LRP (Bach et al. 2015 ), Grid-CAM (Selvaraju et al. 2017 ), RISE (Petsiuk et al. 2018 ), SHAP (Lundberg and Lee 2017 ), LIME (Ribeiro et al. 2016 ) and SOBOL (Fel et al. 2021 ). Especially, in Ying et al. ( 2022 ), by using the heat map generated by Deletion (Samek et al. 2016 ) to visualize what the network is concerned with, and by using Uniform Manifold Approximation and Projection (UMAP) (McInnes et al. 1802 ) to observe the topological interpretation of the learned features, so as to design a model with complementary properties. Silva et al. ( 2022 ) and Mathews et al. ( 2023 ), Grid-CAM was used to provide visual interpretation for deep learning models, highlighting image regions that the model considers important in judging the authenticity of an image. Abir et al. ( 2023 ), through the LIME algorithm, it was explained how the model classifies real and fake images. Tsigos et al. ( 2024 ), the author critically analyzed the limitations of current XAI tools and devised an efficient, in-depth evaluation method specifically tailored for deepfake detection models.
XAI’s ability to highlight pixels in the image that influence decision-making is also critical to designing and interpreting efficient models for satellite image forensics. General-purpose XAI tools may not meet the requirements of satellite image forensics tasks, and there is an urgent need to develop more efficient XAI dedicated to satellite image forensics.
5.3 Robustness evaluation for various types of post-processing
The robustness of a forensic method is used to measure whether it is still effective in the face of distortion attacks. Various types of post-processing operations, such as image resizing, JPEG compression, adding Gaussian noise, and applying Gaussian blur, are often used to test the robustness of satellite image forensics methods. However, in the detection and localization of local tampering, it has not been widely used by researchers. In the future, more types of post-processing operations should be used to verify the robustness of satellite image tampering localization methods.
5.4 The construction of diversified falsified dataset
Satellite image tampering techniques used in existing studies include global tampering and local tampering. Global tampering uses GANs to generate fake images. Local tampering only refers to splicing. Therefore, the constructed datasets lack diversity. Furthermore, copy-move is also a very important type of tampering, which has been widely studied in the image forensics community. Many excellent methods have achieved good results in the study of copy-move (Verma and Singh 2024 ). Especially in Lee et al. ( 2022 ), the authors propose a new image copy-move tampering detection method based on rotation-invariant small wave characteristics and convolutional neural networks, which realizes efficient and accurate positioning of the tampered area. Diwan et al. ( 2023 ), the authors propose an advanced digital image copy-move forgery detection method based on the superpoint keypoint architecture, which can effectively identify and locate areas that have been tampered with by various image processing techniques, with high accuracy and real-time detection capabilities.
Future research methods in satellite image forensics should consider studying the construction of diversified falsified datasets generated by different tampering techniques, such as using more types of GAN methods to generate global fake satellite images and using more types of local tampering such as copy-move and inpainting to create local forged satellite images. As a result, the forensics community of satellite image forgery can flourish.
6 Conclusion
Due to the constant advancement of technology, the financial cost and technical difficulty of falsified satellite images are continually declining, leading to increasing challenges in verifying their authenticity and integrity. Satellite image forensics has emerged as a necessary tool for analyzing imagery. This paper recommends the concept of satellite images, the definition of satellite image forgery detection problems, and commonly used datasets. We also investigate two types of tampering patterns, global and local forgery. We discussed and analyzed detection and localization methods for these two types of manipulation separately.
Regarding the detection of global forgery of satellite images, hand-crafted features can be used to distinguish between true and false satellite images, as well as deep learning methods. We believe that the combination of CNN and Transformers is a promising approach. The one-class classifier method has a strong generalization capability, which is similar to the “reconstruction+error” method based on generative models; we summarize the highlights of all methods.
For the localization of local tampering of satellite images, we discuss them in three categories: generative model-based, segmentation model-based, and mixture model-based. We further analyzed their principles, benchmark datasets, and evaluation metrics. Afterward, the positive and negative aspects of these approaches are pointed out and their performance on different datasets is assessed.
Data availability
No datasets were generated or analysed during the current study.
Abady L, Horváth J, Tondi B, Delp EJ, Barni M (2022) Manipulation and generation of synthetic satellite images using deep learning models. J Appl Remote Sens 16(4):046504
Article Google Scholar
Abady L, Dimitri GM, Barni M (2022) Detection and localization of gan manipulated multi-spectral satellite images. ESANN 2022:339–344
Google Scholar
Abady L, Cannas ED, Bestagini P, Tondi B, Tubaro S, Barni M (2022) An overview on the generation and detection of synthetic and manipulated satellite images. APSIPA Trans Signal Inf Process 11(1):1–56
Abady L, Dimitri GM, Barni M (2024) A one-class classifier for the detection of gan manipulated multi-spectral satellite images. Remote Sens 16(5):781
Abir WH, Khanam FR, Alam KN, Hadjouni M, Elmannai H, Bourouis S, Dey R, Khan MM (2023) Detecting deepfake images using deep learning techniques and explainable ai methods. Intell Autom Soft Comput 35(2):2151–2169
Ali AM, Abouelghar M, Belal AA, Saleh N, Yones M, Selim AI, Amin ME, Elwesemy A, Kucher DE, Maginan S, Savin I (2022) Crop yield prediction using multi sensors remote sensing. Egypt J Remote Sens Space Sci 25(3):711–716
Alibani M, Acito N, Corsini G (2024) Multispectral satellite image generation using StyleGAN3. IEEE J Sel Top Appl Earth Observ Remote Sens 17:4379–4391
Attia W, Ragab D, Abdel-Hamid AM, Marghani AM, Elfadaly A, Lasaponara R (2022) On the use of radar and optical satellite imagery for the monitoring of flood hazards on heritage sites in Southern Sinai, Egypt. Sustainability 14(9):5500
Bach S, Binder A, Montavon G, Klauschen F, Müller K-R, Samek W (2015) On pixel-wise explanations for non-linear classifier decisions by layer-wise relevance propagation. PLoS One 10(7):e0130140
Bartusiak ER, Yarlagadda SK, Güera D, Bestagini P, Tubaro S, Zhu FM, Delp EJ (2019) Splicing detection and localization in satellite imagery using conditional gans. In: 2019 IEEE conference on multimedia information processing and retrieval (MIPR). IEEE, pp 91–96
Bhagtani K, Yadav AK, Bartusiak ER, Xiang Z, Shao R, Baireddy S, Delp EJ (2022) An overview of recent work in media forensics: methods and threats. arXiv preprint arXiv:2204.12067
Bond-Taylor S, Leach A, Long Y, Willcocks CG (2021) Deep generative modelling: a comparative review of vaes, gans, normalizing flows, energy-based and autoregressive models. IEEE Trans Pattern Anal Mach Intell 44(11):7327–7347
Chen HS, Rouhsedaghat M, Ghani H, Hu S, You S, Kuo CC (2021) Defakehop: a light-weight high-performance deepfake detector. In: 2021 IEEE international conference on multimedia and expo (ICME). IEEE, pp 1–6
Chen HS, Zhang K, Hu S, You S, Kuo CC (2021) Geo-defakehop: high-performance geographic fake image detection. arXiv preprint arXiv:2110.09795
Chen LC, Papandreou G, Schroff F, Adam H (2017) Rethinking atrous convolution for semantic image segmentation. arXiv preprint arXiv:1706.05587
Chen X, Dong C, Ji J, Cao J, Li X (2021) Image manipulation detection by multi-view multi-scale supervision. In: Proceedings of the IEEE/CVF international conference on computer vision, pp 14185–14193
Chollet F (2017) Xception: deep learning with depthwise separable convolutions. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 1251–1258
Demir I, Koperski K, Lindenbaum D, Pang G, Huang J, Basu S, Hughes F, Tuia D, Raskar R (2018) Deepglobe 2018: a challenge to parse the earth through satellite images. In: Proceedings of the IEEE conference on computer vision and pattern recognition workshops, pp 172–181
Dice LR (1945) Measures of the amount of ecologic association between species. Ecology 26(3):297–302
Dinh DB, Ngo DT, Nguyen HD, Nguyen HH, Dang NT (2023) Free satellite image data application for monitoring land use cover changes in the Kon ha Nung Plateau, Vietnam. Heliyon 9:e12864
Dinh L, Krueger D, Bengio Y (2014) Nice: non-linear independent components estimation. arXiv preprint arXiv:1410.8516
Diwan A, Kumar D, Mahadeva R, Perera HC, Alawatugoda J (2023) Unveiling copy-move forgeries: enhancing detection with superpoint keypoint architecture. IEEE Access 11:86132–86148
Dosovitskiy A, Beyer L, Kolesnikov A, Weissenborn D, Zhai X, Unterthiner T, Dehghani M, Minderer M, Heigold G, Gelly S, Uszkoreit J (2020) An image is worth \(16\times 16\) words: transformers for image recognition at scale. arXiv preprint arXiv:2010.11929
Eddy SR (2004) What is a hidden Markov model? Nat Biotechnol 22(10):1315–1316
Fel T, Cadène R, Chalvidal M, Cord M, Vigouroux D, Serre T (2021) Look at the variance! Efficient black-box explanations with sobol-based sensitivity analysis. Adv Neural Inf Process Syst 34:26005–26014
Fezza SA, Ouis MY, Kaddar B, Hamidouche W, Hadid A (2022) Evaluation of pre-trained CNN models for geographic fake image detection. In: 2022 IEEE 24th international workshop on multimedia signal processing (MMSP). IEEE, pp 1–6
Foster T, Mieno T (2020) Satellite-based monitoring of irrigation water use: assessing measurement errors and their implications for agricultural water management policy. Water Resour Res 56(11):e2020WR028378
Freund Y, Haussler D (1991) Unsupervised learning of distributions on binary vectors using two layer networks. Adv Neural Inf Process Syst 4:912–919
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Trans Inf Forens Secur 7(3):868–882
Ghelichkhani S, Salem YA, Salahov H, Adam FA, Charbatji AJ, Abdulkareem MI (2023) Generative adversarial networks for artificial satellite image creation and manipulation. In: Adversarial multimedia forensics. Springer, pp 125–143
Goodfellow I, Bengio Y, Courville A (2016) Deep learning. MIT Press, Cambridge
Hao X, Jian Z, Ni J (2021) A survey of digital image operation forensics. J Signal Process 37(12):15
He K, Zhang X, Ren S, Sun J (2016) Deep residual learning for image recognition. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 770–778
Hinton GE, Salakhutdinov RR (2006) Reducing the dimensionality of data with neural networks. Science 313(5786):504–507
Article MathSciNet Google Scholar
Ho J, Jain A, Abbeel P (2020) Denoising diffusion probabilistic models. Adv Neural Inf Process Syst 33:6840–6851
Horváth J, Baireddy S, Hao H, Montserrat DM, Delp EJ (2021) Manipulation detection in satellite images using vision transformer. In: Proceedings of the IEEE/CVF conference on computer vision and pattern recognition, pp 1032–1041
Horváth J, Güera D, Yarlagadda SK, Bestagini P, Zhu FM, Tubaro S, Delp EJ (2019) Anomaly-based manipulation detection in satellite images. Networks 29(21):62–71
Horváth J, Montserrat DM, Delp EJ, Horváth J (2021) Nested attention u-net: a splicing detection method for satellite images. In: Pattern recognition. ICPR international workshops and challenges: virtual event, January 10–15, 2021, Proceedings, Part VI. Springer, pp 516–529
Horváth J, Montserrat DM, Hao H, Delp EJ (2020) Manipulation detection in satellite images using deep belief networks. In: Proceedings of the IEEE/CVF conference on computer vision and pattern recognition workshops, pp 664–665
Horváth J, Xiang Z, Cannas ED, Bestagini P, Tubaro S, Delp III EJ (2022) Sat u-net: a fusion based method for forensic splicing localization in satellite images. In: Multimodal image exploitation and learning, vol 12100. SPIE, pp 1210002
Karras T, Aila T, Laine S, Lehtinen J (2017) Progressive growing of gans for improved quality, stability, and variation. arXiv preprint arXiv:1710.10196
Karras T, Laine S, Aittala M, Hellsten J, Lehtinen J, Aila T (2020) Analyzing and improving the image quality of stylegan. In: Proceedings of the IEEE/CVF conference on computer vision and pattern recognition, pp 8110–8119
Kaur G, Singh N, Kumar M (2023) Image forgery techniques: a review. Artif Intell Rev 56(2):1577–1625
Lee SI, Park JY, Eom IK (2022) Cnn-based copy-move forgery detection using rotation-invariant wavelet feature. IEEE Access 10:106217–106229
Levandowsky M, Winter D (1971) Distance between sets. Nature 234(5323):34–35
Lewis K, de Barros VF, Cure MB, Davies CA, Furtado MN, Hill TC, Hirota M, Martins DL, Mazzochini GG, Mitchard ET, Munhoz CB (2022) Mapping native and non-native vegetation in the Brazilian Cerrado using freely available satellite products. Sci Rep 12(1):1588
Liu X, Dong X, Xie F, Lu P, Lu X, Jiang M (2024) Hybrid network of convolutional neural network and transformer for deepfake geographic image detection. J Electron Imaging 33(2):023007
Long J, Shelhamer E, Darrell T (2015) Fully convolutional networks for semantic segmentation. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 3431–3440
Lundberg SM, Lee S-I (2017) A unified approach to interpreting model predictions. Adv Neural Inf Process Syst 30:4765–4774
Mansourifar H, Simske SJ (2023) Gan-based object removal in high-resolution satellite images. arXiv preprint arXiv:2301.11726
Mathews S, Trivedi S, House A, Povolny S, Fralick C (2023) An explainable deepfake detection framework on a novel unconstrained dataset. Complex Intell Syst 9(4):4425–4437
McInnes L, Healy J, Melville J (1802) Umap: uniform manifold approximation and projection for dimension reduction. arxiv 2018. arXiv preprint arXiv:1802.03426
Mirza M, Osindero S (2014) Conditional generative adversarial nets. Comput Sci 2672–2680
Mo Y, Wu Y, Yang X, Liu F, Liao Y (2022) Review the state-of-the-art technologies of semantic segmentation based on deep learning. Neurocomputing 493:626–646
Montserrat DM, Horváth J, Yarlagadda SK, Zhu F, Delp EJ (2020) Generative autoregressive ensembles for satellite imagery manipulation detection. In: 2020 IEEE international workshop on information forensics and security (WIFS). IEEE, pp 1–6
Muruganantham P, Wibowo S, Grandhi S, Samrat NH, Islam N (2022) A systematic literature review on crop yield prediction with deep learning and remote sensing. Remote Sens 14(9):1990
Niloy FF, Bhaumik KK, Woo SS (2023) Hrfnet: high-resolution forgery network for localizing satellite image manipulation. In 2023 IEEE International Conference on Image Processing (ICIP), IEEE, pp 3165–3169
Oktay O, Schlemper J, Folgoc LL, Lee M, Heinrich M, Misawa K, Mori K, McDonagh S, Hammerla NY, Kainz B, Glocker B (2018) Attention u-net: learning where to look for the pancreas. arXiv preprint arXiv:1804.03999
Petsiuk V, Das A, Saenko K (2018) Rise: randomized input sampling for explanation of black-box models. arXiv preprint arXiv:1806.07421
Razavi A, Van den Oord A, Vinyals O (2019) Generating diverse high-fidelity images with vq-vae-2. Adv Neural Inf Process Syst 32:14837–14847
Reynolds DA et al (2009) Gaussian mixture models. Encycl Biometr 741:659–663
Ribeiro MT, Singh S, Guestrin C (2016) “Why should I trust you?” Explaining the predictions of any classifier. In: Proceedings of the 22nd ACM SIGKDD international conference on knowledge discovery and data mining, pp 1135–1144
Roerdink JB, Meijster A (2000) The watershed transform: definitions, algorithms and parallelization strategies. Fundam Informat 41(1–2):187–228
Salaria A, Singh A, Sharma KK (2023) A unified approach towards effective forest fire monitoring systems using wireless sensor networks and satellite imagery. In: Artificial intelligence and machine learning in satellite data processing and services: proceedings of the international conference on small satellites, ICSS 2022. Springer, pp 151–161
Samek W, Binder A, Montavon G, Lapuschkin S, Müller KR (2016) Evaluating the visualization of what a deep neural network has learned. IEEE Trans Neural Netw Learn Syst 28(11):2660–2673
Schmitt M, Hughes LH, Qiu C, Zhu XX (2019) Sen12ms—a curated dataset of georeferenced multi-spectral sentinel-1/2 imagery for deep learning and data fusion. arXiv preprint arXiv:1906.07789
Selvaraju RR, Cogswell M, Das A, Vedantam R, Parikh D, Batra D (2017) Grad-cam: visual explanations from deep networks via gradient-based localization. In: Proceedings of the IEEE international conference on computer vision, pp 618–626
Silva SH, Bethany M, Votto AM, Scarff IH, Beebe N, Najafirad P (2022) Deepfake forensics analysis: an explainable hierarchical ensemble of weakly supervised models. Forens Sci Int: Synergy 4:100217
Simonyan K (2014) Very deep convolutional networks for large-scale image recognition. arXiv preprint arXiv:1409.1556
Singh S, Bhardwaj A, Verma VK (2020) Remote sensing and gis based analysis of temporal land use/land cover and water quality changes in Harike wetland ecosystem, Punjab, India. J Environ Manag 262:110355
Szegedy C, Vanhoucke V, Ioffe S, Shlens J, Wojna Z (2016) Rethinking the inception architecture for computer vision. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 2818–2826
Tsigos K, Apostolidis E, Baxevanakis S, Papadopoulos S, Mezaris V (2024) Towards quantitative evaluation of explainable ai methods for deepfake detection. In: Proceedings of the 3rd ACM international workshop on multimedia AI against disinformation, pp 37–45
Van den Oord A, Kalchbrenner N, Espeholt L, Vinyals O, Graves A (2016) Conditional image generation with pixelcnn decoders. Adv Neural Inf Process Syst 29:4790–4798
Van Den Oord A, Kalchbrenner N, Kavukcuoglu K (2016) Pixel recurrent neural networks. In: International conference on machine learning. PMLR, pp 1747–1756
Van Den Oord A, Vinyals O (2017) Neural discrete representation learning. Adv Neural Inf Process Syst 30:6306–6315
Verma M, Singh D (2024) Survey on image copy-move forgery detection. Multimedia Tools Appl 83(8):23761–23797
Wang Y, Wong J, Miner A (2004) Anomaly intrusion detection using one class SVM. In: Proceedings from the 5th annual IEEE SMC information assurance workshop. IEEE, pp 358–364
Yarlagadda SK, Güera D, Bestagini P, Zhu FM, Tubaro S, Delp EJ (2018) Satellite image forgery detection and localization using gan and one-class classifier. arXiv preprint arXiv:1802.04881
Yates M, Hart G, Houghton R, Torres MT, Pound M (2022) Evaluation of synthetic aerial imagery using unconditional generative adversarial networks. ISPRS J Photogram Remote Sens 190:231–251
Ying X, Raja K, Pedersen M (2022) Supervised contrastive learning for generalizable and explainable deepfakes detection. In: Proceedings of the IEEE/CVF winter conference on applications of computer vision, pp 379–389
Zenghui Z, Wenxian Y (2016) Feature understanding and target detection for sparse microwave synthetic aperture radar images. J Radars 5(1):42–56
Zhao B, Zhang S, Xu C, Sun Y, Deng C (2021) Deep fake geography? When geospatial data encounter artificial intelligence. Cartogr Geogr Inf Sci 48(4):338–352
Zhou Z-H (2021) Machine learning. Springer Nature
Zhou Z, Rahman Siddiquee MM, Tajbakhsh N, Liang J (2018) Unet++: a nested u-net architecture for medical image segmentation. In: Deep learning in medical image analysis and multimodal learning for clinical decision support: 4th international workshop, DLMIA 2018, and 8th international workshop, ML-CDS 2018, held in conjunction with MICCAI 2018, Granada, Spain, September 20, 2018, proceedings 4, 3–11. Springer
Zhu JY, Park T, Isola P, Efros AA (2017) Unpaired image-to-image translation using cycle-consistent adversarial networks. In: Proceedings of the IEEE international conference on computer vision, pp 2223–2232
Download references
Acknowledgements
This research is supported in part by the National Natural Science Foundation of China (62272160), the Research Foundation of the Department of Natural Resources of Hunan Province (No. HBZ20240107), the Opening Project of Liaoning Collaboration Innovation Center For CSLE (No. XTCX2024-004) and the Scientific Research Foundation of Hunan Provincial Education Department of China (No. 23A0377).
Author information
Authors and affiliations.
School of Computer Science and Engineering, Hunan University of Science and Technology, Xiangtan, 411201, China
Xiangling Ding, Yuchen Nie, Jizhou Yao & Jia Tang
Liaoning Collaboration Innovation Center For CSLE, Shenyang, 110854, China
Xiangling Ding & Yubo Lang
College of Information Technology and Intelligence, Criminal Investigation Police University of China, Shenyang, 110854, China
You can also search for this author in PubMed Google Scholar
Contributions
X. Ding: Conceptualization, Funding Acquisition, Writing—Review & Editing, Supervision; Y. Nie: Data duration, Methodology, Writing—Original draft preparation, Software; J. Yao: Visualization, Investigation; J. Tang: Software, Validation; Y. Lang: Writing-Review; All authors reviewed the manuscript.
Corresponding author
Correspondence to Xiangling Ding .
Ethics declarations
Conflict of interest.
The authors declare no Conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License, which permits any non-commercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this article or parts of it. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by-nc-nd/4.0/ .
Reprints and permissions
About this article
Ding, X., Nie, Y., Yao, J. et al. Forensic research of satellite images forgery: a comprehensive survey. Artif Intell Rev 57 , 253 (2024). https://doi.org/10.1007/s10462-024-10909-w
Download citation
Accepted : 06 August 2024
Published : 14 August 2024
DOI : https://doi.org/10.1007/s10462-024-10909-w
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Satellite image forgery
- Satellite image forensics
- Tampering detection
- Tampering localization
- Find a journal
- Publish with us
- Track your research
In this blog, you’ll find some of the top macroeconomic research Paper topics for 2024. Grasping macroeconomics enables you to understand the workings of national and global economies. Let’s delve into this subject-oriented essay topic blog to explore what macroeconomics is and why it is crucial for your research.
What is Macroeconomics? Definition and Scope
Macroeconomics focuses on broad economic factors such as national income, total employment, and aggregate price levels. It explores how different sectors of the economy interact on a large scale. The discussion could be on anything, including government policies, international trade, and global financial systems.
Macroeconomics studies the economy broadly, concentrating on aspects like GDP, inflation rates, and unemployment, whereas microeconomics zeroes in on individual and business decisions. Macroeconomics addresses large-scale economic factors, while microeconomics explores supply and demand, consumer behavior, and pricing more granularly. Macroeconomics centralizes its attention on broader aspects, while microeconomics focuses on specific topics. Both perspectives offer valuable insights but from distinct viewpoints.
3 Primary Objectives of Macroeconomics
1. Economic Growth: As a primary objective, economic growth aims to increase the output of goods and services in an economy over time. Sustained economic growth improves living standards, creates job opportunities, and boosts national income. It also empowers governments with more resources to invest in public services and infrastructure.
2. Inflation: Inflation control is a key objective in macroeconomics, focusing on maintaining price stability within an economy. By managing inflation, governments and central banks aim to ensure that prices do not rise too quickly, which can erode purchasing power. Effective inflation control supports economic stability and promotes sustainable growth.
3. Unemployment: Reducing unemployment is a central goal. It aims to balance job availability. High employment levels contribute to economic stability and growth by maximizing the productive capacity of the workforce. Policymakers focus on creating job prospects and enhancing skills to address unemployment and support a healthy economy.
Importance of Studying Macroeconomics
Macroeconomics offers a comprehensive view of economic health and guides effective policy implementation. Understanding these concepts is essential for grasping the complexities of both national and global economies. Studying macroeconomics is crucial for several reasons. See the following to know them:
Informed Policy Making : Understanding macroeconomic principles helps policymakers design effective strategies to manage economic growth, control inflation, and reduce unemployment. This knowledge is vital for creating policies that stabilize and stimulate the economy.
Economic Forecasting : Macroeconomics provides tools for predicting future economic trends and conditions. Accurate forecasts can guide business decisions, investments, and financial planning, helping both individuals and organizations prepare for potential economic changes.
Global Economic Understanding : Macroeconomics analyzes global economic interactions and trade to help understand the impact of international events on national economies. This knowledge is essential for navigating and responding to global economic challenges.
Economic Stability and Growth : Studying macroeconomics helps understand the factors contributing to economic stability and growth. This insight is crucial for developing strategies to effectively promote sustainable economic development and manage economic fluctuations.
How to Select a Good Macroeconomics Research Topic?
Identify areas of interest :.
Begin by considering what aspects of macroeconomics capture your interest. Are you intrigued by the impact of government policies on economic performance, or are you interested in the effects of international trade? Selecting a topic that genuinely excites you will make the research process more enjoyable and engaging. For instance, if you have a passion for environmental issues, you might investigate the economic implications of climate change policies.
Review Current Literature :
Reviewing current literature is crucial for selecting a good macroeconomic research topic. It helps you understand existing research trends, identify gaps in knowledge, and spot areas where further investigation is needed. Reviewing recent studies, theories, and findings helps pinpoint unresolved issues or underexplored areas, aligning your interests and having the potential for impactful research. It ensures your topic is both relevant and original, contributing to the broader field of macroeconomics.
Look for Gaps in Existing Research
After pinpointing your area of interest, review existing research to identify gaps. Are there unresolved questions or areas with contradictory results? Addressing these gaps can lead to a distinctive and influential research paper. For example, if most studies focus on the impact of fiscal policy on economic growth but overlook its effects during economic downturns, exploring this angle could provide valuable insights.
Consider Practical Relevance, Impact & Timeliness :
A topic with practical relevance addresses real-world economic issues, influencing policy decisions, business strategies, or societal outcomes. Evaluating the impact ensures that your research can contribute meaningful insights or solutions to pressing economic challenges. Timeliness reflects current economic trends, making your research more pertinent to audiences. This approach makes your work academically rigorous, applicable, and influential.
Evaluate Data and Resource Feasibility:
Ensure you have access to reliable and comprehensive data sources like economic reports, statistical databases, and scholarly articles necessary for your analysis. Consider whether you have the tools and skills required to analyze this data effectively. Assessing the feasibility involves determining if you can realistically obtain and utilize the necessary data within your research timeline and constraints. It ensures that your research is thoroughly and effectively conducted, leading to credible and insightful results.
Define Clear Objectives :
Start by outlining what you aim to discover or prove through your research. This could be anything from understanding the impact of monetary policy on inflation to evaluating the effects of trade tariffs on economic growth. Articulated objectives guide your focus, narrow your topic, and keep your research relevant. This clarity streamlines the research process, enhancing your findings’ quality and coherence. It also facilitates the communication of your findings.
Top Macroeconomics Research Topics in 2024
1. Why Do We Dislike Inflation?- This paper answers Shiller’s (1997) question: Why do we dislike inflation? It explores the primary reasons behind people’s aversion to inflation and includes surveys to learn people’s perceptions of inflation, its impacts, and reactions.
2. Recent Developments in Financial Risk and the Real Economy— In this topic, you can review recent developments in macro and finance. You can also highlight the relationship between financial risk and the real economy through subtopics and surveys.
3. The Effects of Macroeconomic Policies on Housing Markets— Discuss macroeconomic policies influencing housing markets. You can explain interest rates’ impact on house affordability and changes in demand. Include studies that show how Fiscal policies drive market behavior.
4. Comparative Analysis: Great Depression & Great Recession— You can state how the Great Depression and the Great Recession offer valuable insights into economic crises. It compares these two significant events’ causes, government responses, and recovery processes.
5. Government Responses to Unemployment— You can discuss diverse employment strategies of Governments to combat unemployment, particularly during economic downturns. Explore the effectiveness of different approaches and analyze case studies for better understanding.
6. Impact of Foreign Direct Investment on Economic Growth— Review how FDI influences growth in various sectors. You could analyze relevant case studies to clearly reflect the causes and explain how these have significant impacts on the economic growth of different countries.
7. The Relationship Between GDP and Unemployment— You can discuss the relationship between the Gross Domestic Product and unemployment. Explain why these two are often inversely proportional and how GDP changes influence unemployment rates across different sectors.
8. Pros and Cons of the US Economy— Researching this topic allows students to delve into various facets of the US economy. Students can explain the complex economic system along with its strengths and weaknesses, helping them develop a balanced view of the US economy.
9. The Impact of Globalization on Modern Economies— This research paper will discuss globalization and its impact on worldwide economics. With case studies, you can support the research related to the transformation of modern economics under the influence of globalization.
10. Comparative Study of Capitalism and Socialism— You can analyze various countries’ fundamental principles, historical implementations, and outcomes to offer insights into Capitalism and Socialism. Talk about the advantages and disadvantages of each system with diverse approaches.
11. Historical Analysis of the British Industrial Revolution— Researching it involves exploring the long-term effects of industrialization on economic development in different classes. You can discuss the shift from agrarian economies to industrial ones, the rise of urbanization, and social impacts.
12. Solutions to the Child Labor Problem— Research historical and contemporary efforts to combat this problem. Explore legal frameworks and economic incentives for families. Understanding the causes and effective interventions allows the development of a comprehensive strategy to address the issue.
13. Supply Chain Constraints and Inflation— You can evaluate how potential supply chain capacity constraints shape inflation. Adding case studies, models, and relevant data explains how this constraint impacts increased demand or capacity reductions related to reasons for inflation.
14. Modern Infectious Diseases: Macroeconomic Impacts and Policy Responses— Discuss standard frameworks for assessing the economic burden of infectious diseases and how to prevent their macroeconomic repercussions. You can also review the health toll and economic impacts of infectious diseases.
15. Foreign Demand Shocks to Production Networks: Firm Responses and Worker Impacts— Explain how firms respond to foreign demand shocks within domestic production networks and assess the impacts on workers. Analyze how specific and overall changes in foreign demand spread through a small open economy, affecting firms and workers.
16. Discrete-Choice Models and Representative Consumer Theory— Explores how individuals make decisions based on limited options and how these choices can be aggregated to reflect market behavior. Delve into the mathematical modeling of individual preferences and the simplification of complex market dynamics into a single representative consumer framework.
17. The Debt Capacity of a Government— Investigate the maximum amount of debt a government can sustain without compromising its financial stability or economic growth. Explore economic indicators, fiscal policies, and external economic conditions to assess the limits of sustainable borrowing.
18. Simulating Endogenous Global Automation— Review the impacts of automation driven by internal economic factors on a global scale. See simulation models to analyze how advancements in automation technology affect labor markets, economic growth, and international trade dynamics.
19. Can Monetary Policy Create Fiscal Capacity?— It explores the relationship between monetary policy actions and a government’s ability to finance its expenditures. You can investigate how central bank policies might enhance a government’s fiscal space and impact economic stability.
20. Welfare and Output with Income Effects and Taste Shocks— Study how changes in income levels and consumer preferences impact overall economic welfare and production. It also analyzes the interplay between economic output, individual well-being, and shifts in consumer tastes, providing insights into the broader effects of economic fluctuations and policy interventions.
21. Market Power in Neoclassical Growth Models— Market power in neoclassical growth models refers to the ability of firms to influence prices and wages due to a lack of perfect competition. Here, I have discussed how this power can lead to deviations from the optimal allocation of resources, potentially affecting long-term economic growth and income distribution within the model.
22. The Macroeconomics of Financial Speculation— This topic reviews how speculative activities in financial markets impact economic variables like investment, consumption, and growth. It explores the potential for speculative bubbles, market volatility, and systemic risks. It analyzes their effects on economic stability and policy responses.
23. The Economics of Walking About and Predicting US Downturns— The economics of walking about involves gathering informal, on-the-ground observations to predict economic downturns in the US. Discuss the traditional economic indicators by capturing real-time business and consumer sentiment, offering early signals of potential recessions.
24. A New Way of Forecasting Recessions— It proposes a new way of displaying and analyzing macroeconomic time series to form recession forecasts. You can use different models & recent data to analyze diverse aspects, including market variables, to predict recessions.
25. Inclusive Monetary Policy: How Tight Labor Markets Facilitate Broad-Based Employment Growth— Inclusive monetary policy fosters tight labor markets, which help drive broad-based employment growth across diverse demographic groups. We discuss how maintaining low unemployment rates and such policies can reduce disparities in job opportunities and support economic inclusivity.
Our Trending Services >> Homework Help | Assignment Help | Live Sessions | Do My Homework | Do My Essay | Write My Essay | Essay Writing Help | Lab Report Help | Project Report Help | Speech Writing Service | Presentation Writing Service | Video Solutions | Pay Someone To Do My Homework | Help With Writing My Paper | Writing Service For Research Paper | Paying Someone To Write Your Paper
Our Popular Subjects >> Math Homework Help | Physics Homework Help | Chemistry Homework Help | Civil Engineering Homework Help | Finance Homework Help | Electrical Engineering Homework Help | Mechanical Engineering Homework Help | Computer Science Homework Help | Economics Homework Help | Calculus Homework Help | Fluid Mechanics Homework Help
- E- Learning
- Online Learning
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked*
Comment * NEXT
Save my name and email in this browser for the next time I comment.
You May Also Like

How to Write a Survey Paper: Guidance From Experts

How to Write a Sociology Research Paper- Expert Guidance with Template

25 Career Scope For You With a Computer Science Degree

Will Computer Science Careers in the Job Market Become Saturated Soon?

Expert Guide on How to Write an Analytical Essay
Online homework help, get homework help.
Get Answer within 15-30 minutes

Check out our free tool Math Problem Solver
About tutorbin, what do we do.
We offer an array of online homework help and other services for our students and tutors to choose from based on their needs and expertise. As an integrated platform for both tutors and students, we provide real time sessions, online assignment and homework help and project work assistance.

Who are we?
TutorBin is an integrated online homework help and tutoring platform serving as a one stop solution for students and online tutors. Students benefit from the experience and domain knowledge of global subject matter experts.

IMAGES
COMMENTS
Definition: Research Paper is a written document that presents the author's original research, analysis, and interpretation of a specific topic or issue. It is typically based on Empirical Evidence, and may involve qualitative or quantitative research methods, or a combination of both. The purpose of a research paper is to contribute new ...
Definition. A research paper is a paper that makes an argument about a topic based on research and analysis. Any paper requiring the writer to research a particular topic is a research paper. Unlike essays, which are often based largely on opinion and are written from the author's point of view, research papers are based in fact.
A research paper is a piece of academic writing that provides analysis, interpretation, and argument based on in-depth independent research. Research papers are similar to academic essays, but they are usually longer and more detailed assignments, designed to assess not only your writing skills but also your skills in scholarly research ...
What is a research paper? A research paper is a type of academic writing that provides an in-depth analysis, evaluation, or interpretation of a single topic, based on empirical evidence. Research papers are similar to analytical essays, except that research papers emphasize the use of statistical data and preexisting research, along with a strict code for citations.
A research paper is a common form of academic writing. Research papers require students and academics to locate information about a topic (that is, to conduct research ), take a stand on that topic, and provide support (or evidence) for that position in an organized report. The term research paper may also refer to a scholarly article that ...
Table of contents. Step 1: Introduce your topic. Step 2: Describe the background. Step 3: Establish your research problem. Step 4: Specify your objective (s) Step 5: Map out your paper. Research paper introduction examples. Frequently asked questions about the research paper introduction.
1. Choose your topic. Choose a topic that interests you. Writing your research paper will be so much more pleasant with a topic that you actually want to know more about. Your interest will show in the way you write and effort you put into the paper. Consider these issues when coming up with a topic:
A research paper is an expanded essay that presents your own interpretation or evaluation or argument. When you write an essay, you use everything that you personally know and have thought about a subject. When you write a research paper you build upon what you know about the subject and make a deliberate attempt to find out what experts know.
Experimental research paper. This type of research paper basically describes a particular experiment in detail. It is common in fields like: biology. chemistry. physics. Experiments are aimed to explain a certain outcome or phenomenon with certain actions. You need to describe your experiment with supporting data and then analyze it sufficiently.
Research Paper. A research paper is a product of seeking information, analysis, human thinking, and time. Basically, when scholars want to get answers to questions, they start to search for information to expand, use, approve, or deny findings. In simple words, research papers are results of processes by considering writing works and following ...
The introduction leads the reader from a general subject area to a particular topic of inquiry. It establishes the scope, context, and significance of the research being conducted by summarizing current understanding and background information about the topic, stating the purpose of the work in the form of the research problem supported by a hypothesis or a set of questions, explaining briefly ...
The pages in this section cover the following topic areas related to the process of writing a research paper: Genre - This section will provide an overview for understanding the difference between an analytical and argumentative research paper. Choosing a Topic - This section will guide the student through the process of choosing topics ...
Research results can be presented in a variety of ways, but one of the most popular—and effective—presentation forms is the research paper. A research paper presents an original thesis, or purpose statement, about a topic and develops that thesis with information gathered from a variety of sources.
Research: What it is. A research paper is the culmination and final product of an involved process of research, critical thinking, source evaluation, organization, and composition. It is, perhaps, helpful to think of the research paper as a living thing, which grows and changes as the student explores, interprets, and evaluates sources related ...
Each of these examples is specific enough that we already have a sense of what the paper might discuss, but simple enough for most readers to quickly understand. Try one of the following to catch the reader's eye: • An eye-catching, startling fact or statistic. • An interesting or provocative question • A definition of a key term or concept
Definition paper. Experimental paper. Interpretative paper. Survey paper. Let us understand each type of research paper in detail. 1. Analytical Research Paper. While writing an analytical paper, the student asks a question, collects relevant data from a variety of sources, and analyzes it. The findings, viewpoints, and conclusions presented in ...
Grey Literature-- research produced by organizations outside of commercial and academic publishing that publish materials, such as, working papers, research reports, and briefing papers. Grounded Theory-- practice of developing other theories that emerge from observing a group. Theories are grounded in the group's observable experiences, but ...
Research paper introduction is the first section of a research paper that provides an overview of the study, its purpose, and the research question (s) or hypothesis (es) being investigated. It typically includes background information about the topic, a review of previous research in the field, and a statement of the research objectives.
Although research paper assignments may vary widely, there are essentially two basic types of research papers. These are argumentative and analytical.. Argumentative. In an argumentative research paper, a student both states the topic they will be exploring and immediately establishes the position they will argue regarding that topic in a thesis statement.
A research paper is an academic requirement provided by students which focuses on a particular topic and includes thorough data analyses, objective, and personal interpretation. A thesis is a dissertation that provides a theory or idea based on intensive research and is discussed in a logical manner.
The discussion section is often considered the most important part of your research paper because it: Most effectively demonstrates your ability as a researcher to think critically about an issue, to develop creative solutions to problems based upon a logical synthesis of the findings, and to formulate a deeper, more profound understanding of the research problem under investigation;
themselves constitute a research paper. The following pages describe the major components and standards of a research paper, and provide tips on how to write a good research paper. The last page is a sample checklist for grading a research paper. 1) MAKE AN ARGUMENT The main objective of a research paper is to use academic theories, accepted
Research methods are specific procedures for collecting and analyzing data. Developing your research methods is an integral part of your research design. When planning your methods, there are two key decisions you will make. First, decide how you will collect data. Your methods depend on what type of data you need to answer your research question:
For a professional paper, the affiliation is the institution at which the research was conducted. Include both the name of any department and the name of the college, university, or other institution, separated by a comma. Center the affiliation on the next double-spaced line after the author names; when there are multiple affiliations, center ...
Implementing Retrieval-Augmented Generation (RAG) systems is inherently complex, requiring deep understanding of data, use cases, and intricate design decisions. Additionally, evaluating these systems presents significant challenges, necessitating assessment of both retrieval accuracy and generative quality through a multi-faceted approach. We introduce RAG Foundry, an open-source framework ...
This paper aims to fill this gap and investigates recent advances in satellite image forensics, focusing on tampering strategies and forensic methodologies. First, we discuss the concept of satellite images, the definition of satellite image forgery from global and local perspectives, and the datasets commonly used for satellite image forensics.
9. The Impact of Globalization on Modern Economies—This research paper will discuss globalization and its impact on worldwide economics. With case studies, you can support the research related to the transformation of modern economics under the influence of globalization. 10.